| 일 | 월 | 화 | 수 | 목 | 금 | 토 |
|---|---|---|---|---|---|---|
| 1 | 2 | 3 | ||||
| 4 | 5 | 6 | 7 | 8 | 9 | 10 |
| 11 | 12 | 13 | 14 | 15 | 16 | 17 |
| 18 | 19 | 20 | 21 | 22 | 23 | 24 |
| 25 | 26 | 27 | 28 | 29 | 30 | 31 |
- Burp Suite: Intruder
- TryHackMe
- CTFS
- burp suite
- Walkthrough
- Burp Suite: Other Modules
- Windows Forensics 1
- ctf
- advent of cyber 3
- Intruder
- Today
- Total
root@sky:~#
[Day 9] Advent of Cyber 3 (2021) | TryHackMe 본문


Networking
Where Is All This Data Going
Story
McSkidy recently found out that a large amount of traffic is entering one system on the network. Use your traffic analysis skills to determine what kind of activities Grinch Enterprises are performing.
Answer the questions below
Q.) In the HTTP #1 - GET requests section, which directory is found on the webserver?
A.) login
Process:- Download the task fine and open Wireshark.
You can also use THM attack box.


http.request.method == GET
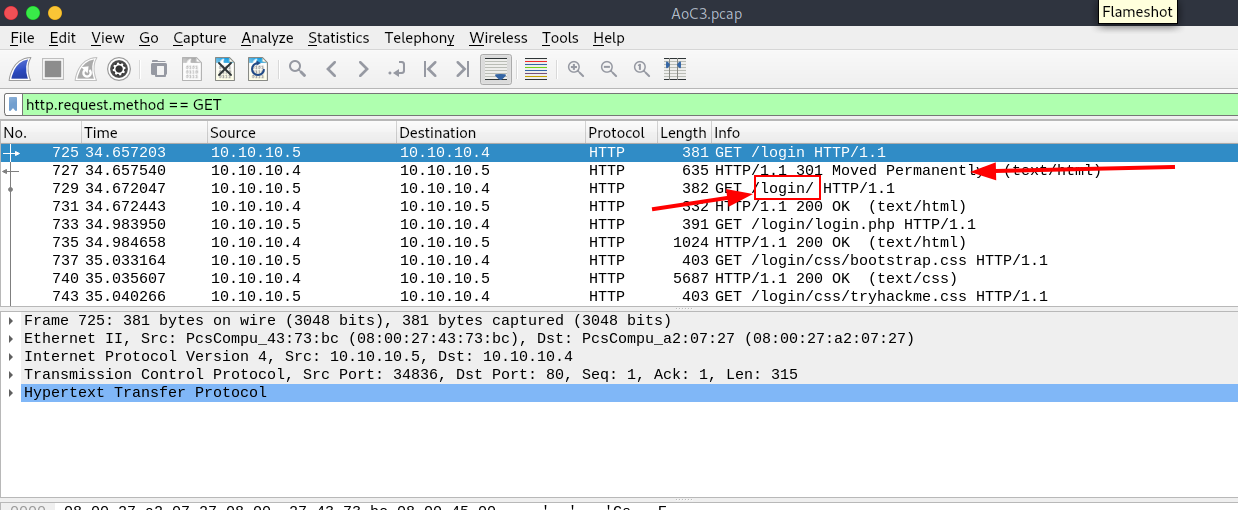
" in filter box and press enter.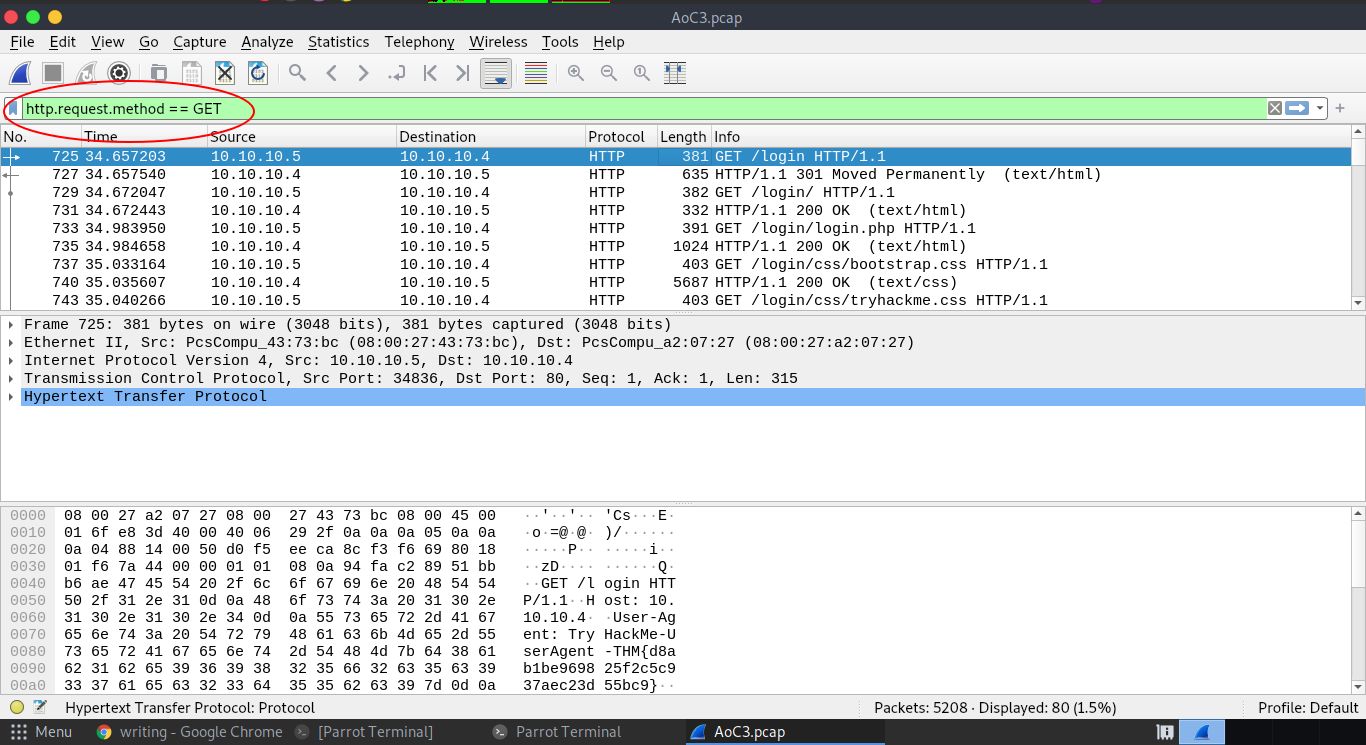
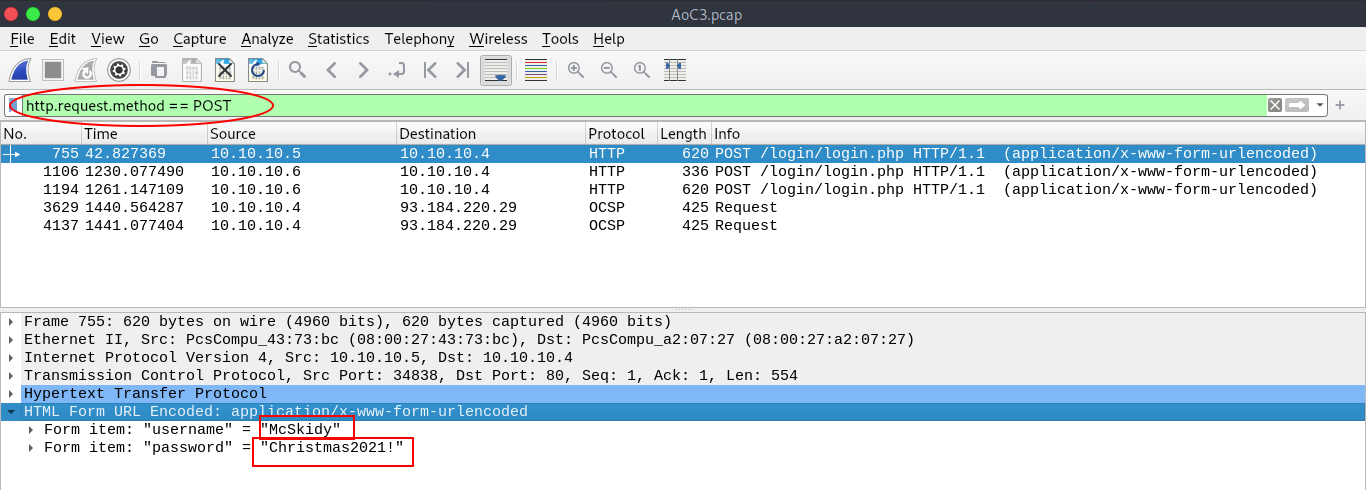
Q.) What is the username and password used in the login page in the HTTP #2 - POST section?
