| 일 | 월 | 화 | 수 | 목 | 금 | 토 |
|---|---|---|---|---|---|---|
| 1 | 2 | 3 | 4 | 5 | ||
| 6 | 7 | 8 | 9 | 10 | 11 | 12 |
| 13 | 14 | 15 | 16 | 17 | 18 | 19 |
| 20 | 21 | 22 | 23 | 24 | 25 | 26 |
| 27 | 28 | 29 | 30 |
- ctf
- Intruder
- burp suite
- Burp Suite: Intruder
- Windows Forensics 1
- CTFS
- TryHackMe
- advent of cyber 3
- Burp Suite: Other Modules
- Walkthrough
- Today
- Total
root@sky:~#
[Day 2] Advent of Cyber 3 (2021) | TryHackMe 본문


Web Exploitation
Elf HR Problems
Story
McSkidy needs to check if any other employee elves have left/been affected by the Grinch Industries attack, but the systems that hold the employee information have been hacked. Can you hack them back to determine if the other teams in the Best Festival Company have been affected?
Learning Objectives
- Understanding the underlying technology of web servers and how the web communicates.
- Understand what cookies are and their purpose.
- Learn how to manipulate and manage cookies for malicious use.
Answer the questions below
Q.) What is the name of the new cookie that was created for your account?
A.) user-auth
Process:- Today, I am using Windows OS. Open the static site in a new tab,

Press
CTRL+SHIFT+I to open developer mode and open the Application tab and keep watching the cookies.

