[Day 5] Advent of Cyber 3 (2021) | TryHackMe


Web Exploitation
Pesky Elf Forum
Story
The Elf Forum is where all the elves express their joy and excitement about Christmas, but Grinch Enterprises has one bad admin account, and they've installed a plugin that changes all mentions of Christmas to Buttmas!! McSkidy needs to find that admin account and disable the plugin.
Learning Objectives
In today's task, we're going to learn the following.
- Understanding authentication and where it is used
- Understanding what fuzzing is
- Understanding what Burp Suite is and how we can use it for fuzzing a login form to gain access
- Apply this knowledge to retrieve Santa's travel itinerary

Answer the questions below
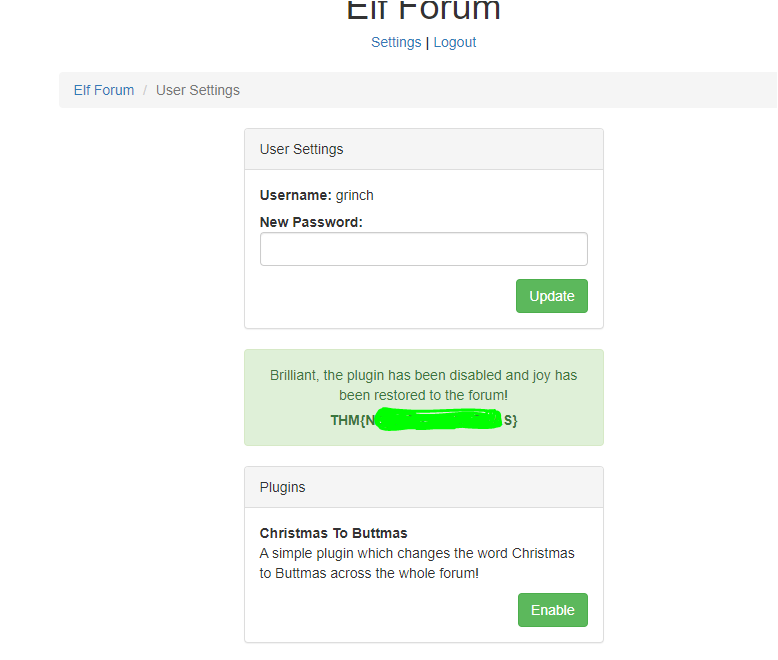
Q.) What flag did you get when you disabled the plugin?
A.) THM{NXXXXXXXXXXXXS}
Process:- Here I have McSkidy's account credentials and I have to change grinch's password using Cross-Site Scripting(XSS).
Let's solve it :-)
First of all, start the machine and visit the site ( in my case it's https://10-10-69-131.p.thmlabs.com/ )

Login to McSkidy's account Username: McSkidy and Password: password

I logged in and I got an option setting. Let's visit it.