A.) McSkidy: Christmas 2021!
Process:- To look at the POST requests, change the filter to " http.request.method == POST ".
In the first POST request, you can see the username and password.
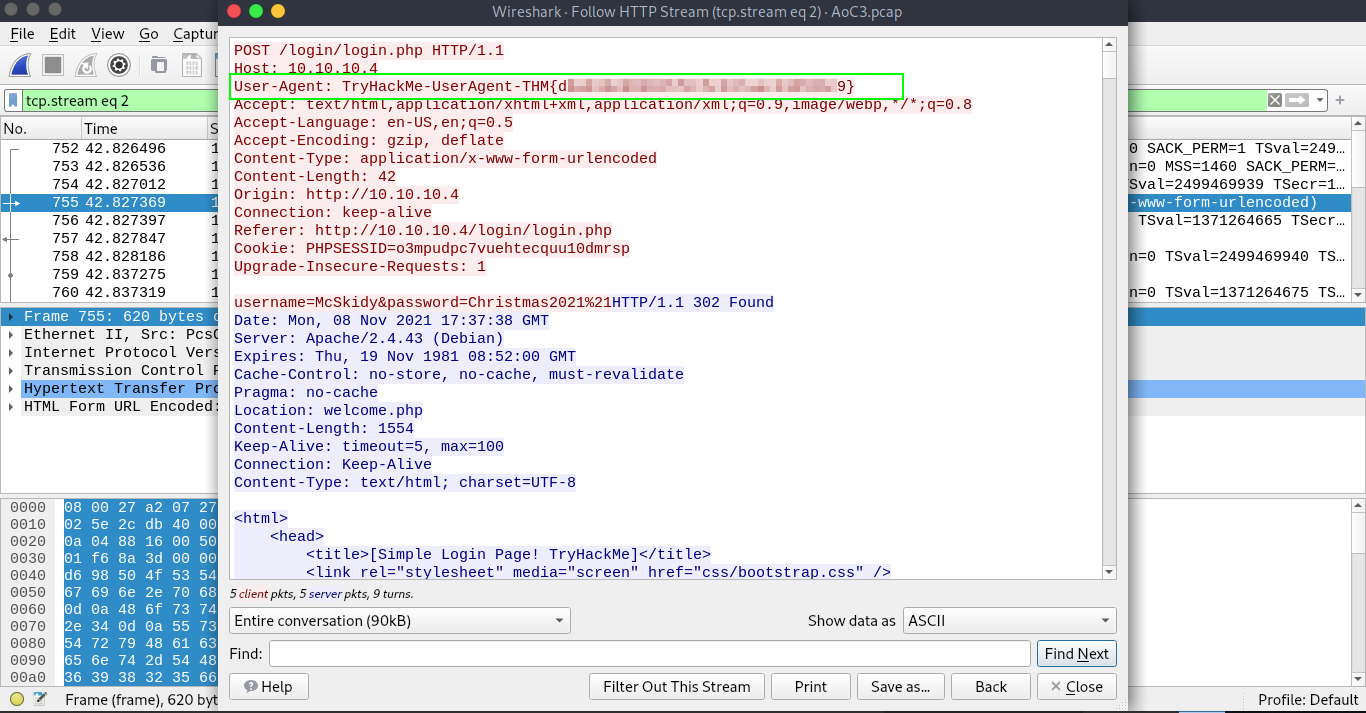
Q.) What is the User-Agent's name that has been sent in HTTP #2 - POST section?