Now, go for signup and create an account and you'll see a new cookie will generate,
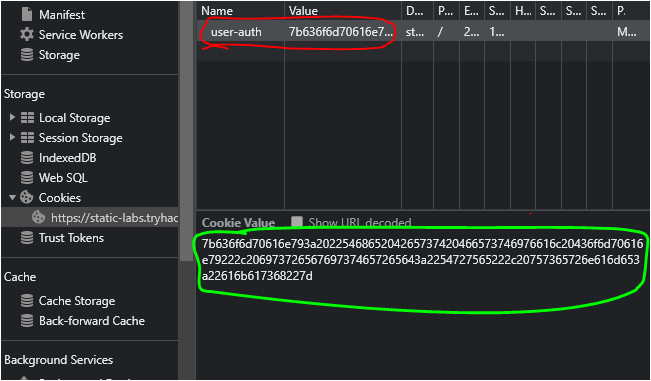
the name of the new cookie.
Q.) What encoding type was used for the cookie value?
A.) hexadecimal
Process:- You can analyze this hash on some hash analyzer website or tool but, I identified this through its pattern, you can see that this hash has 0-9 digits and a-f alphabets. Total 16 characters and it has no extra symbols. So, I think its pattern indicates hexadecimal.
I tried it and Yes It's right.
Q.) W hat object format is the data of the cookie stored in?
A.) JSON
Process:- I decoded this cookie through a website ( https://hashes.com/en/decrypt/hash ) and I got that It's a JSON format.
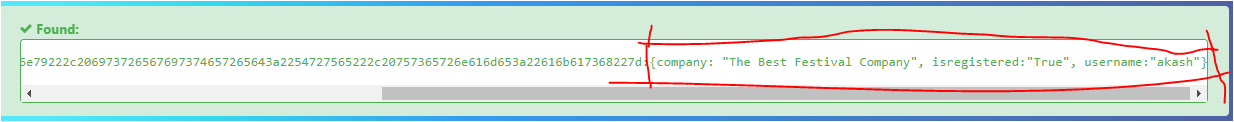
Q.) What is the value of the administrator cookie? (username = admin)
A.) 7bXXXXXXX_I_CAN'T_GIVE_FULL_HASH_ XXXXXXX 7d
Process:- I changed the JSON data, username akash to admin and encoded it to hexadecimal through this website ( https://codebeautify.org/string-hex-converter ).
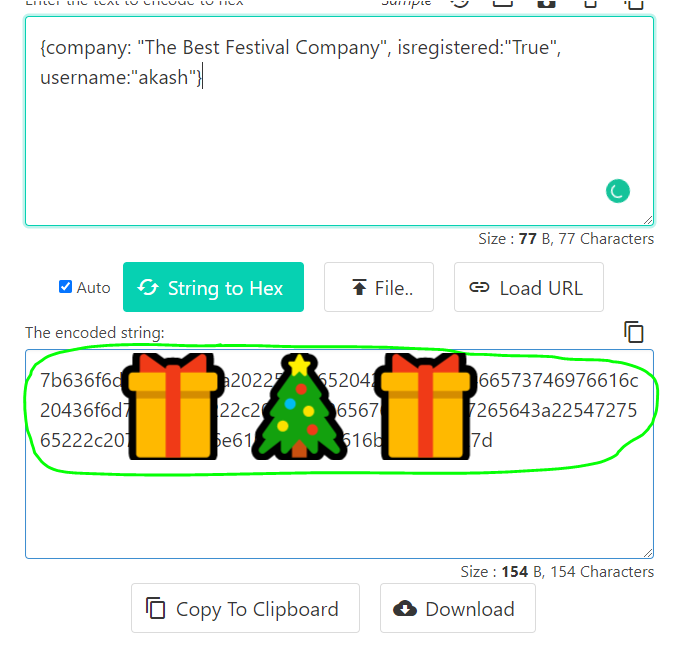
for both encoding and decoding.
Q.) What team environment is not responding?
A.) HR
Process:- Now, I changed the cookie with the admin's cookie to the Best Festival Monitoring Login Page (where you got the cookie) and, and refreshed the page by pressing CTRL+SHIFT+R and I got a "Best Festival Monitoring Dashboard".
Here, I saw that the HR team has red status means they are not responding.
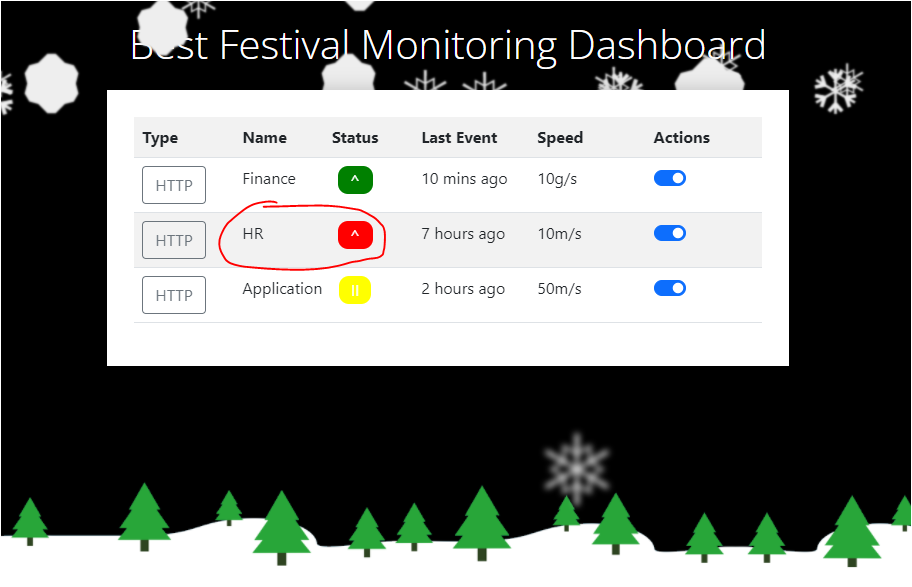
Q.) W hat team environment has a network warning?
A.) Application
Process:- As you can see, the "Application" team has a warning.
Thanks for reading.Have a lovely day :-)

'CTFs > TryHackMe' 카테고리의 다른 글
| [Day 4] Advent of Cyber 3 (2021) | TryHackMe (0) | 2021.12.06 |
|---|---|
| [Day 3] Advent of Cyber 3 (2021) | TryHackMe (0) | 2021.12.06 |
| [Day 1] Advent of Cyber 3 (2021) | TryHackMe (0) | 2021.12.03 |
| Pickle Rick | TryHackMe Walkthrough (0) | 2021.12.01 |
| TryHackMe | Jr Penetration Tester Write-up | Walking An Application (0) | 2021.11.07 |





