| 일 | 월 | 화 | 수 | 목 | 금 | 토 |
|---|---|---|---|---|---|---|
| 1 | 2 | 3 | 4 | 5 | ||
| 6 | 7 | 8 | 9 | 10 | 11 | 12 |
| 13 | 14 | 15 | 16 | 17 | 18 | 19 |
| 20 | 21 | 22 | 23 | 24 | 25 | 26 |
| 27 | 28 | 29 | 30 |
- ctf
- Intruder
- CTFS
- Burp Suite: Intruder
- Walkthrough
- advent of cyber 3
- Burp Suite: Other Modules
- burp suite
- TryHackMe
- Windows Forensics 1
- Today
- Total
root@sky:~#
[Day 10] Advent of Cyber 3 (2021) | TryHackMe 본문


Networking
Offensive Is The Best Defence
Story
McSkidy is trying to discover how the attackers managed to penetrate the network and cause damage to the Best Festival Company’s infrastructure. She decided to start doing a security assessment of her systems to discover how Grinch Enterprises managed to cause this damage. She started by conducting a security assessment of her systems to discover how Grinch Enterprises managed to cause this damage and wonders what service they exploited.

Answer the questions below
Q.) Help McSkidy and run nmap -sT MACHINE_IP. How many ports are open between 1 and 100?
A.) 2
Process:- Do a nmap scan.
nmap -sT 10.10.219.54
Q.) What is the smallest port number that is open?
A.) 22
Process:- As you can see in nmap output, the smallest open port is 22.
Q.) What is the service related to the highest port number you found in the first question?
A.) HTTP
Process:- As you can see in nmap output, the highest port number(80) is running http.
Q.) Now run nmap -sS 10.10.219.54. Did you get the same results? (Y/N)
A.) Y
Process:- Run the nmap command and check if it's same as previous result.
sudo nmap -sS 10.10.219.54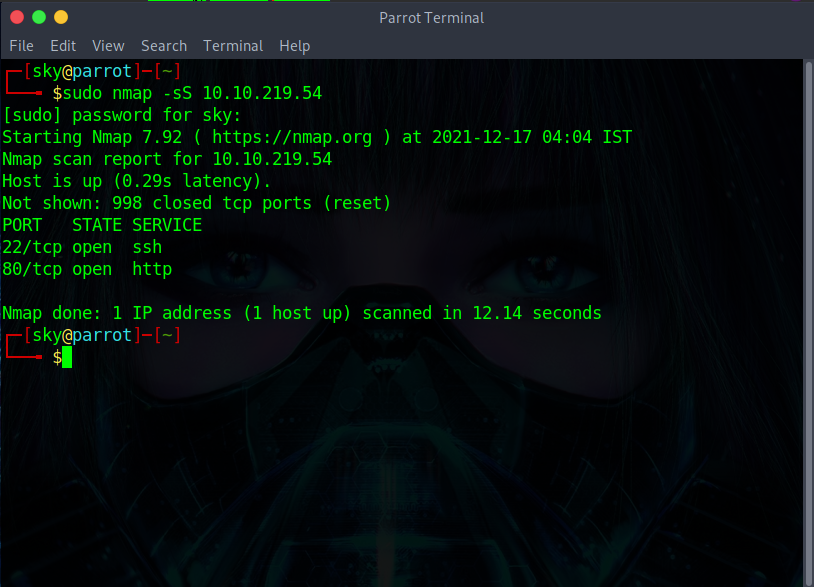
Yes, got the same result.
Q.) If you want Nmap to detect the version info of the services installed, you can use nmap -sV 10.10.219.54. What is the version number of the webserver?
A.) Apache httpd 2.4.49