A.) TryHackMe-UserAgent-THM{dXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX9}
Process:- To look the User-Agent, Just right click on the POST request and go to Follow>HTTP Stream or press Ctrl+Alt+Shift+H.
Q.) In the DNS section, there is a TXT DNS query. What is the flag in the message of that DNS query?
A.) THM{dXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX7}
Process:- To look at all the DNS, Just type DNS in the filter.
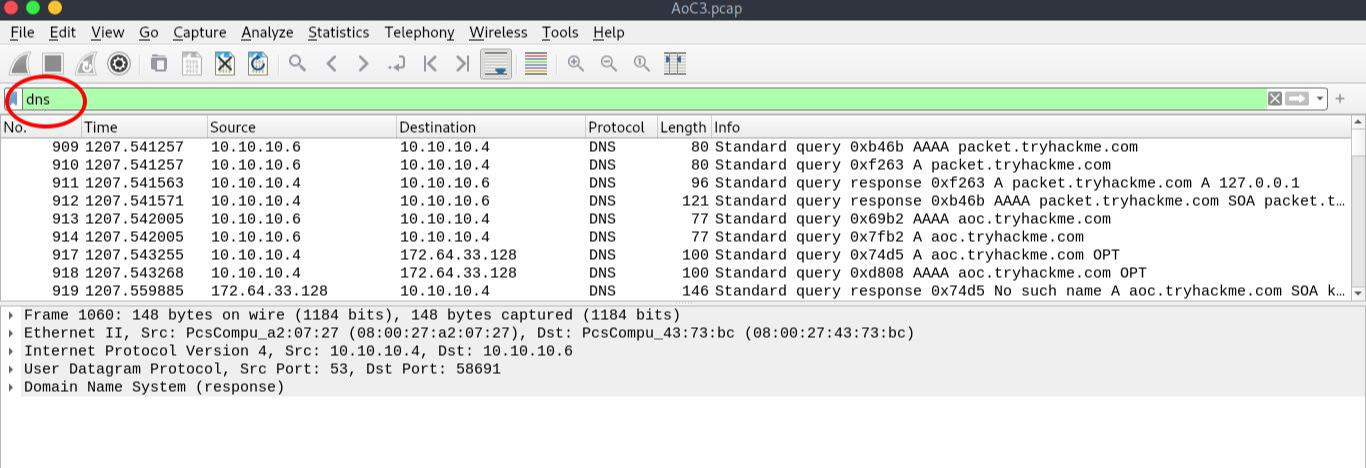
Now scroll down and find the TXT DNS query.
