[Day 12] Advent of Cyber 3 (2021) | TryHackMe


Networking
Sharing Without Caring
Story
Grinch Enterprises has been leaving traces of how their hackers have been accessing data from the system - you've found a unique server they use. We need your help to find out what method they've been using to extract any data.

Answer the questions below
Q.) Scan the target server with the IP 10.10.74.115 . Remember that MS Windows hosts block pings by default, so we need to add -Pn , for example, nmap -Pn 10.10.74.115 for the scan to work correctly.How many TCP ports are open?
A.) 7
Process:- Start the machine and do a nmap scan.
nmap -Pn 10.10.74.115
Q.) In the scan results you received earlier, you should be able to spot NFS or mountd, depending on whether you used the -sV option with Nmap or not. Which port is detected by Nmap as NFS or using the mountd service?
A.) 2049
Process:- In the nmap result, you can see that port 2049 is using NFS service.
Q.) How many shares did you find?
A.) 4
Process:- Run the following command to see how many shares are available.
showmount -e 10.10.74.115
If you are getting error "
bash: showmount: command not found
", run the following command to fix it.
sudo apt install rpcbind nfs-common
Q.) How many shares show “everyone”?
A.) 4
Process:- Here is 3 shares for everyone.

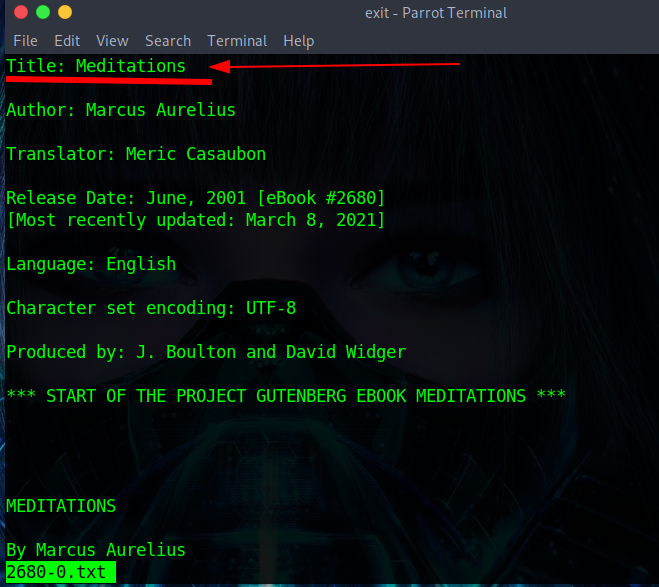
Q.) What is the title of file 2680-0.txt?
A.) Meditations
Process:- To see, what is inside these folders, create 4 folders (with any name). I am gonna create 4 folders with the same name.
mkdir AoC12 && cd AoC12 && mkdir share admin-files my-notes confidentialNow, run the following commands to mount the shared folders to your folders.
export MACHINE_IP=10.10.74.115
sudo mount $MACHINE_IP:/confidential confidential
sudo mount $MACHINE_IP:/share share
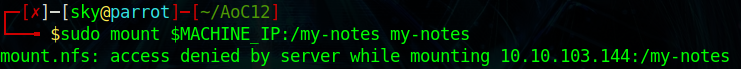
sudo mount $MACHINE_IP:/my-notes my-notes
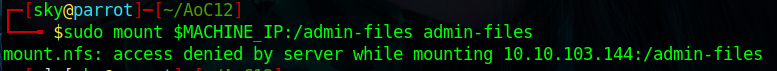
sudo mount $MACHINE_IP:/admin-files admin-filesAs you can see that we don't have permission to mount my-notes and admin-files.
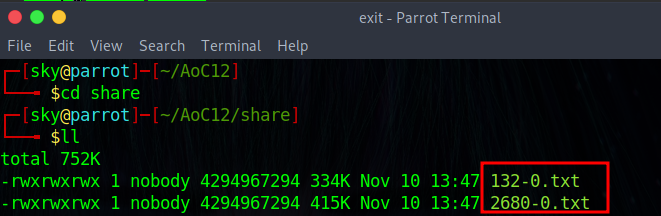
2680-0.txt
file so, let's read it. Because It's a big text file I'm gonna use the "less" command instead of "cat".
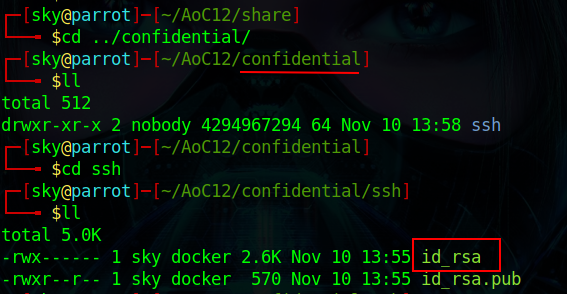
Q.) It
seems that Grinch Enterprises has forgotten their SSH keys on our system. One of the shares contains a private key used for SSH authentication (
id_rsa
).
What is the name of the share?
A.) confidential
Process:- I got the id_rsa file in confidential share.
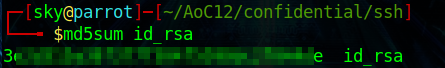
Q.) We can calculate the MD5 sum of a file using md5sum FILENAME . What is the MD5 sum of id_rsa ?
A.) 3XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXe
Process:- To calculate the MD5 of id_rsa, run the following command,
Thanks for reading.
Have a happy day :-)

