| 일 | 월 | 화 | 수 | 목 | 금 | 토 |
|---|---|---|---|---|---|---|
| 1 | 2 | 3 | 4 | 5 | ||
| 6 | 7 | 8 | 9 | 10 | 11 | 12 |
| 13 | 14 | 15 | 16 | 17 | 18 | 19 |
| 20 | 21 | 22 | 23 | 24 | 25 | 26 |
| 27 | 28 | 29 | 30 |
- Intruder
- burp suite
- Windows Forensics 1
- Walkthrough
- CTFS
- TryHackMe
- ctf
- advent of cyber 3
- Burp Suite: Other Modules
- Burp Suite: Intruder
- Today
- Total
root@sky:~#
[Day 3] Advent of Cyber 3 (2021) | TryHackMe 본문


Web Exploitation
Christmas Blackout
Story
Grinch Enterprises have also tried to block communication between anyone at the company. They've locked everyone out of their email systems and McSysAdmin has also lost access to their admin panel. Can you find the admin panel and help restore communication for the Best Festival Company.
Learning Objectives
In today's task, we're going to be using our investigatory skills and techniques to discover un-listed content, and attempt some common authentication using the clues around us.

Answer the questions below
Q.) Using a common wordlist for discovering content, enumerate http://10.10.144.223 to find the location of the administrator dashboard. What is the name of the folder?
A.) admin
Process:- I used gobuster to brute-force web directory with "/usr/share/wordlists/dirb/common.txt" wordlist and I found an admin login page in http://10.10.144.223/admin.

Q.) In your web browser, try some default credentials on the newly discovered login form for the "administrator" user. What is the password?
A.) administrator
Process:- I tried some default passwords and I logged in with the password " administrator ".
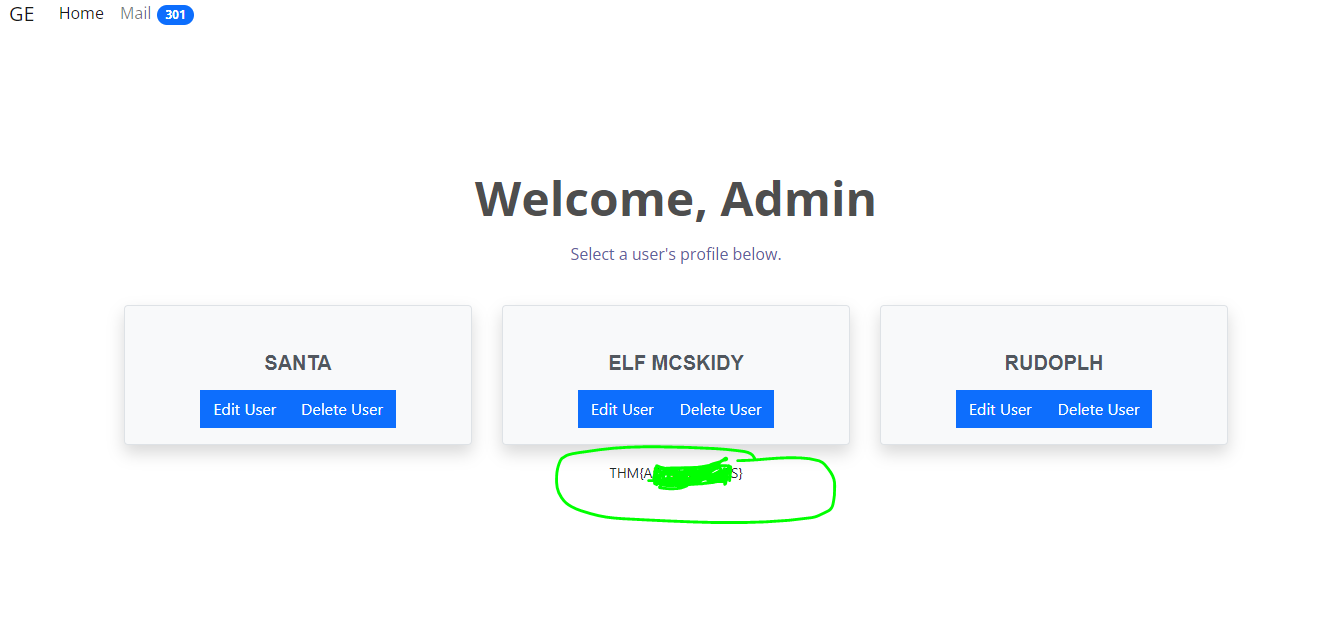
Q.) Access the admin panel. What is the value of the flag?
A.) THM{AXXXXXXXXXS}
Process:- I accessed the admin panel and I got the flag.
Thanks for reading.
Have a lovely day :-)

'CTFs > TryHackMe' 카테고리의 다른 글
| [Day 5] Advent of Cyber 3 (2021) | TryHackMe (0) | 2021.12.07 |
|---|---|
| [Day 4] Advent of Cyber 3 (2021) | TryHackMe (0) | 2021.12.06 |
| [Day 2] Advent of Cyber 3 (2021) | TryHackMe (0) | 2021.12.03 |
| [Day 1] Advent of Cyber 3 (2021) | TryHackMe (0) | 2021.12.03 |
| Pickle Rick | TryHackMe Walkthrough (0) | 2021.12.01 |