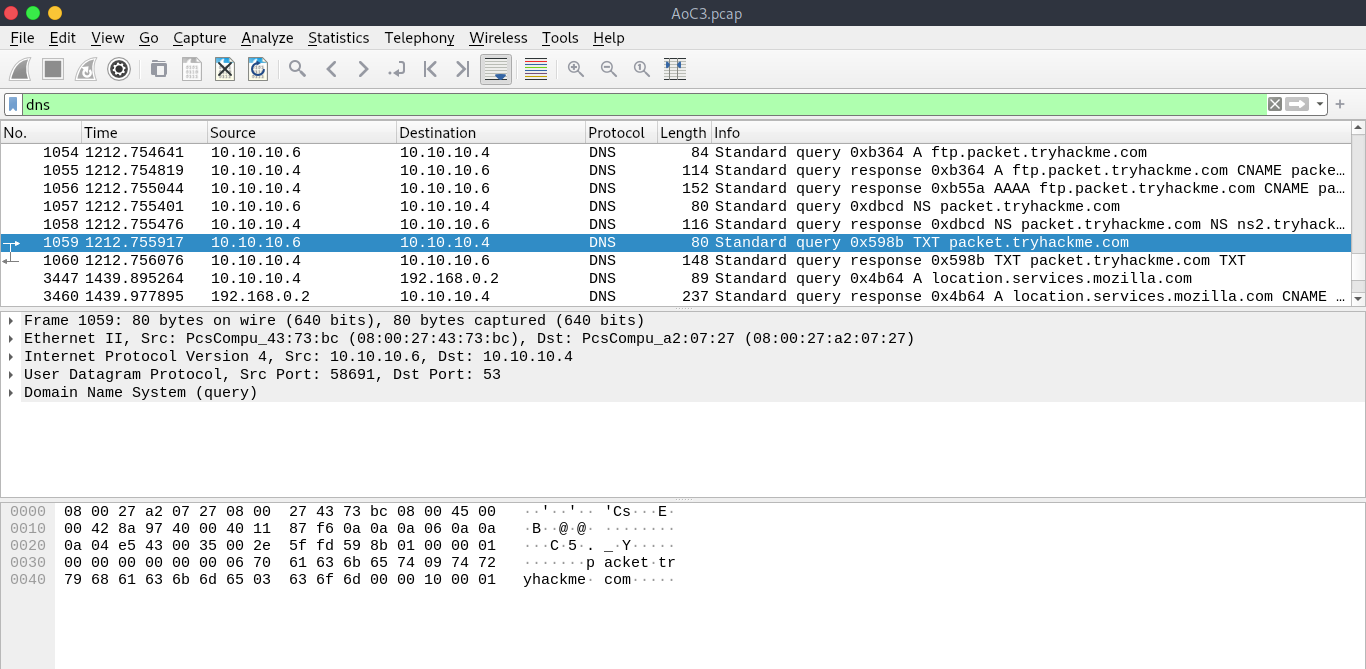
I got the TXT DNS query at number 1059.
Now right click on the DNS query and go to Follow>UDP Stream or press Ctrl+Alt+Shift+U.
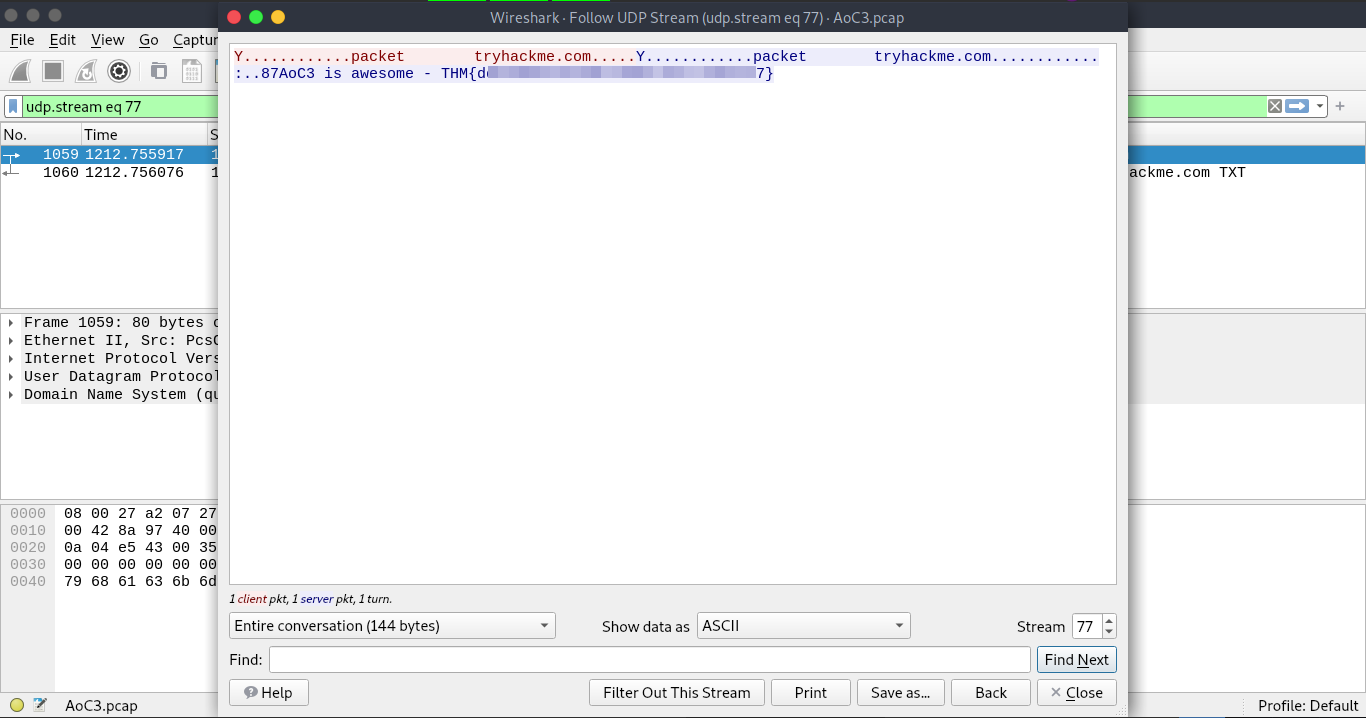
And got the flag.
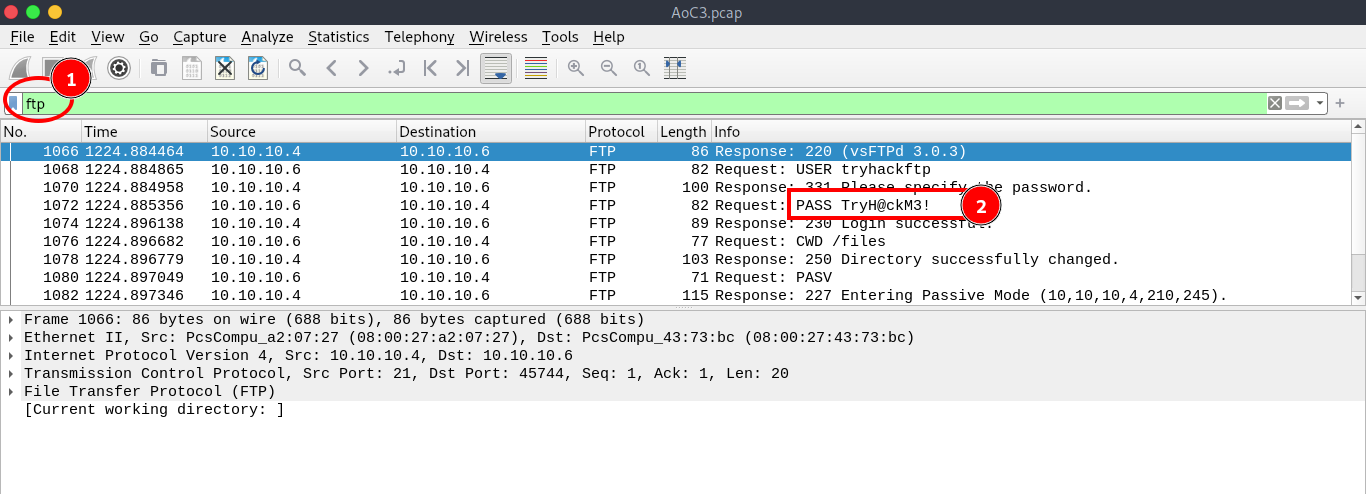
Q.) In the FTP section, what is the FTP login password?
A.) TryH@ckM3!
Process:- To look at FTP, type ftp in the filter and press enter.
Q.) In the FTP section, what is the FTP command used to upload the secret.txt file?
A.) STOR
Process:- To look at FTP data, type ftp-data in the filter.

Here, you can see the STOR command used to upload secret.txt.