Here is an option to change McSkidy's password. Let's change it.
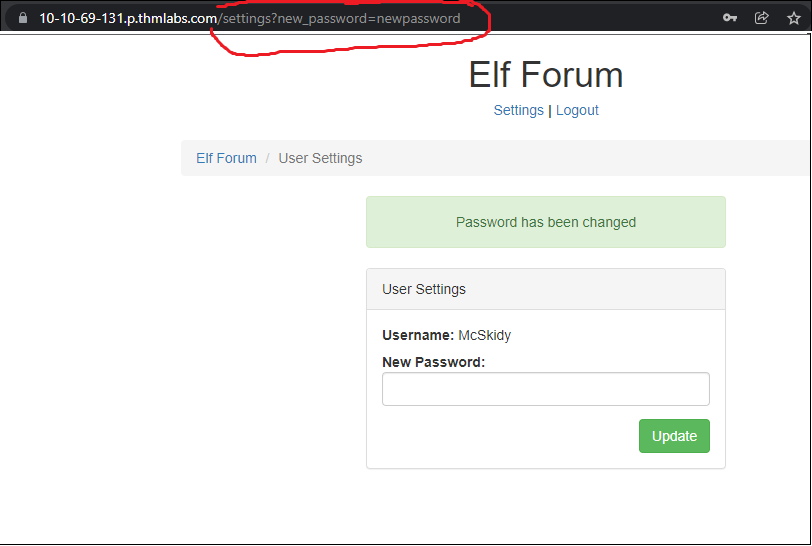
I changed the password and I noticed that It made a request to a specified URL to change the password so, If grinch will make a request to the URL his password will be changed.
Go back to the Elf Form and open the grinch's post.
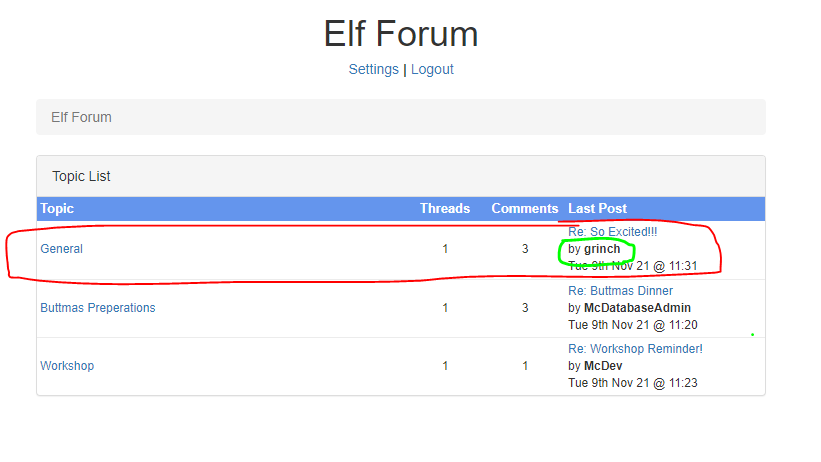
I sent this script in the grinch's comment box to change grinch's password to "newpass".
<script>fetch('/settings?new_password=newpass');</script>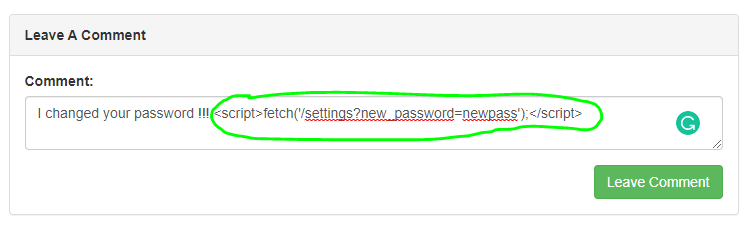
I sent the comment.
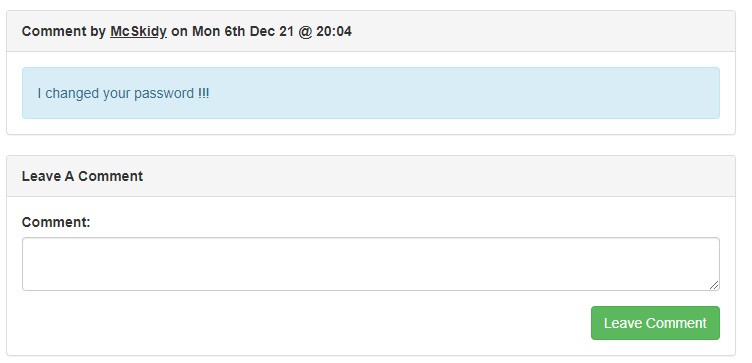
Let's log out the McSkidy's account and check if grinch's password has been changed.
Yes, I can log in to the grinch's account.
Now, go to setting and disable Christmas To Buttmas plugin to get the flag.
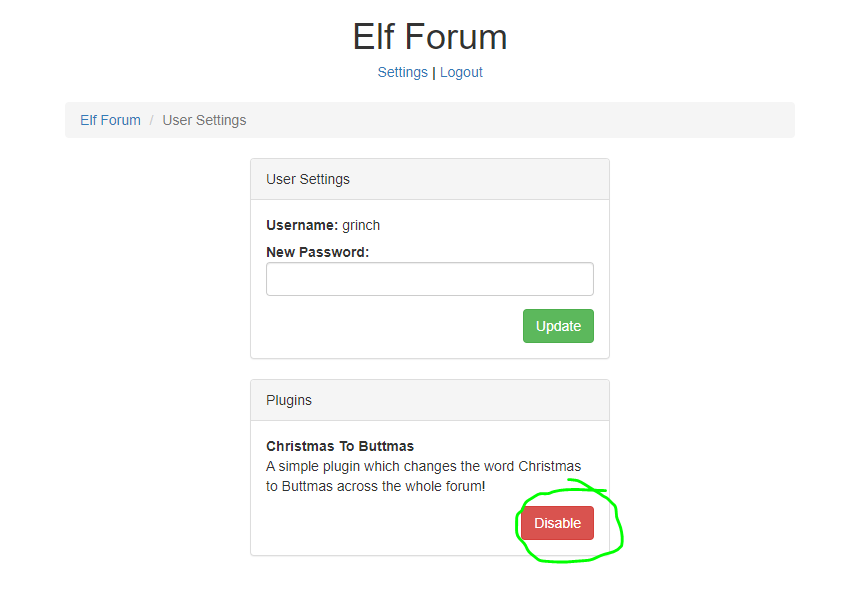
And I got the flag :-)
Thanks for reading.
Have a lovely day :-)