Process:- Run the nmap command and check the webserver version.
nmap -sV 10.10.219.54
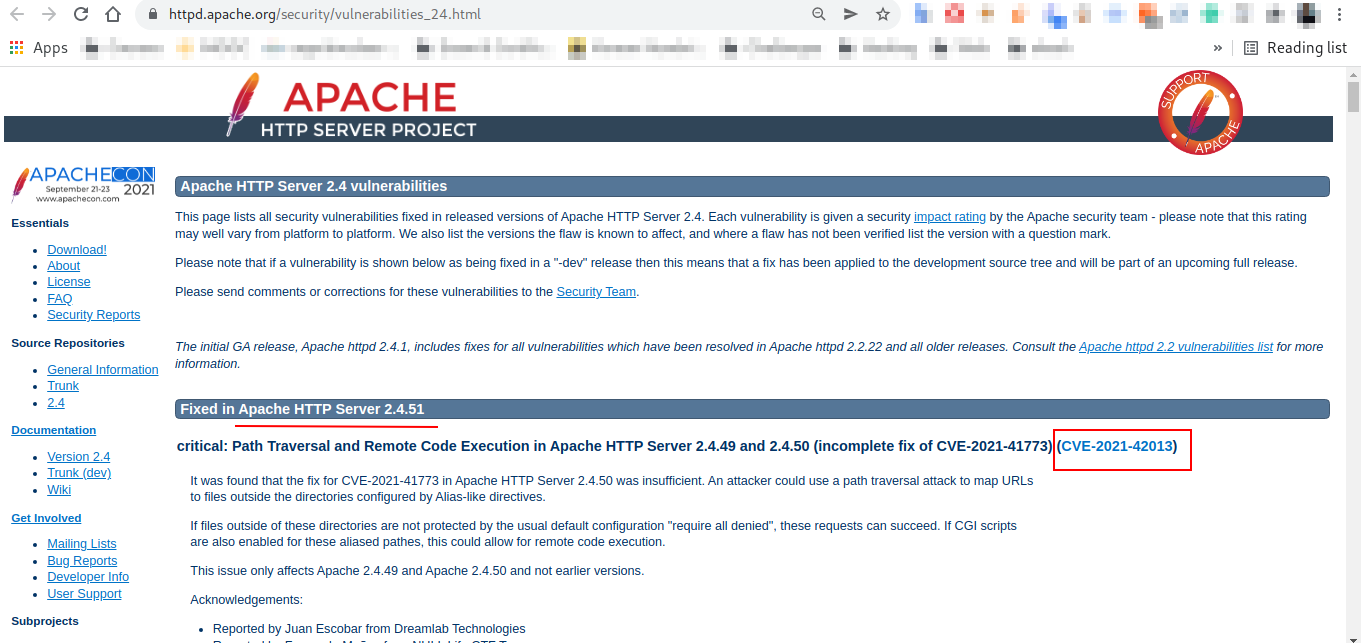
Q.) By checking the vulnerabilities related to the installed web server, you learn that there is a critical vulnerability that allows path traversal and remote code execution. Now you can tell McSkidy that Grinch Enterprises used this vulnerability. What is the CVE number of the vulnerability that was solved in version 2.4.51?
A.) CVE-2021-42013
Process:- Run the nmap command and
Q.) You are putting the pieces together and have a good idea of how your web server was exploited. McSkidy is suspicious that the attacker might have installed a backdoor. She asks you to check if there is some service listening on an uncommon port, i.e. outside the 1000 common ports that Nmap scans by default. She explains that adding -p1-65535 or -p- will scan all 65,535 TCP ports instead of only scanning the 1000 most common ports. What is the port number that appeared in the results now?
A.) 20212
Process:- Run the nmap code below to check for all ports.
nmap -p- -T4 10.10.219.54This scanning will take too much time.
You can run the command below to get the output quickly.
nmap -p20000-21000 -T4 -sV 10.10.219.54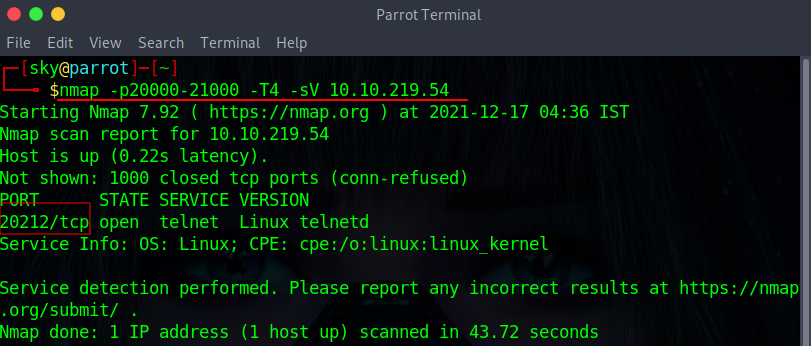
Q.) What is the name of the program listening on the newly discovered port?
A.) telnetd
Process:- As you can see in the previous nmap output, It's running telnetd.
Thanks for reading.
Have a happy day :-)

'CTFs > TryHackMe' 카테고리의 다른 글
| [Day 12] Advent of Cyber 3 (2021) | TryHackMe (0) | 2021.12.24 |
|---|---|
| [Day 11] Advent of Cyber 3 (2021) | TryHackMe (0) | 2021.12.22 |
| [Day 9] Advent of Cyber 3 (2021) | TryHackMe (0) | 2021.12.17 |
| [Day 8] Advent of Cyber 3 (2021) | TryHackMe (0) | 2021.12.17 |
| [Day 7] Advent of Cyber 3 (2021) | TryHackMe (0) | 2021.12.16 |