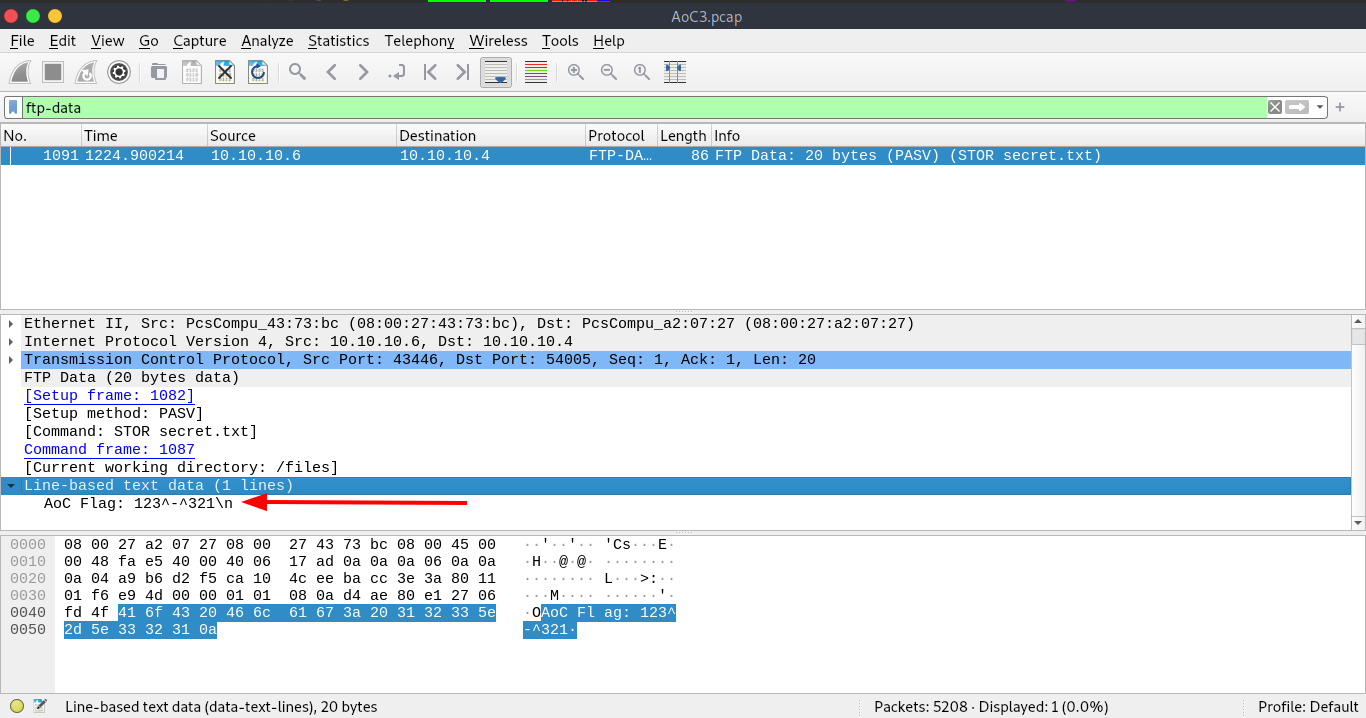
Q.) In the FTP section, what is the content of the secret.txt file?
A.) 123^-^321
Process:- Look down in Line-based text data and you'll get the content of the secret.txt file.
Thanks for reading.
Have a romantic day ;-)

'CTFs > TryHackMe' 카테고리의 다른 글
| [Day 11] Advent of Cyber 3 (2021) | TryHackMe (0) | 2021.12.22 |
|---|---|
| [Day 10] Advent of Cyber 3 (2021) | TryHackMe (0) | 2021.12.17 |
| [Day 8] Advent of Cyber 3 (2021) | TryHackMe (0) | 2021.12.17 |
| [Day 7] Advent of Cyber 3 (2021) | TryHackMe (0) | 2021.12.16 |
| [Day 6] Advent of Cyber 3 (2021) | TryHackMe (0) | 2021.12.16 |





